DDoS attack detection method based on SDN
An attack detection and purpose technology, applied in the field of software-defined network, can solve the problems that are difficult to be precise and large in number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1: a kind of DDoS attack detection method based on SDN, comprises the following steps:
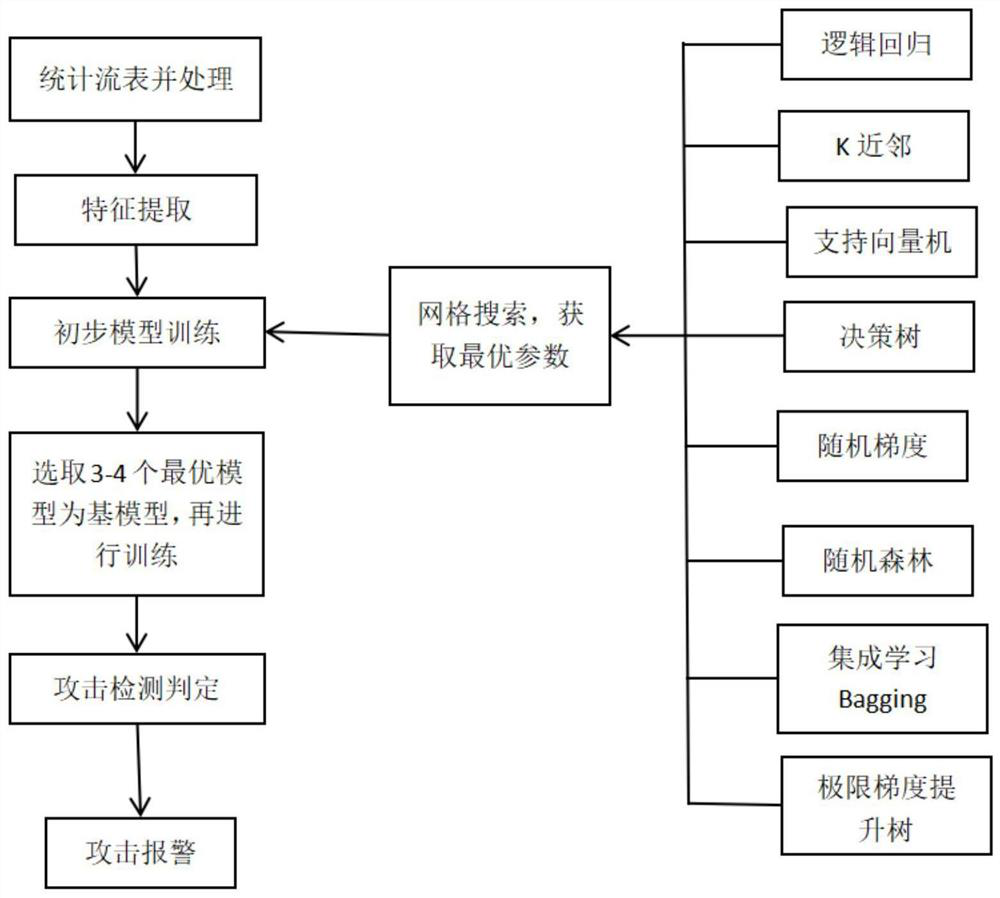
[0053] 1) Count the flow entries in the SDN and preprocess them.
[0054] 2) Feature extraction.
[0055] 3) Preliminary model training.
[0056]4) Select 3-4 optimal models as the base model, and then train.
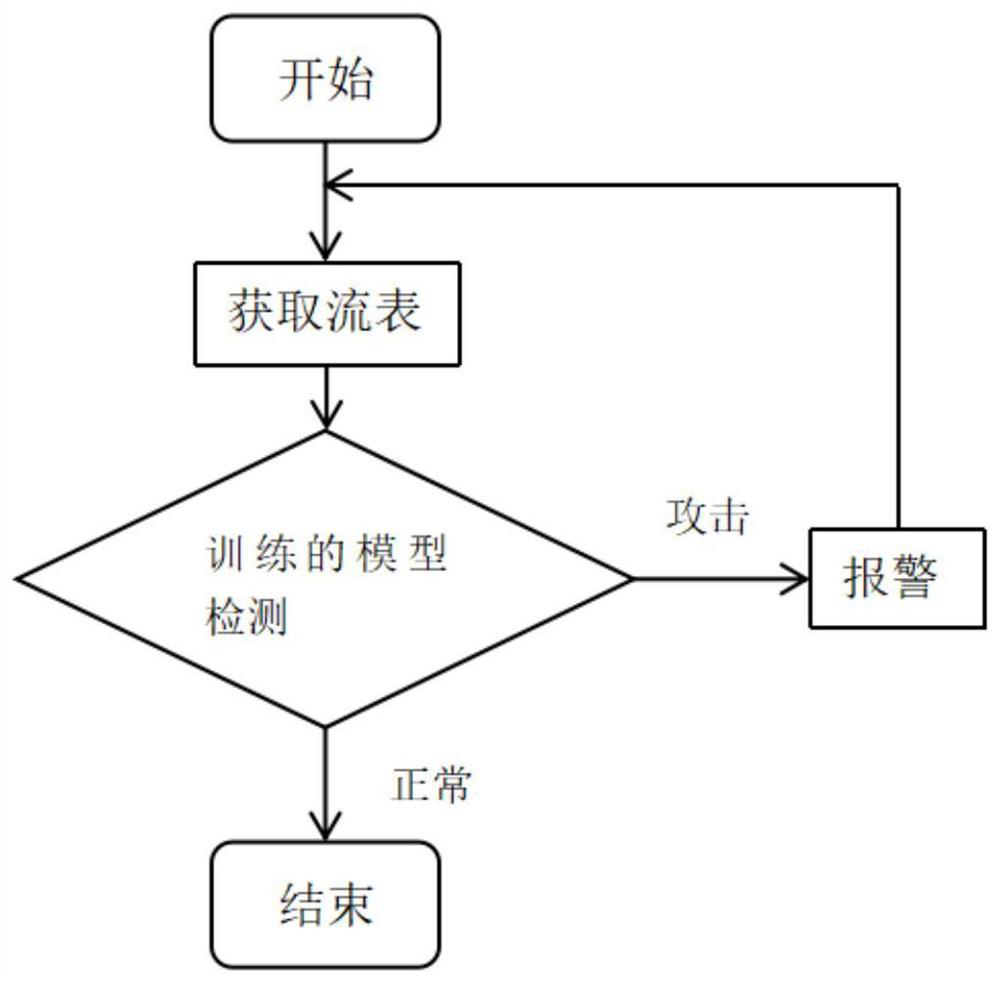
[0057] 5) Attack detection and judgment.
[0058] Further, said step 1) includes the following steps:
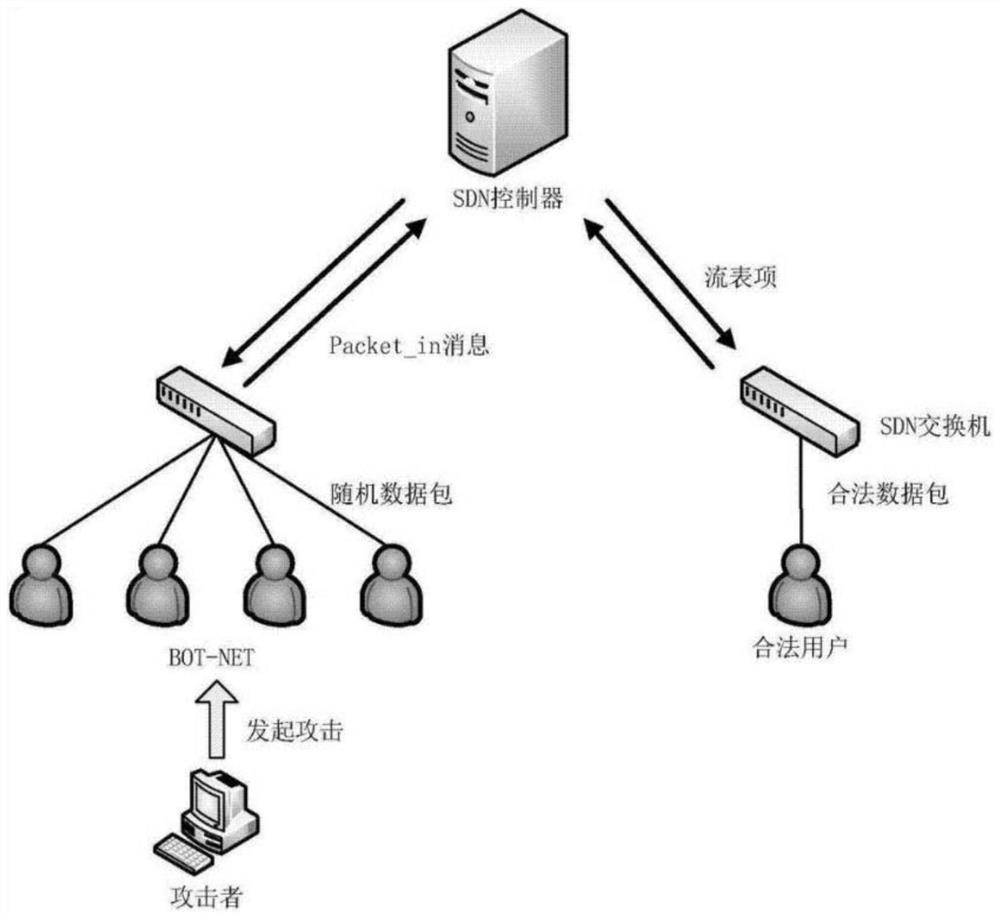
[0059] Count the matching field and counter information in the flow entry, protocol, srcIP, dstIP, srcPort, dstPort, pCount represent the matching protocol type, source address, destination address, source port, destination port, and the number of data packets of the flow entry in turn. Assuming that the OpenFlow switch is extracted with a cycle T, the total number of different flow entries is N, and the set is flowSet={(protocol,srcIPi,dstIP,srcPorti,dstPort,pCount,i=l,2,...N }, the DDoS attack detection algorithm needs to periodically extract the flow entry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com