Application deployment method and device
A technology of application deployment and automatic deployment, which is applied in the field of deployment applications, can solve problems such as error-prone and low efficiency, and achieve the effect of improving efficiency and success rate, simple logic, and avoiding low efficiency and success rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
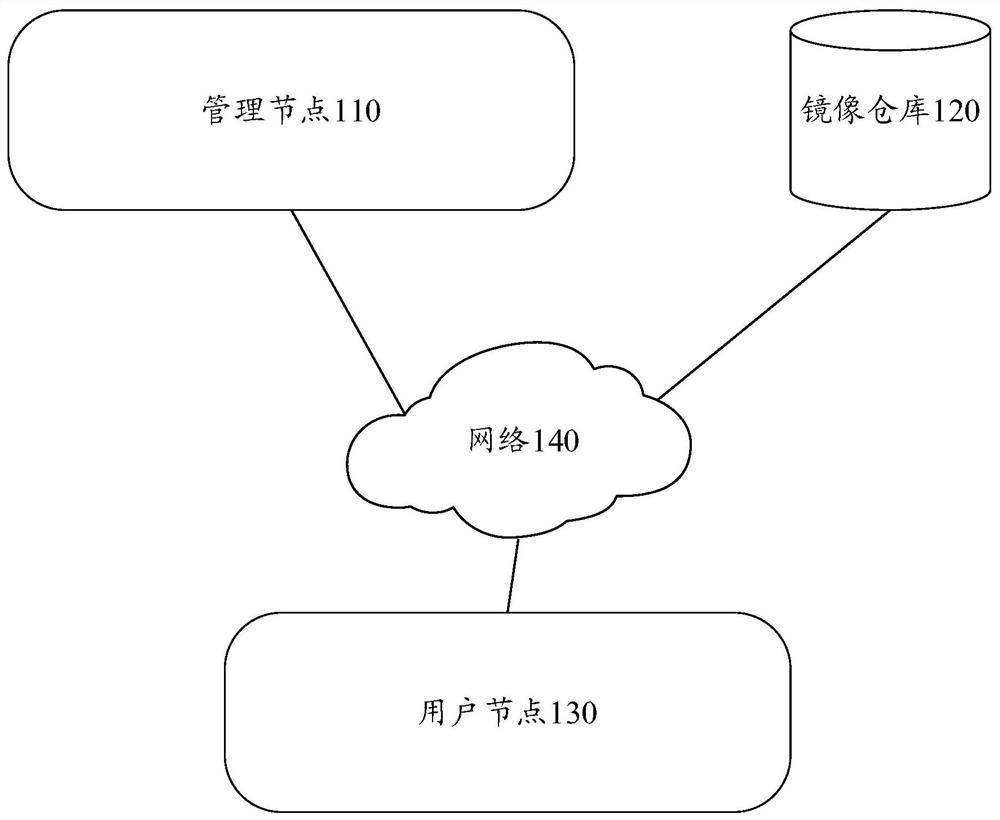
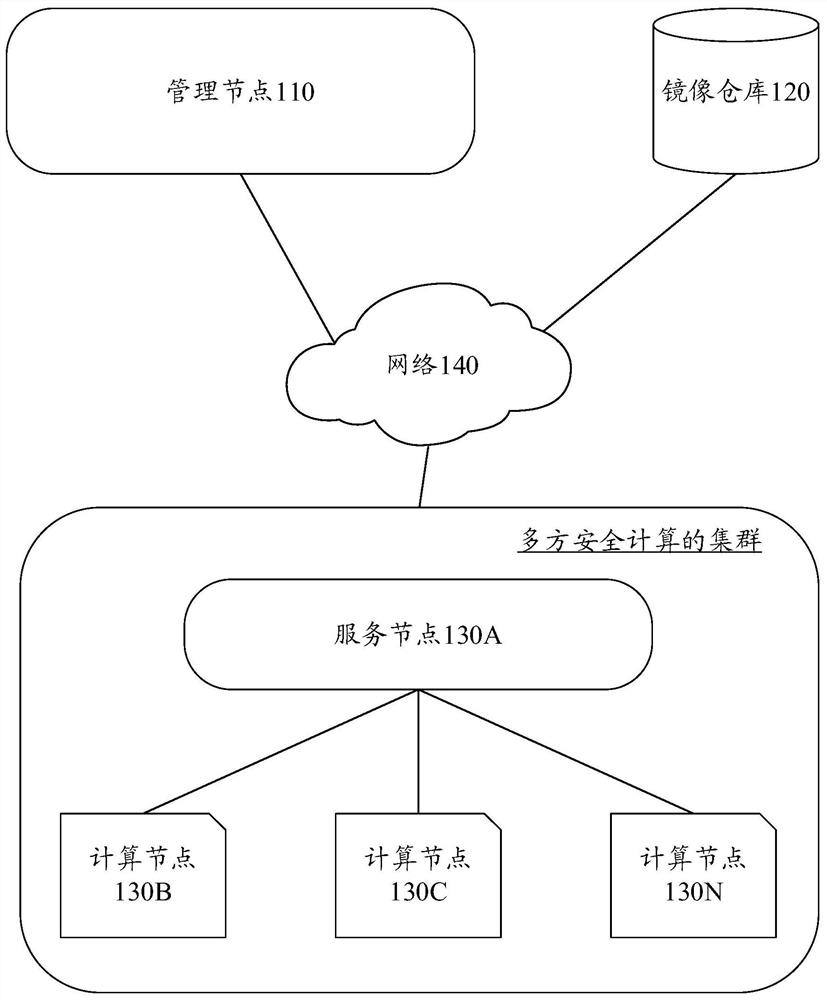
[0054] Figure 4 is a schematic flowchart of a method for deploying an application provided by an embodiment of the present disclosure. Figure 4 The method is executed by user nodes and management nodes. The user node may be, for example, the user node 130 described above. The management node may be, for example, the management node 110 described above. The user node can be an independent user node, or a certain node in the cluster. When the user node 130 is a certain node in the cluster, the user node 130 may be a master node in the cluster, or a slave node in the cluster. For example, a user node is a service node that provides multi-party secure computing services or a computing node that participates in multi-party secure computing.
[0055] In step S402, the user node receives a deployment token. The deployment token may be a token allocated by the management node to the user node or authorized to be used by the user.
[0056] There are many ways for user nodes to ...
Embodiment 2
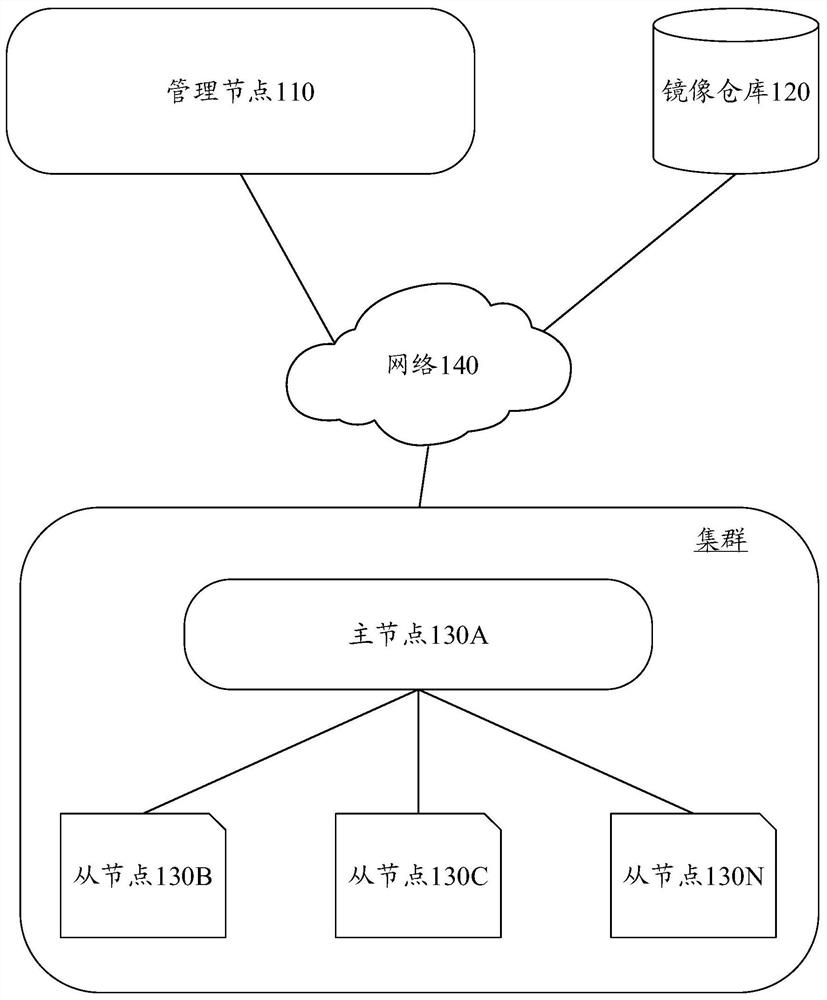
[0075] Embodiment 2 describes how to implement application deployment on a cluster according to an embodiment of the present disclosure. It should be noted that the second embodiment describes in detail how the slave nodes perform application deployment on the premise that the master node of the cluster has completed the application deployment. The master node can deploy applications in advance according to the application deployment method provided in Embodiment 1. It should also be noted that what is described in Embodiment 1 is a general application deployment method, which can be applied to both the application deployment of the master node in Embodiment 2 and the application deployment of the slave nodes in Embodiment 2 .
[0076] Such as Figure 7 As shown, in step S702, the master node sends a second request to the management node. The second request may be used to request the management node to allocate a deployment token to the slave nodes of the cluster (for the i...
Embodiment 3
[0082] Embodiment 3 provides an example of the manner in which the management node generates the application deployment file. It should be understood that the third embodiment may be applied to any of the aforementioned embodiments. For example, before step S408 in the first embodiment or before step S714 in the second embodiment, the application deployment file may be generated based on the third embodiment. Embodiment 3 is described in detail below.
[0083] Before the management node sends the application deployment file to the user node, it needs to obtain the application deployment file first. Traditional application deployment files are generated by operation and maintenance personnel by manually entering codes. For example, the operation and maintenance personnel need to determine with the user in advance the version of the application that the user expects to deploy. For an application that supports multiple application modules (that is, a multi-container applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com