A high-performance data multi-level encryption and decryption method and system based on fully homomorphic encryption
A homomorphic encryption and encrypted data technology, applied in the field of information security, can solve problems such as slow execution speed, high overhead, and inability to dynamically adjust, and achieve high processing speed and storage efficiency, small footprint, and fast encryption and decryption processing speed Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
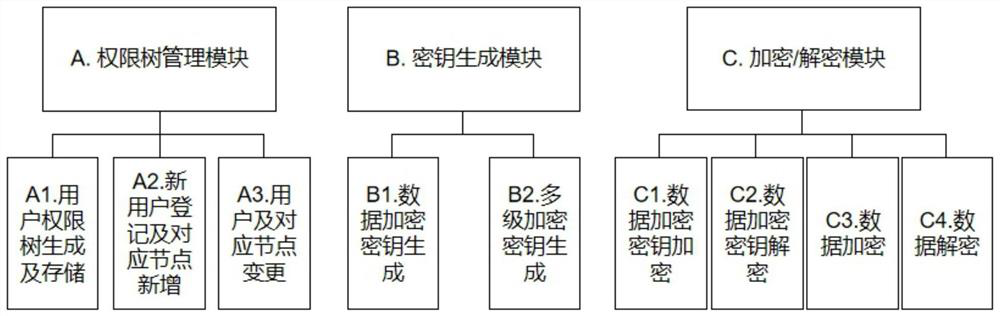
Method used
Image
Examples
Embodiment
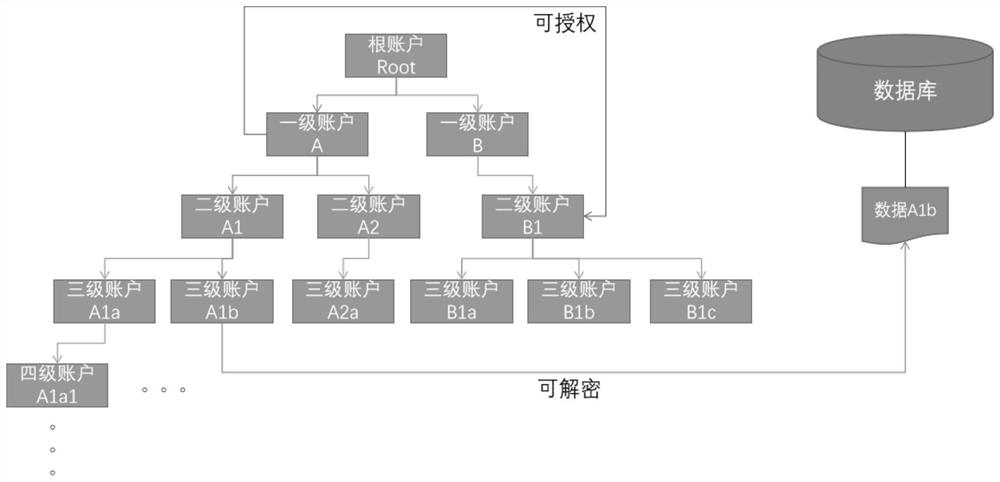
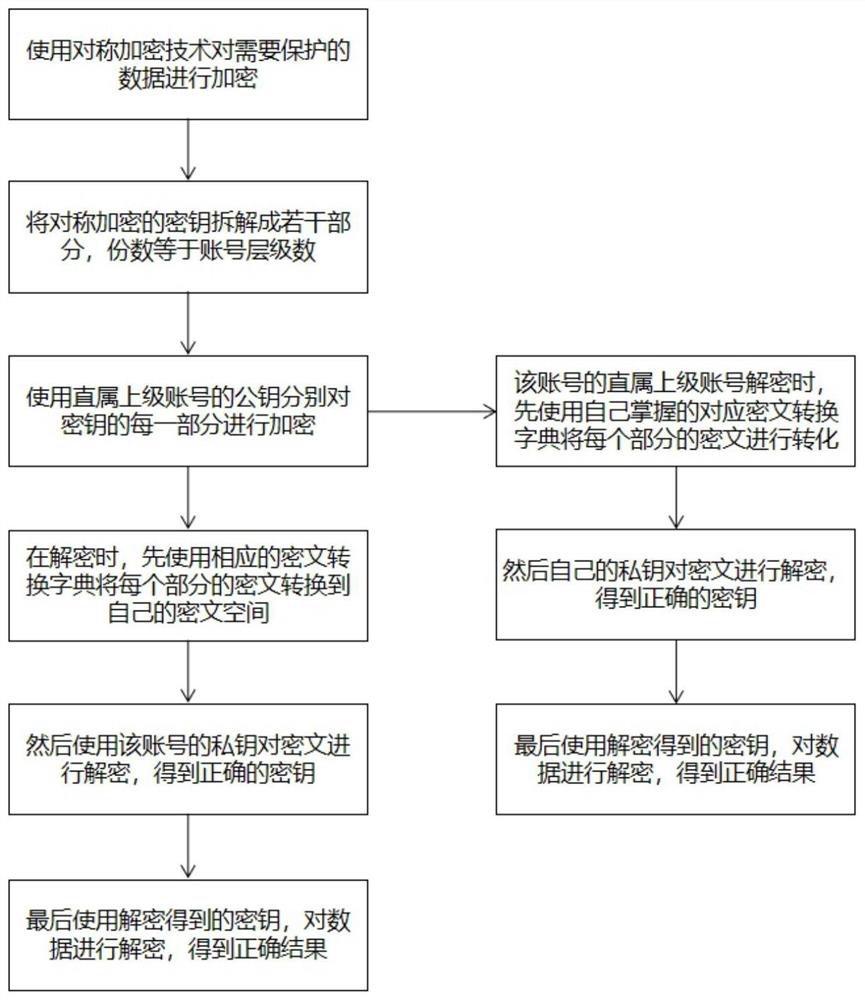
[0064] For the sake of convenience, this embodiment uses the simplest summation and disassembly scheme for description, taking three-level encryption as an example, where PK is the public key and SK is the private key. The specific operation steps are as follows:
[0065] A. The first level platform provides centralized identity registration, key generation, key distribution services, and initializes a pair of public and private keys SK pub and PK pub As a public ciphertext space (S pub ) key;
[0066] B. After the secondary account A completes the registration, the central platform generates the corresponding public-private key pair SK A and PK A , and send the PK pub and the conversion dictionary (T pub=>A ) to A, who holds the conversion dictionary (T A=>pub );
[0067] C. After the registration of the third-level account A1 (organization) under the second-level account is completed, the central platform generates the corresponding public-private key pair SK A1 and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com