Anti-counterfeiting encryption verification method and system for electric power data
A technology of power data and verification method, which is applied in the direction of digital transmission system, transmission system, digital data protection, etc., and can solve problems such as malicious operation of power commands
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
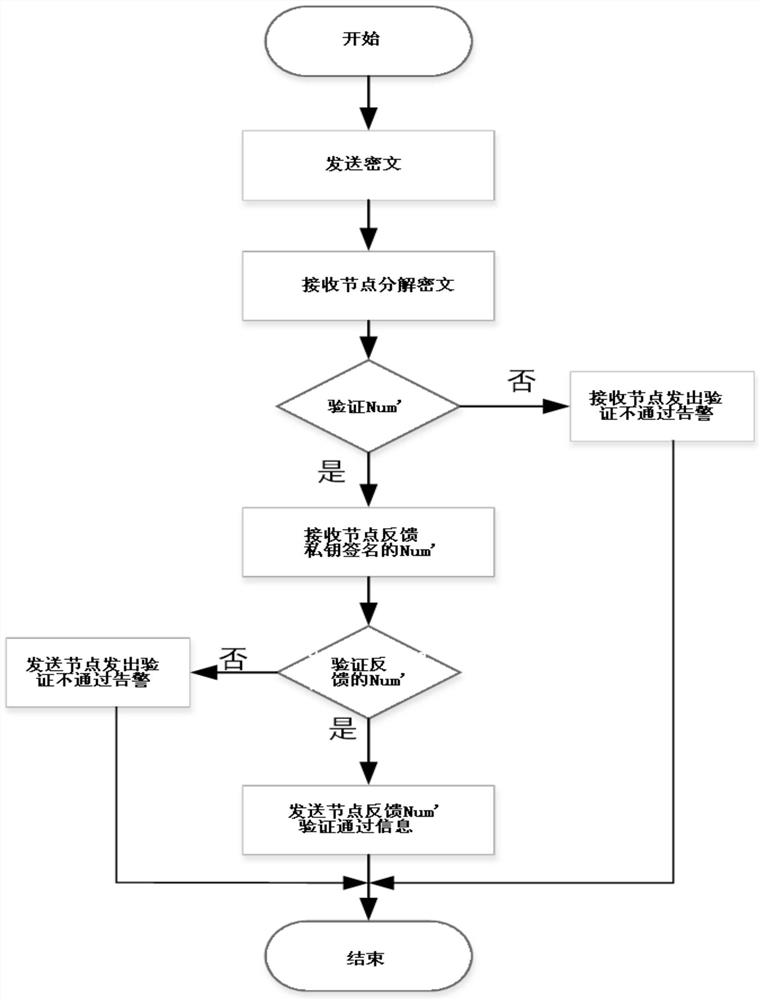
[0051] Such as figure 1 As shown, a power data anti-forgery encryption verification method includes a method on the sending node side and a method on the receiving node side, specifically as follows:
[0052] The method on the sending node side includes the following steps:
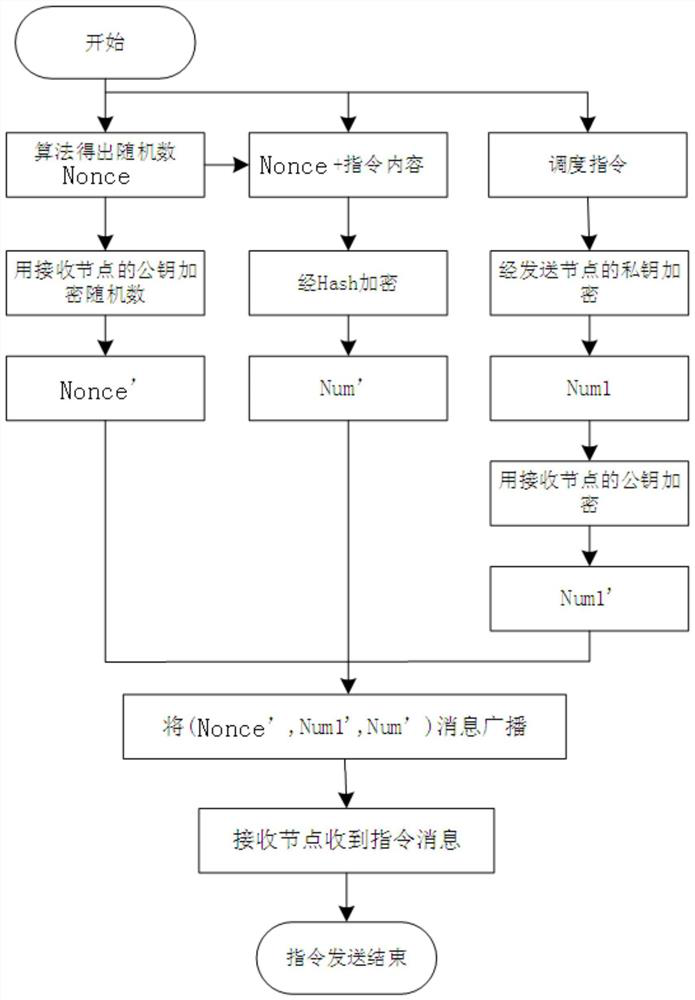
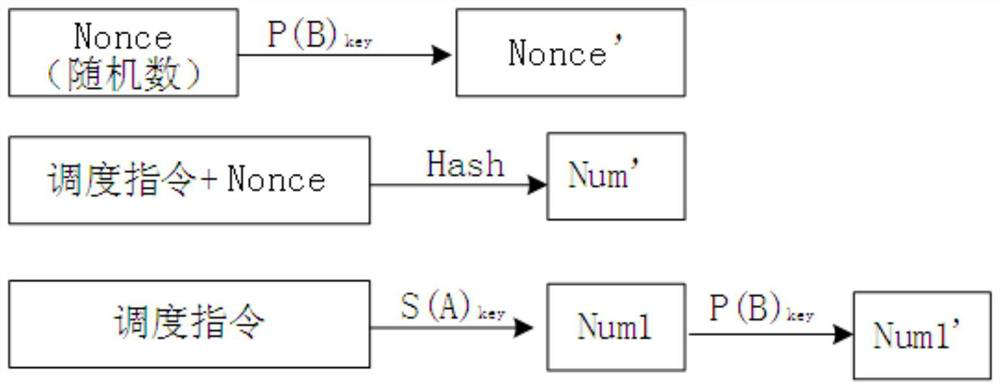
[0053] 11) Use the random number generation algorithm to generate the random number Nonce on the blockchain system application platform, and use the receiving node public key P(B) key Encrypt the random number Nonce to obtain the ciphertext Nonce'.
[0054] 12) Combining the random number Nonce with an instruction (specifically a scheduling instruction), and using a one-way encryption algorithm to encrypt the combination...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com