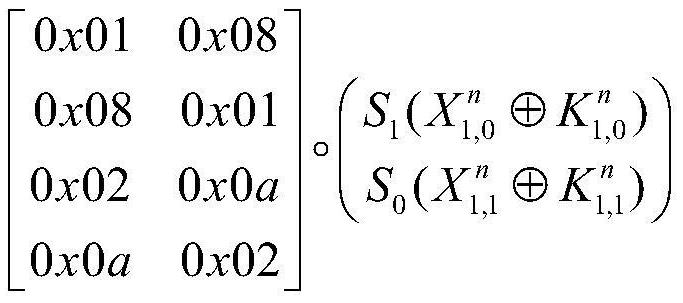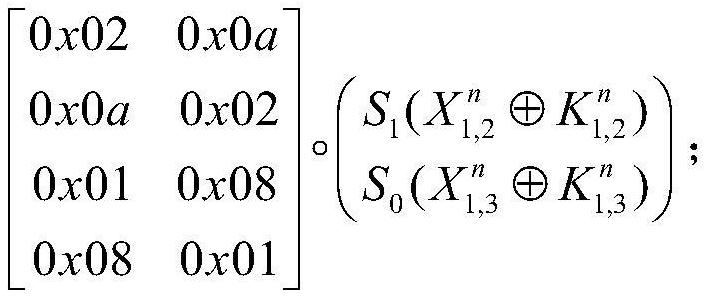Software tampering detection method based on white box CLEFIA encryption method
An encryption method and tamper detection technology, applied to electrical components and key distribution, can solve the problem of small size of detection software
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
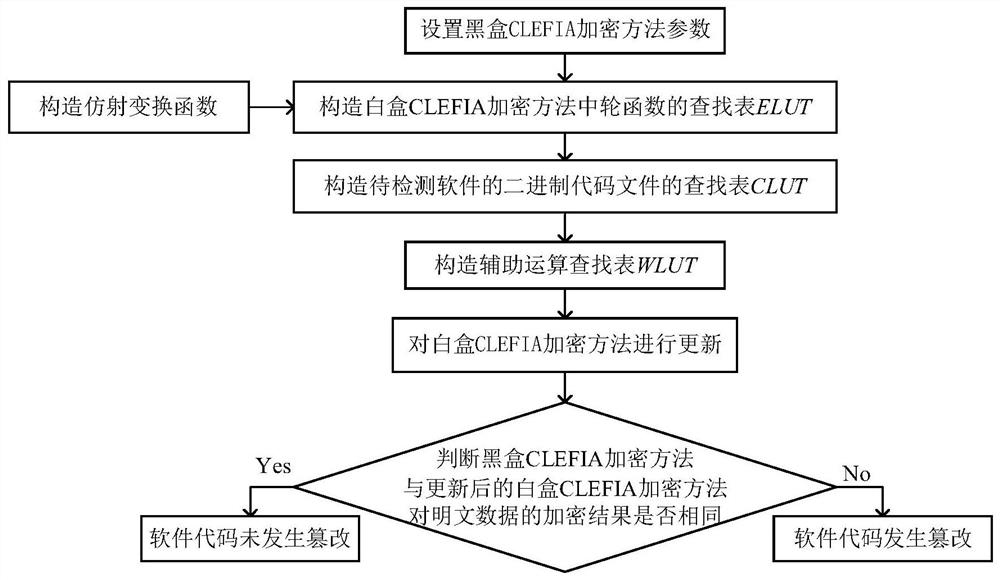
[0044] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
[0045] Step 1) Set the black box CLEFIA encryption method parameters:
[0046] Let the whitening key of the black-box CLEFIA encryption method be WK 1 、WK 2 、WK 3 and WK 4 , the CLEFIA encryption method includes N rounds of iterations, and the round function of the nth round of iterations is with WK 1 and WK 2 Before the first round of iteration, WK 3 and WK 4 After the last round of iterations, where N=18, with Respectively with input, and with The size of the finite field GF(2) 32 A randomly generated 32-bit vector on the with Respectively with The round key, WK 1 、WK 2 、WK 3 and WK 4 ,as well as with are 32 bits in size, with The expressions are respectively:
[0047]
[0048]
[0049]
[0050]
[0051] Among them, M 0 and M 1 respectively represent the 32×32 diffusion matrix defined ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com