A kind of exchange cipher watermark encryption, decryption method and system
A watermark encryption and cipher technology, applied in the field of information security, can solve problems affecting the availability of vector geographic data, redundant decryption steps, difficult to meet the security protection of vector geographic data, etc., achieve good imperceptibility and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
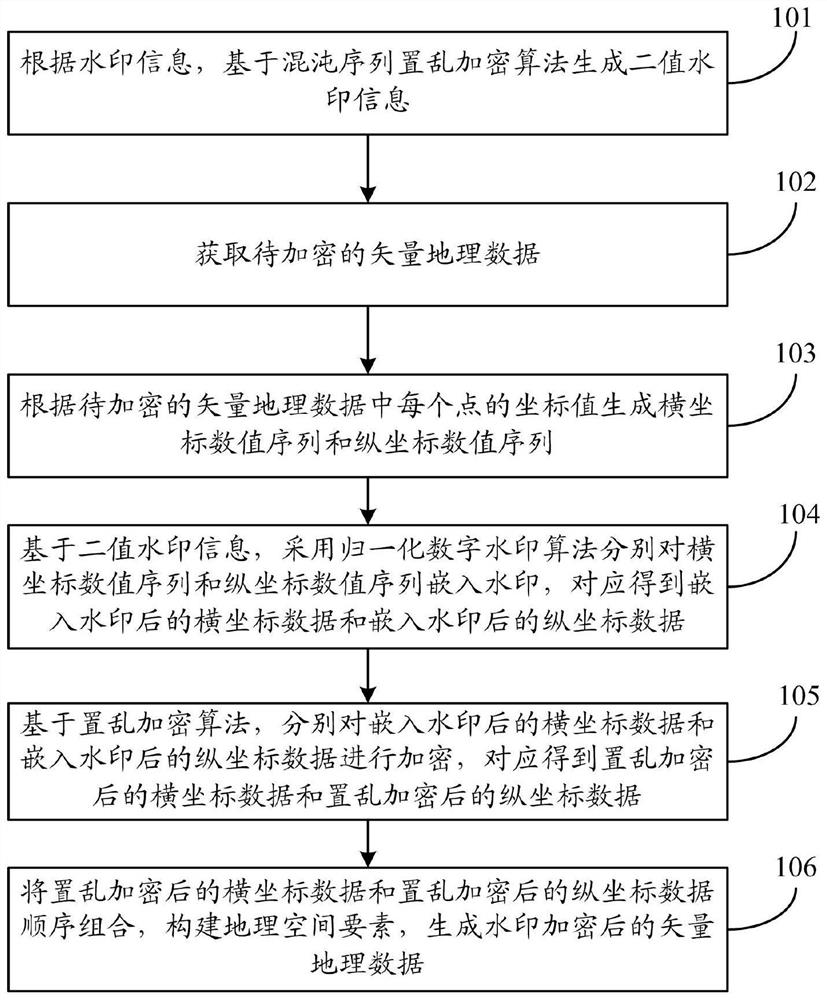
[0115] In this embodiment, a watermark is first embedded in the vector geographic data, and then scrambling and encryption are performed to obtain the vector geographic data encrypted by the watermark. figure 1 It is a schematic flowchart of Embodiment 1 of the present invention, such as figure 1 The specific process is as follows:
[0116] Step 101: Generate binary watermark information based on the chaotic sequence scrambling encryption algorithm according to the watermark information. Specifically: first, according to the watermark information, a binary sequence of the watermark information is generated according to the computer code; then, based on the iteration number N of the chaotic sequence, a chaotic sequence scrambling encryption algorithm is used to generate the scrambled binary watermark information {W n |n=1,2,...,n}, W i = 0 or 1, W i Represents binary watermark information W n The value of the ith element in .
[0117] Step 102: Obtain the vector geographic...
Embodiment 2
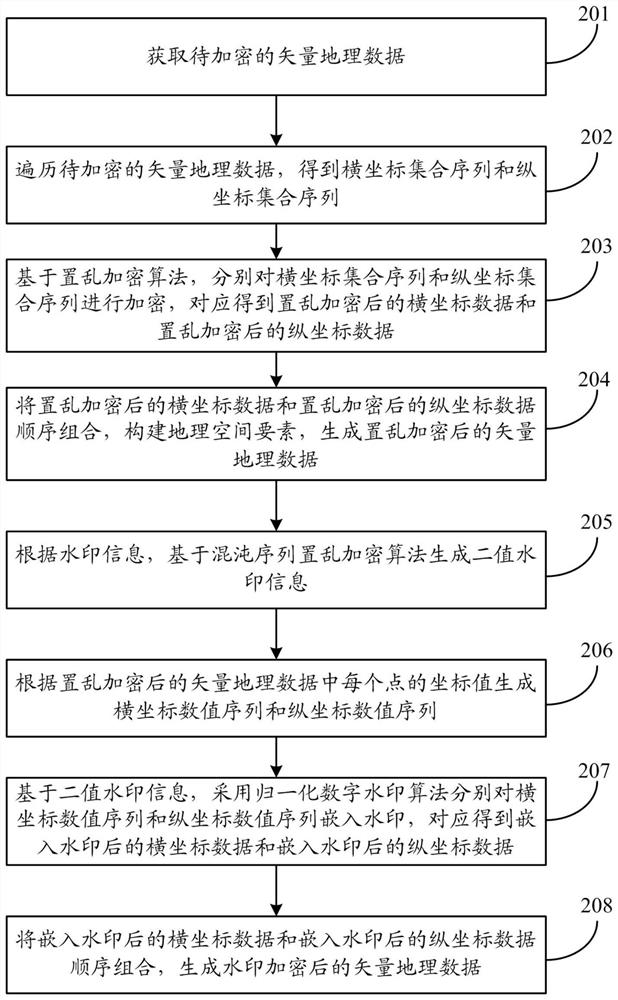
[0148] The difference from Embodiment 1 is that in this embodiment, vector geographic data is first scrambled and encrypted, and then a watermark is embedded in the encrypted vector geographic data, thereby obtaining watermark-encrypted vector geographic data. The same is that the methods used for watermark embedding and scrambling encryption are the same as those in Embodiment 1. figure 2 It is a schematic flowchart of Embodiment 2 of the present invention, such as figure 2 shown, including the following steps:
[0149] Step 201: Obtain vector geographic data to be encrypted.
[0150] Step 202: Traverse the vector geographic data to be encrypted to obtain abscissa set sequence and ordinate set sequence. Step 202-Step 203 is the random encryption process. This step is mainly to traverse the geographic coordinate set in the data to obtain the abscissa set sequence {PX n |n=1,2,...,N} and the ordinate set sequence {PY n |n=1, 2, . A sequence of ordinates of points.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com