Identity recognition method for illegal object based on illegal behavior recognition
An identity recognition and behavior technology, applied in the field of identity recognition, can solve the problems of too large face inclination angle, unable to further realize the face recognition of illegal personnel, unable to further carry out face recognition and so on.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
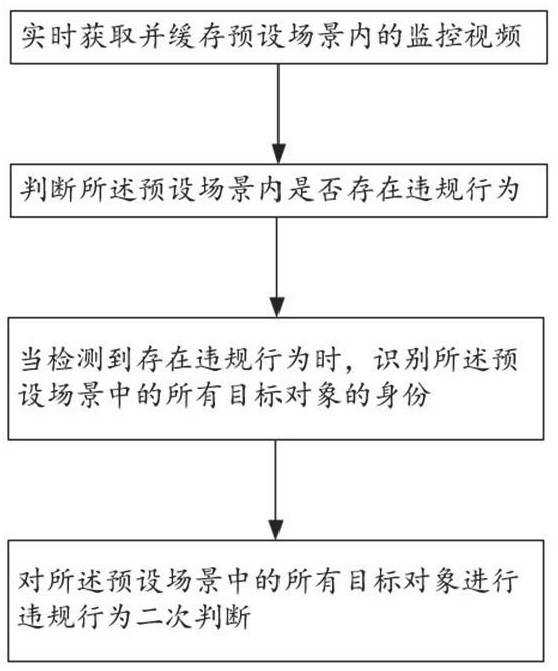
[0065] This embodiment provides a violation object identification method based on violation behavior identification, including:
[0066] S1: Obtain and cache in real time (real-time caching of historical 60s video clips of monitoring) the monitoring video in the preset scene (the corresponding scene within the monitoring range of the monitoring system);
[0067] S2: Determine whether there is a violation in the preset scene (such as not wearing a safety helmet, etc.);
[0068] S3: When a violation is detected, identify the identities of all target objects (people entering the preset scene) in the preset scene;
[0069] S4: Perform a second judgment on violations of all target objects in the preset scene.
[0070] In this embodiment, the violating object is: after a second judgment of the violating behavior, it is determined that the violating behavior has occurred.
[0071] In this embodiment, the present invention is mainly applied in construction work areas such as factori...
Embodiment 2
[0074] On the basis of the above-mentioned embodiment 1, this embodiment provides a violation object identification method based on violation behavior identification, S1: real-time acquisition and buffering of surveillance video in a preset scene, including:
[0075] Based on the monitoring system, the monitoring video in the preset scene is obtained in real time, and the historical video clips of the preset time period are cached in real time.
[0076] In this embodiment, the real-time caching of historical video clips for a preset time period refers to the real-time caching of historical 60s video clips for monitoring based on the current time point.
[0077] In this embodiment, the monitoring system is connected to the computer cloud terminal in the data center.
[0078] The beneficial effect of the above technical solution is: the monitoring system can transmit the monitoring video in the preset scene to the computer cloud terminal in the data center in real time, realize ...
Embodiment 3
[0080] On the basis of the above-mentioned embodiment 1, this embodiment provides the above-mentioned method for identifying the illegal object based on the identification of violations. S2: Before judging whether there is a violation in the preset scene, it includes:
[0081] extracting frames to be tested (that is, initially extracted frames for frame extraction detection) from the surveillance video according to a preset cycle;
[0082] Judging whether the target object exists in the frame to be tested, if so, obtaining the maximum brightness difference between the pixels contained in the frame to be tested (that is, the maximum brightness difference between all pixels in the frame to be tested) the maximum value of the luminance difference), the maximum gray value difference (that is, the maximum value of the gray value difference between all image points in the frame to be tested), the maximum chromaticity difference value (that is, the maximum value of the The maximum va...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com