Benign file list generation
A file list, benign technology, applied in the direction of platform integrity maintenance, user identity/authority verification, instruments, etc., can solve problems such as increase
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Specific non-limiting embodiments of the invention will now be described with reference to the accompanying drawings. It should be understood that specific features and aspects of any embodiment disclosed herein can be used and / or combined with specific features and aspects of any other embodiment disclosed herein. It should also be understood that these embodiments are exemplary, and merely describe a small number of embodiments within the scope of the invention. Various changes and modifications involved in the present invention, which are obvious to those skilled in the art, are deemed to be within the spirit, scope and intent of the present invention as further defined in the appended claims.
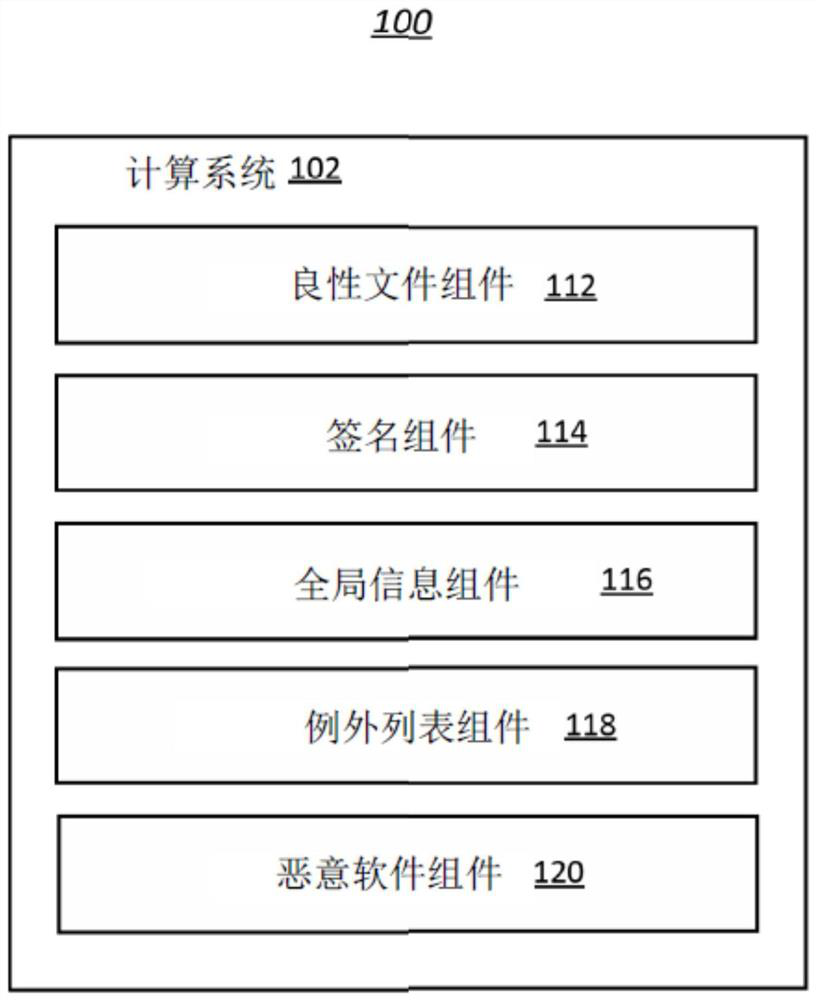
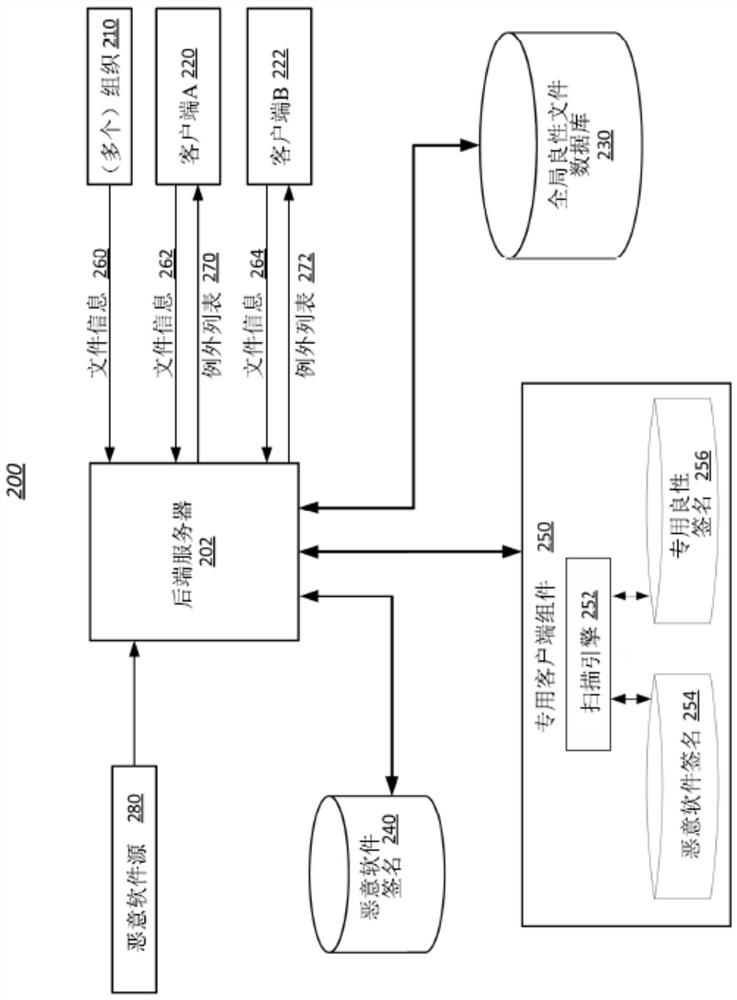
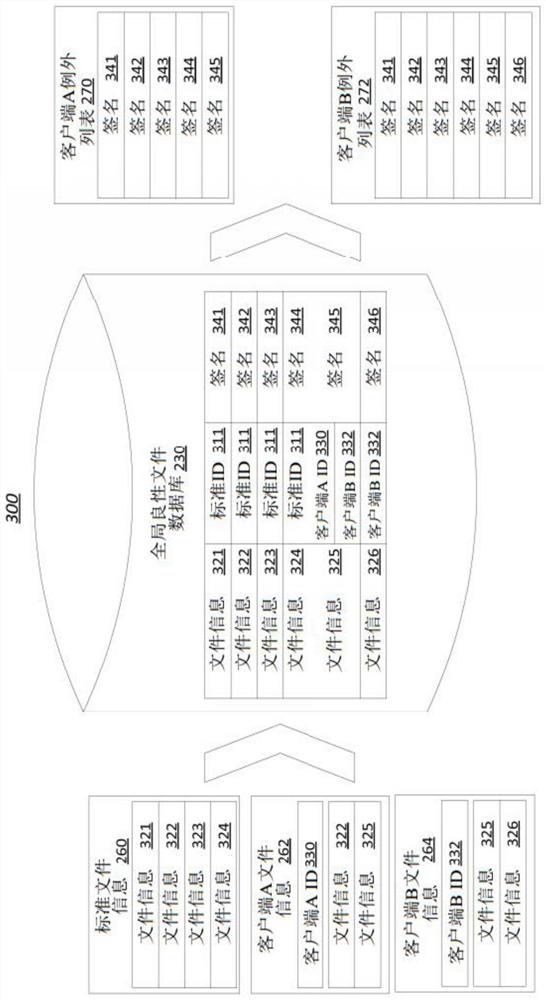
[0025] The methods disclosed herein improve the functionality of computing systems that generate or use lists of benign files. Three common approaches to malware detection are signature-based, behavior-based, and machine learning-based methods. Signature-based methods have ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com