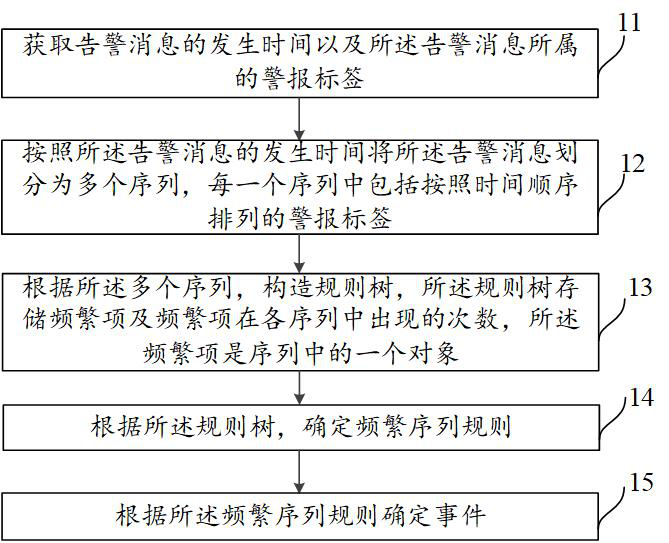
A method, device and equipment for processing an alarm message
A technology of alarm messages and processing methods, applied in the field of information processing, can solve problems such as inability to directly apply new systems, poor generalization performance, etc., and achieve the effect of saving time and cost and efficient compression methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0122] Example 1: An example of an alarm management method, in which the improved Prefixspan algorithm is used in the association stage.
[0123] Such as Figure 5 As shown, in order to clarify the processing process and results, five alarm messages are taken as examples from a large number of alarm messages. These five alarm messages belong to two different nodes, and the host (operation and maintenance node host) IDs are 1041 and 1043 respectively.
[0124] In the alarm merging phase, five alarm messages [a, b, c, d, e] are combined to generate alarm A and alarm B. The alarm message is given the ID of the corresponding alarm;
[0125] Before alarm correlation, alarm messages need to be divided into sequences based on events. With 5 minutes as an event granularity, these five alarm messages can be divided into three sequences. [a, b], [c, d], [e] corresponds to the alarm sequence [A, B], [A, B], [B]. Using the improved Prefixspan algorithm, assuming that the sequence with ...
Embodiment 2
[0126] Embodiment 2: an example of an alarm management method, wherein the association stage adopts a historical rule base algorithm.
[0127] Such as Figure 6 As shown, suppose there are the following 6 alarm messages. Although they are similar in text, they come from four different nodes. There are four types of HostID. The divided alarm sequences are [A, B] and [C, D, A, B].
[0128] In this case, based on the improved Prefixspan algorithm, only [A, B] alarm sequence can be excavated. In this case, it is assumed that the real frequent sequence in the system is [A, B, C, D, A], but because the sequence only appears once, and it happens to be separated by the event window, the Prefixspan algorithm fails to find out the sequence effectively. However, from the perspective of practical application and operation and maintenance experience, due to the frequent occurrence of [A, B, C, D, A] sequences in history, there may already be a complete troubleshooting method, so finding ...
Embodiment 3
[0131] Embodiment 3: Example of Improved Prefixspan Algorithm
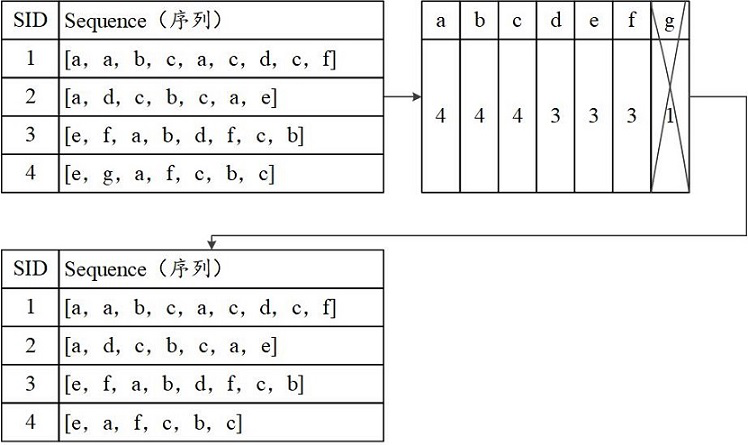
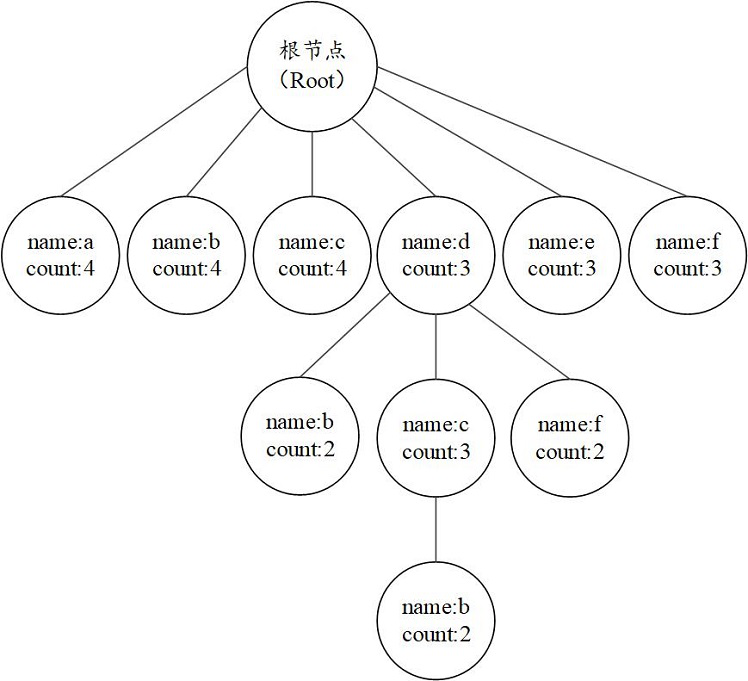
[0132] Such as Figure 8 As shown, the algorithm that introduces the tree structure is splitting the data at the same time. Create a root node for the rule tree, count the frequent items in the split sequence set, and remove the infrequent items from the sequence data.
[0133] Take item a among the frequent items as an example, the process of other frequent items is the same as a, create a new leaf node for a, and mark a as processed. Such as Figure 9 shown. Transfer to the newly created a node, find that the frequent item is only d, and create a child node d. If it is found that d does not have a suffix item, check to see if there are other unprocessed frequent items, and transfer to it if it exists. Finally, an example graph of the rule tree looks like Figure 8 shown. It can be seen that the sequence set has common frequent sequences [a, d], [a], [b], [c], [d].
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com