Intelligent monitoring gesture recognition method and device, equipment and storage medium
A gesture recognition and intelligent monitoring technology, applied in character and pattern recognition, instruments, biological neural network models, etc., can solve problems such as server crashes and inability to issue alarms in time, and achieve the effect of improving efficiency and practical significance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
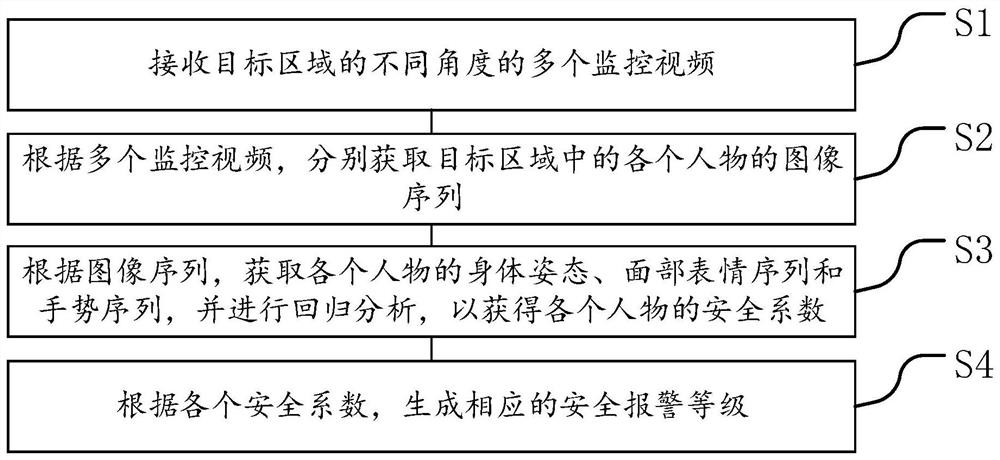
[0064] see Figure 1 to Figure 6 , the security monitoring method provided by the first embodiment of the present invention can be executed by a security monitoring device, in particular, by one or more processors in the security monitoring device, so as to realize steps S1 to S4.
[0065] S1. Receive multiple surveillance videos from different angles of the target area.
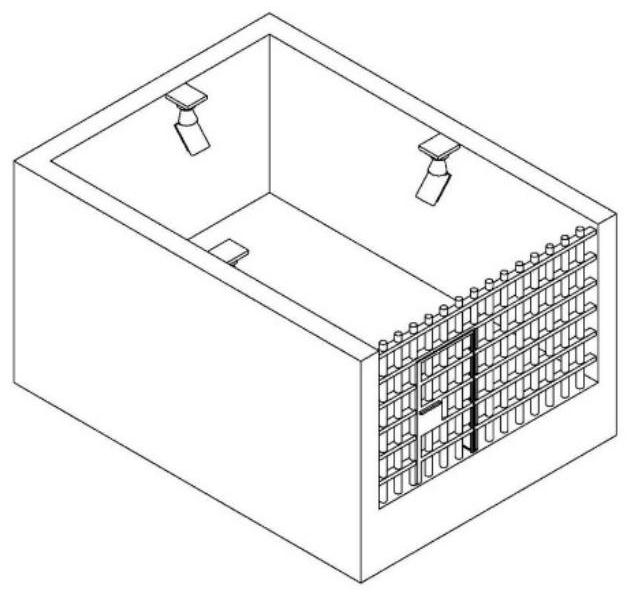
[0066] Specifically, the security monitoring device is electrically connected to the monitoring system in the target area, and can receive and analyze the monitoring images captured by the monitoring system. like figure 2 As shown, the monitoring system has at least three cameras installed in the target area, and the cameras are installed at a place higher than 2.5m above the bottom surface, so that the angle between the shooting angle of the camera and the portrait in the target area is not greater than 45°. At least three cameras are arranged at different angles of the target area.
[0067] It should b...
Embodiment 2
[0132] Embodiment 2. The embodiment of the present invention provides a safety monitoring device, which includes:
[0133] The video module 1 is used to receive multiple surveillance videos from different angles of the target area.
[0134] The image module 2 is used to obtain image sequences of each person in the target area according to a plurality of surveillance videos.
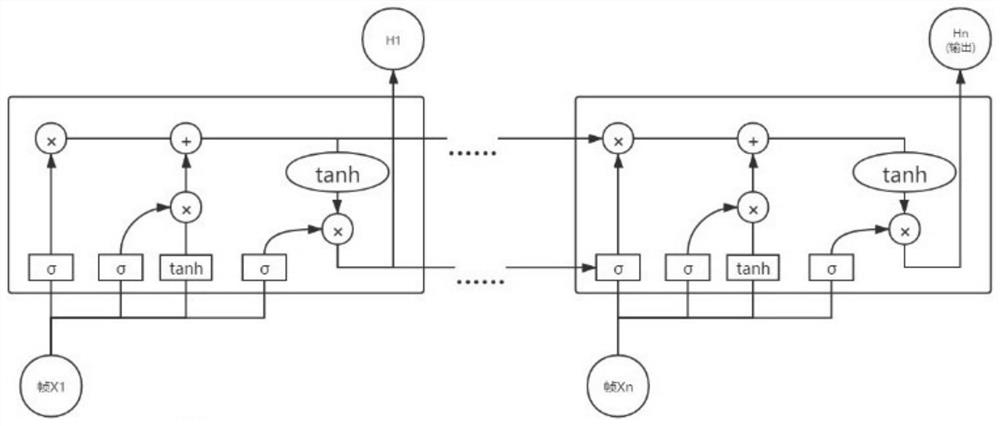
[0135] The coefficient module 3 is used to obtain the body posture, facial expression sequence and gesture sequence of each character according to the image sequence, and perform regression analysis to obtain the safety factor of each character.
[0136] The level module 4 is used to generate the corresponding security alarm level according to each security factor.
[0137] Optionally, the image module 2 specifically includes:
[0138] The skeleton unit is used to obtain skeleton information from different angles of each person in the target area through the OpenPose model according to mul...
Embodiment 3
[0177] Embodiment 3. An embodiment of the present invention provides a security monitoring device, which includes a processor, a memory, and a computer program stored in the memory. The computer program can be executed by the processor to implement the security monitoring method as described in the first aspect.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com