Authority management method and device, electronic equipment and storage medium
An authority management and authority technology, which is applied in the fields of electronic equipment and storage media, devices, and authority management methods, can solve the problems of single terminal authority monitoring standard and low user privacy security, and achieves a simple and direct way of monitoring codes and improves security. Performance, easy-to-achieve effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
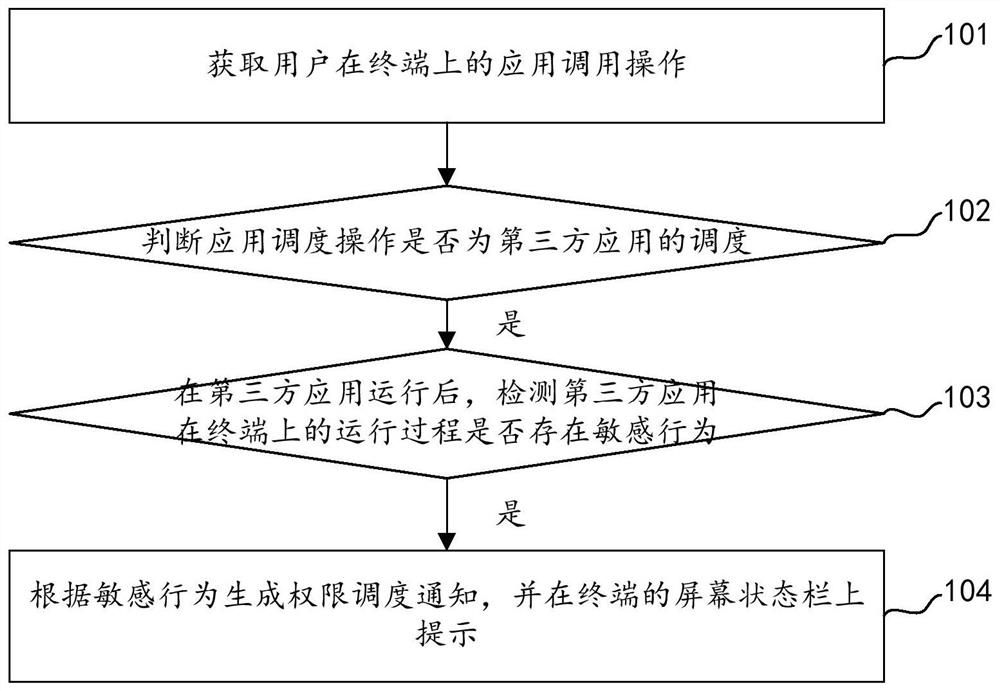
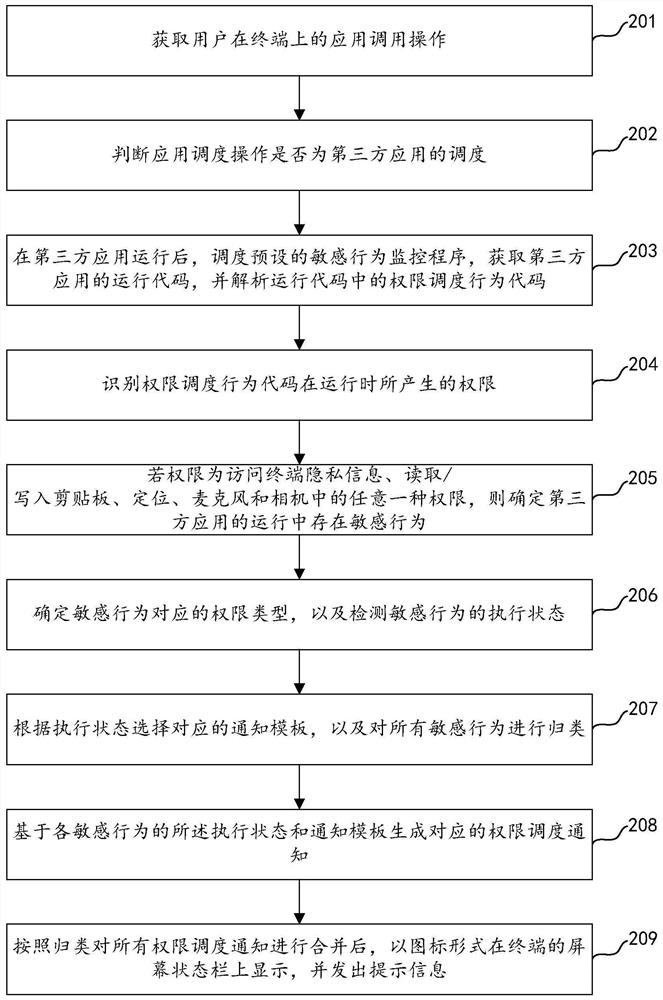
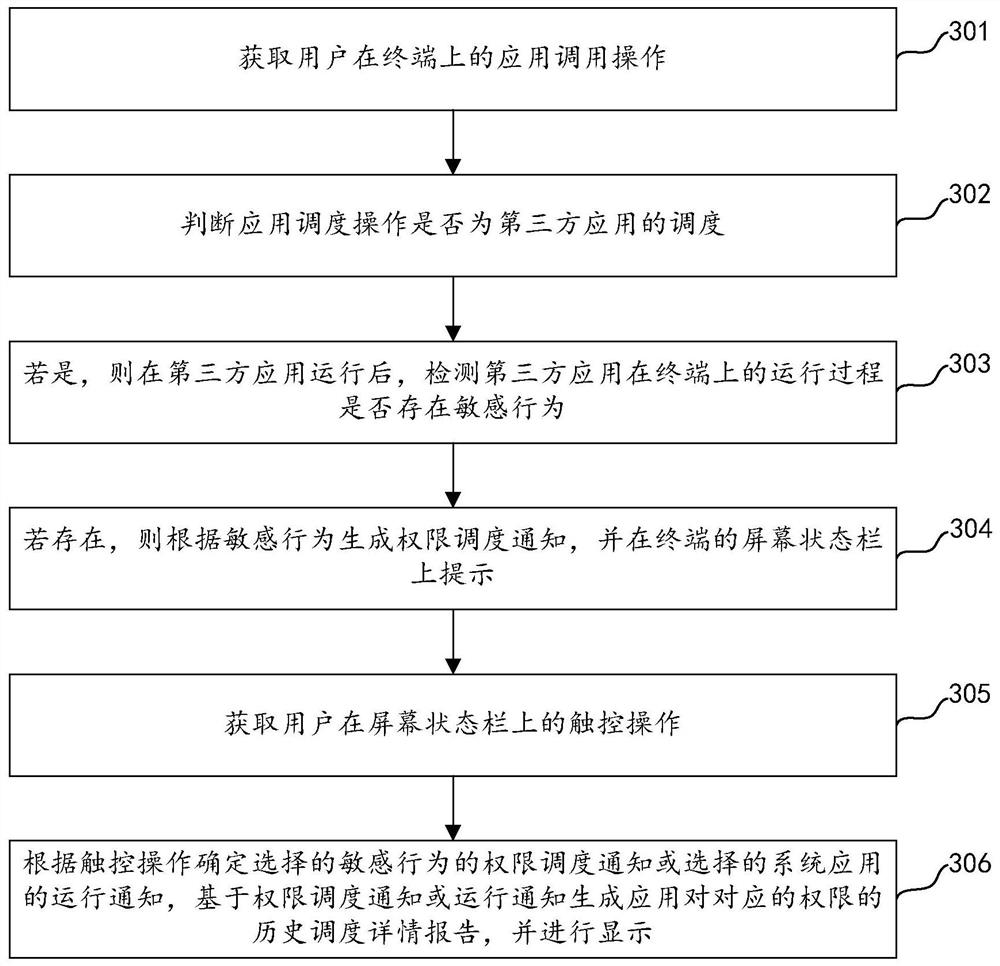
[0072] An embodiment of the present invention provides a permission management method. When the method detects that a third-party application is scheduled on the terminal, it judges whether the scheduling behavior of the third-party application is a sensitive behavior, and if so, generates a permission scheduling notification according to the sensitive behavior. And prompt on the screen status bar, based on this method to detect whether the scheduling of some permissions of the terminal by the application on the terminal during the running process is illegal scheduling, compared with the existing technology, the compatibility and versatility of this method Relatively high, there is no need to set monitoring rules for permissions, and it can be applied to the monitoring of permission calls for various applications, avoiding the security risks of single-rule monitoring.
[0073] The terms "first", "second", "third", "fourth", etc. (if any) in the description and claims of the pre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com