A host remote monitoring method based on chip-level privacy computing
A remote monitoring and chip-level technology, applied in computer security devices, computing, instruments, etc., can solve the problems of high real-time connection cost, insufficient security, and increased monitoring cost, so as to improve monitoring flexibility and solve security deficiencies. , the effect of reducing monitoring costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
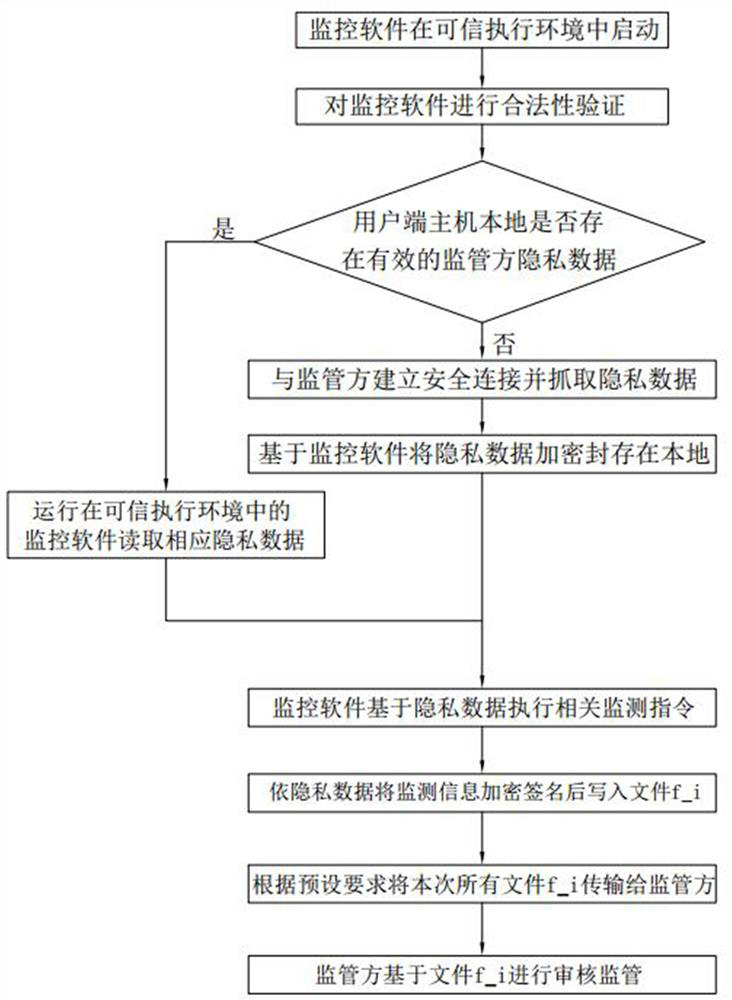
[0041] This embodiment discloses a host remote monitoring method based on chip-level privacy computing, including the following steps:
[0042] S1. The monitoring software in the client host is started in a trusted execution environment based on the chip level;
[0043] S2. Determine whether there is valid privacy data locally in the client host, if so, directly enter step S4, otherwise, enter step S3;
[0044] S3. Establish a secure connection with the regulator and capture private data;
[0045] S4. The monitoring software running in the trusted execution environment executes relevant monitoring instructions based on private data, and encrypts and signs the monitoring results and transmits them to the regulator.
[0046] Specifically, in step S1, the monitoring software is automatically started when the user terminal host is turne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com