Data stream encryption and decryption method, electronic equipment and chip system
A technology of encryption and decryption and data flow, which is applied in the field of information security, can solve the problems of low performance of data flow encryption and decryption, slow data processing speed, etc., and achieve the effect of improving performance and data processing speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0038] Example 1
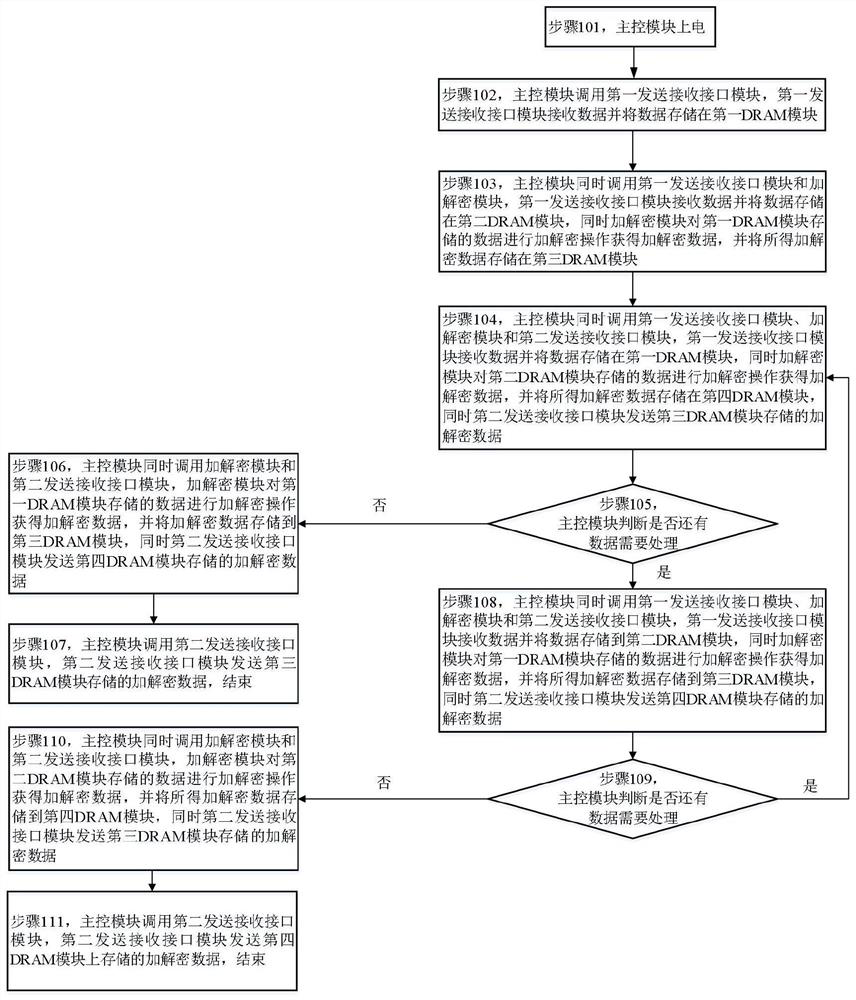
[0039] This embodiment provides a data stream encryption and decryption method, such as figure 1 shown, including:
[0040] Step 101, the main control module is powered on;
[0041] Step 102, the main control module calls the first sending and receiving interface module, and the first sending and receiving interface module receives the data and stores the data in the first DRAM module;
[0042] Step 103, the main control module calls the first sending and receiving interface module and the encryption and decryption module at the same time, the first sending and receiving interface module receives the data and stores the data in the second DRAM module, and the encryption and decryption module performs the data stored in the first DRAM module at the same time. The encryption and decryption operation obtains encryption and decryption data, and stores the obtained encryption and decryption data in the third DRAM module;
[0043] Step 104, the main control mod...
Example Embodiment
[0064] Embodiment 2
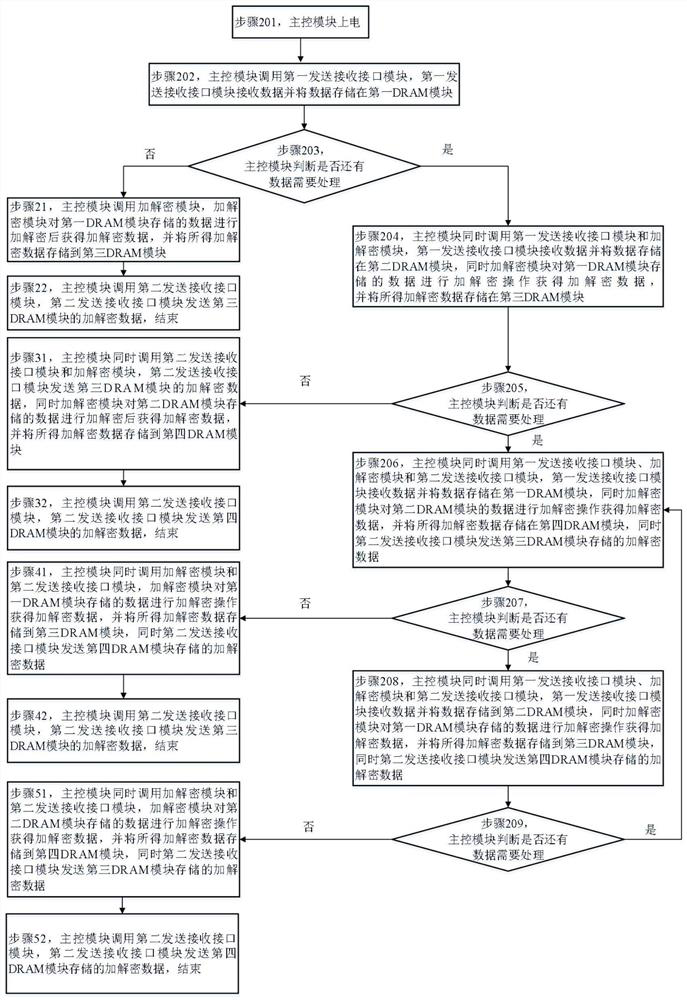
[0065] This embodiment provides a data stream encryption and decryption method, such as figure 2 shown, including the following steps:
[0066] Step 201, the main control module is powered on;
[0067] In this embodiment, the DRAM module may be a random access memory, and its space size is limited, so the data to be encrypted and decrypted needs to be sent and processed in packets.
[0068] In this embodiment, after the main control module is powered on, it obtains the length of the data to be encrypted and decrypted from the data processing requester, and calculates the transmission data of the data to be encrypted and decrypted according to the length of the data to be encrypted and decrypted and the capacity of a single DRAM module. The number of packets, that is, how many packets of data to be encrypted and decrypted need to be sent;
[0069] Specifically, the number of data packets sent is calculated according to the quotient value obtained by di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com