A Quantum Digital Signature and Quantum Digital Signcryption Method
A quantum digital signature and digital signature technology, applied in the field of quantum security, can solve problems such as high resource consumption, security threats, and classic digital signcryption protocol security threats, so as to avoid security risks, ensure security, high efficiency and The effect of unconditional security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
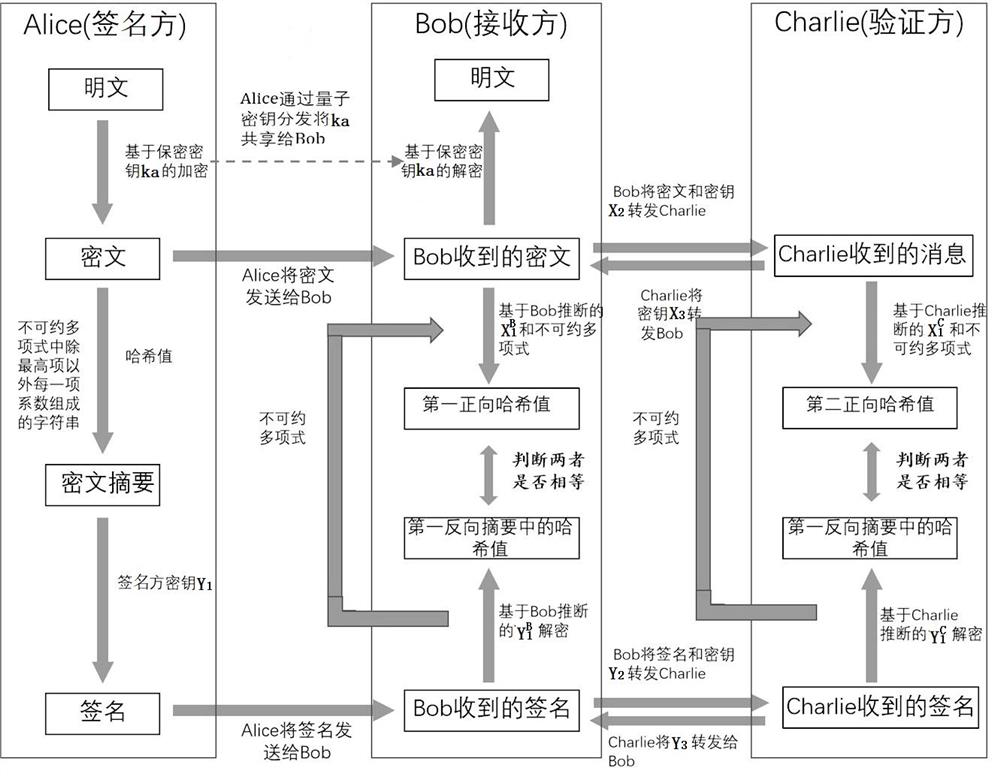
[0043] The quantum digital signature method of the present invention has the following three steps: the phase of preparing a key, the phase of generating a signature and the phase of verifying a signature.
[0044] (1) Prepare keys: the signer, the receiver and the verifier hold their own two sets of random keys, and the six strings of keys are divided into two groups, which are denoted as X group and Y group. The two strings of random number key strings held by the signer are denoted as X 1 and Y 1 , similarly the receiver holds X 2 and Y 2 , the verifier holds X 3 and Y 3 , and the keys among the signer, receiver and verifier form a secret sharing; the way to realize the secret sharing is preferably quantum secret sharing;
[0045] Secret sharing relationship: holding both X 2 and X 3 to infer X 1 , while holding Y 2 and Y 3 to infer Y 1 , which satisfies the condition:
[0046] X 1 ⊕ X 2 ⊕ X 3 =0, Y 1 ⊕ Y 2 ⊕ Y 3 =0,
[0047] In the form...
Embodiment 2
[0066] The present invention includes a quantum digital signcryption method, the participants are the signer Alice, the receiver Bob and the verifier Charlie, including the following steps:
[0067] a Encryption: the signer Alice uses a secret key for the plaintext message Encrypt to obtain ciphertext; preferred encryption adopts XOR operation;
[0068] b Digitally sign the ciphertext through the above-mentioned quantum digital signature method. In the process of digitally signing the ciphertext, the ciphertext is used as a message to be signed and the signer will also keep the secret key It is sent to the receiver in an unconditional and safe way, and the unconditional and safe way is realized by quantum key distribution technology or secure distribution of quantum random numbers; the specific process is:
[0069] 1) Prepare keys: Alice the signer, Bob the receiver, and Charlie the verifier hold their own two sets of random keys. These six strings of keys are divided into ...
Embodiment 3
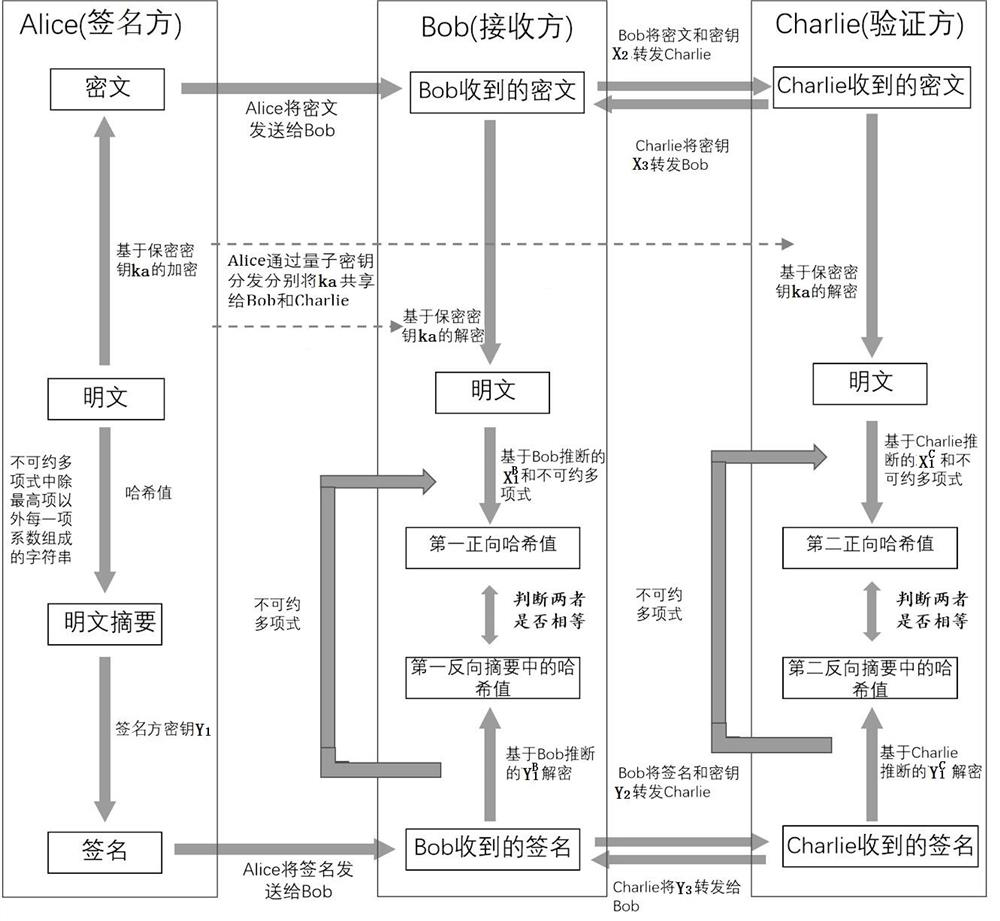
[0089] The present invention includes a quantum digital signcryption method, the participants are the signer Alice, the receiver Bob and the verifier Charlie, and the method includes the following steps:
[0090] S1 encryption: the signer Alice uses the secret key for the plaintext message Encrypt to get the ciphertext; the signer Alice sends the ciphertext to the receiver Bob, and the receiver Bob sends the ciphertext to the verification party Charlie; at the same time, the signer Alice also keeps the secret key It is sent to the receiver Bob and the verifier Charlie in an unconditional and safe way, and the unconditional and safe way is realized by quantum key distribution technology or secure distribution of quantum random numbers;
[0091] S2 digitally signs the plaintext message through the same quantum digital signature method as in Embodiment 1. In the process of digitally signing the plaintext message, the plaintext message is used as the message that needs to be sig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com