Defense method for speculative execution attack
A technology of instruction and memory access, applied in the protection of internal/peripheral computer components, instruments, electrical digital data processing, etc., can solve the problems of high performance overhead and large hardware modification, so as to avoid performance overhead, ensure safety and effectiveness sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
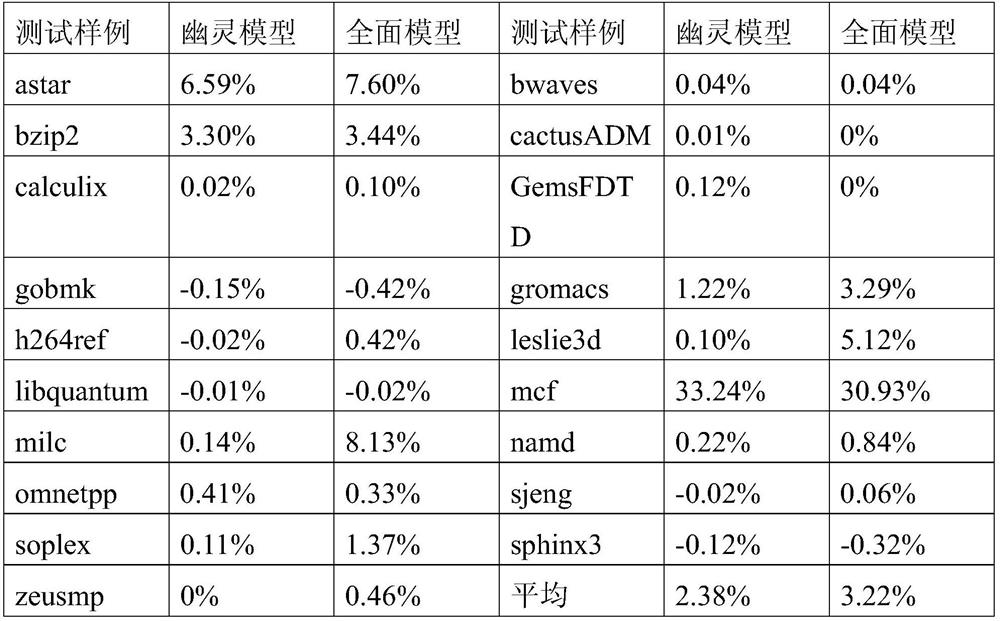
[0029] The present invention will be further described in detail below by specific embodiments and drawings.
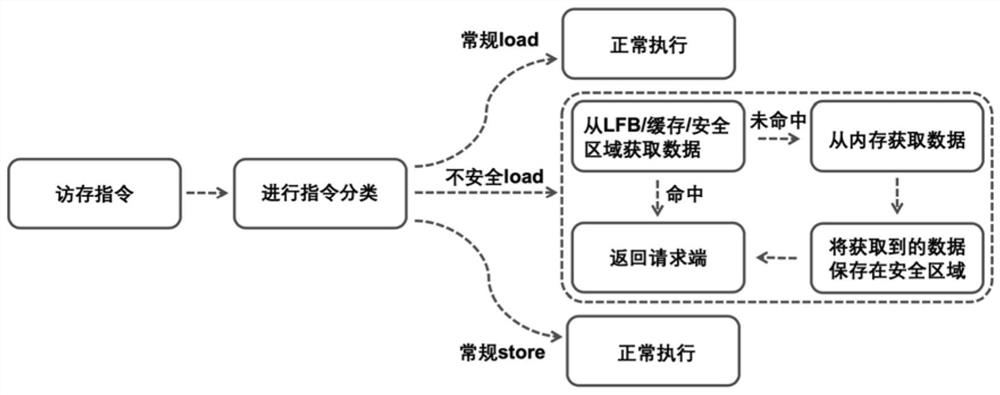
[0030] figure 1 It is a system architecture of the present invention. like figure 1 As shown, the defense method of the speculative execution attack is mainly included in the following steps:
[0031]Step S1: Perform instruction classification, that is, mark all instructions associated with the hidden channel as unsafe instructions, and classify the interview instruction according to the tag;
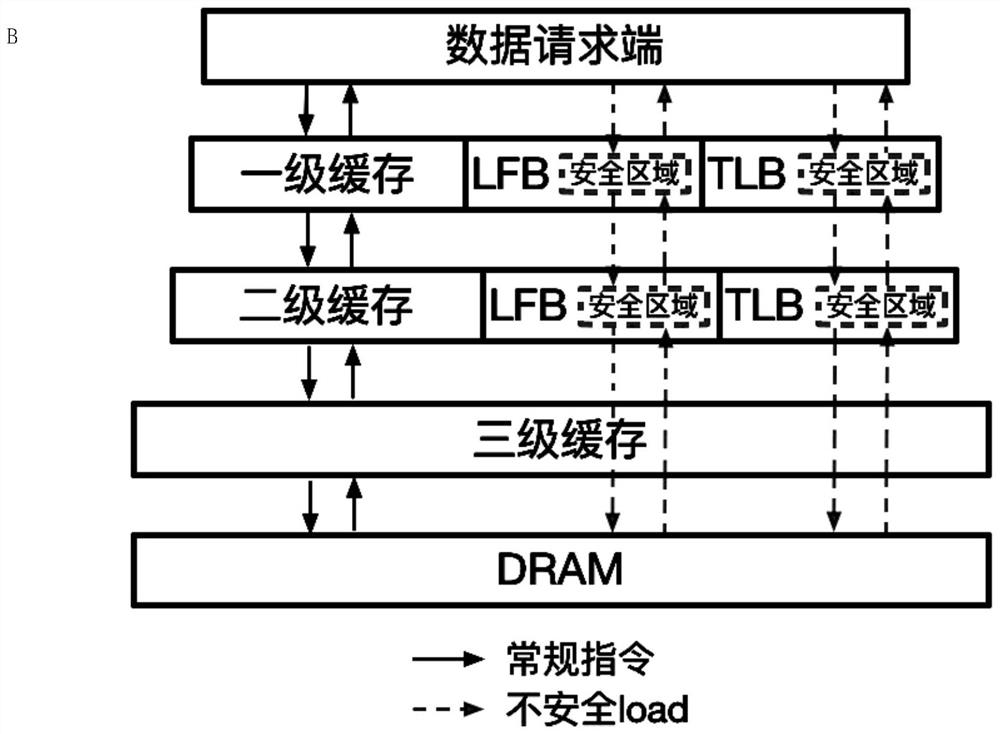
[0032] Step S2: Provides the LFB and TLB to divide the cache system that is regular area and security zone, which will hide the interview instruction marked as unsafe instructions within the secure area divided within the cache system, thereby avoiding its change cache Architecture state. Among them, the hidden execution refers to the micro-frame state in the secure area cannot be read from the regular instruction from the current physical core or other physical core, thereby perf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com