Unified data access service type fine-grained authority control method and system
A data access and authority control technology, applied in database management systems, digital data authentication, data processing applications, etc., can solve the problems of coarse control of data authority granularity and uncontrollable data authority, and achieve the effect of safe open sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
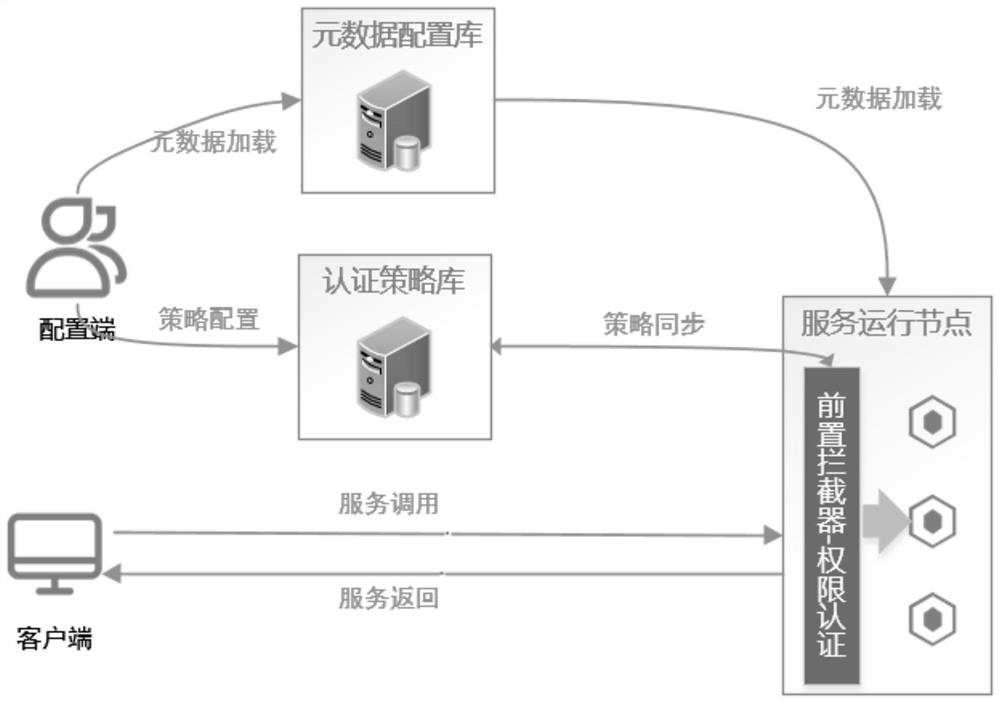
[0044] This embodiment provides a technical solution: a unified data access service-type fine-grained authority control method, including the following steps:
[0045] S1: Data asset metadata management
[0046] Use the database to store the metadata information of the enterprise's data assets;
[0047] S2: Configure Metadata Property Access Permissions
[0048] Configure the access rights of metadata attributes based on metadata through the page, and synchronize them to the authentication database redis;
[0049] S3: access policy match
[0050] When the user makes a data service call, the server intercepts the data access before calling, and obtains the data service call message and matches the access strategy for the message analysis;
[0051] S4: Matching judgment
[0052] If the matching is successful, the data service call is made, and if the matching fails, the data service call is rejected.
[0053] In this example, if figure 1 As shown, the metadata information ...
Embodiment 2
[0066] like Figure 4 As shown, it is an implementation flowchart of the fine-grained authority control method of the unified data access service in this embodiment. First, the client (user) submits a single entity read service request, and then the server uses an interceptor to intercept data access and obtain the request report. text and parse it, wherein, the request message includes the following information: APPID, SPECID, query field, query condition; then go to the cache database (redis) to query data authorization information according to APPID and SPECID, and confirm whether there is authorization information and authorization Information will continue to obtain its policy_type (authorization policy type), and then judge the authorization policy type. If there is no authorization information, it will prompt the user to call the service without authorization; when judging the authorization policy type, when the authorization policy type is attribute_auth (attribute Aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com