User identification security verification method and device based on shiro framework, and computer medium
A security verification and user identification technology, applied in the field of network security, can solve the problems of not setting token timeliness, validity or valid for a period of time, illegal use, etc., to save resources, ensure security, and have strong compatibility Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
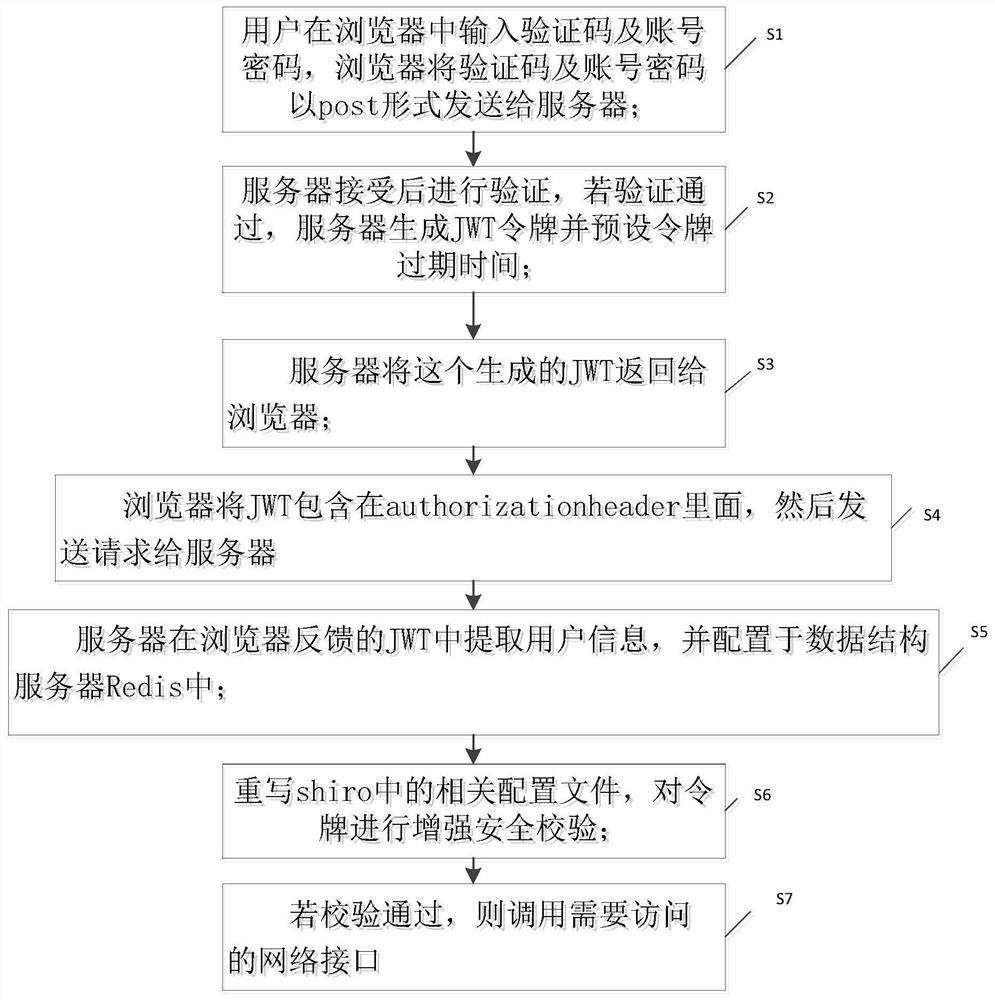
[0042] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
[0043] At present, most front-end and back-end separation projects on the market are based on tokens for security verification, but many projects do not set the timeliness of tokens, and tokens are always valid or valid within one day. After the user logs in on the page, illegal elements get the token, which can achieve the purpose of directly requesting various interfaces without operating on the page, which is very low in security.
[0044] According to the technical solution of the present invention, the token obtained by the user after logging in is valid within five minutes, and the synchronously generated mark for refreshing the token is half an hour. Five minutes later, if the request comes and finds that the token has expired, but the token is still valid, the request ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com