Method for bidirectional secure communication over unidirectional network for edge computing
A one-way network and edge computing technology, applied in the field of communication, can solve problems such as network obstacles, long transmission paths, and Internet insecurity, and achieve the effect of reducing delay and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
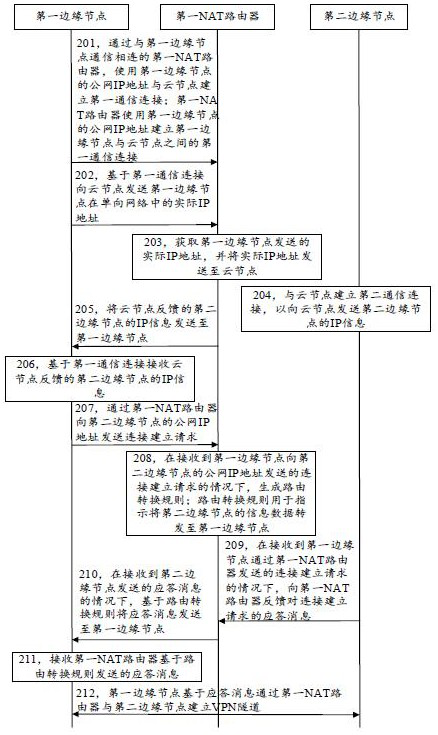
[0042] The specific implementation manners of the present application will be further described in detail below in conjunction with the drawings and embodiments. The following examples are used to illustrate the present application, but not to limit the scope of the present application.
[0043] First, some terms involved in this application are introduced.
[0044] Cloud computing (cloud computing) is a kind of distributed computing, which refers to decomposing a huge data computing processing program into countless small programs through the network "cloud", and then processing and analyzing these programs through a system composed of multiple servers. The applet gets the result and returns it to the user. In the early days of cloud computing, simply put, it was simple distributed computing, solving task distribution, and merging calculation results.
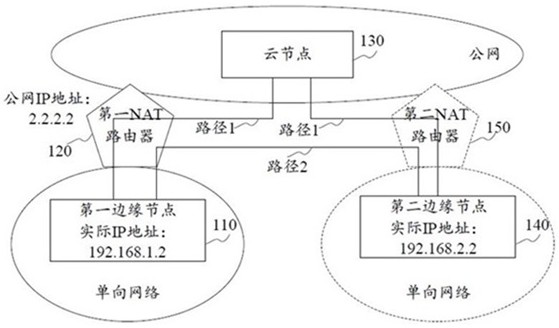
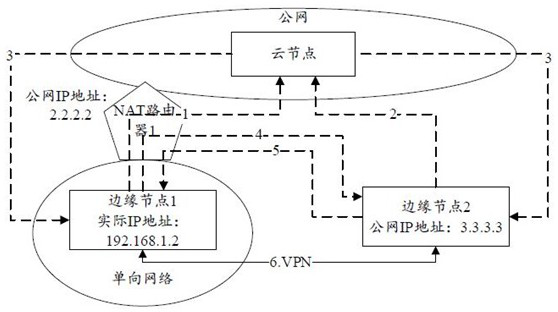
[0045] Cloud node: refers to the host / server used in cloud computing.
[0046] Edge computing: refers to an open platform...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com