Permission authentication method and system for information security sharing
A technology of information security and authority authentication, applied in the field of information security, can solve the problems of single authority authentication method, inflexible application, and affecting the security of information sharing, and achieve the effect of high accuracy and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
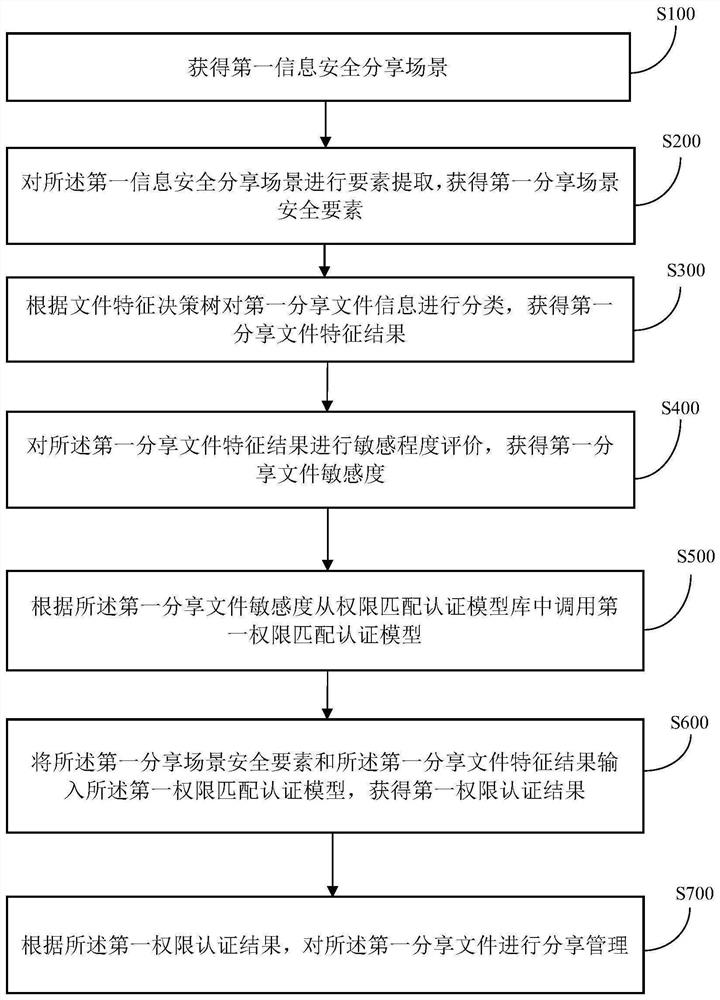
[0031] Such as figure 1 As shown, the embodiment of the present application provides an authority authentication method for information security sharing, wherein the method includes:
[0032] Step S100: Obtain the first information security sharing scene;
[0033] Step S200: Extract elements of the first information security sharing scene to obtain security elements of the first sharing scene;
[0034] Specifically, with the development of Internet technology, information sharing is becoming more and more popular. Sharing resource information with others in order to achieve a more reasonable allocation of resources and save social costs is to improve the utilization of information resources and avoid unnecessary waste in information collection, An important means of repeated waste in storage and management, therefore, the security of information sharing is of great significance. The first information security sharing scenario is an information and data sharing application sc...
Embodiment 2
[0082] Based on the same inventive idea as the authority authentication method for information security sharing in the foregoing embodiments, the present invention also provides an authority authentication system for information security sharing, such as Figure 6 As shown, the system includes:
[0083] A first obtaining unit 11, configured to obtain a first information security sharing scenario;
[0084] A second obtaining unit 12, the second obtaining unit 12 is configured to extract elements of the first information security sharing scene, and obtain the security elements of the first sharing scene;
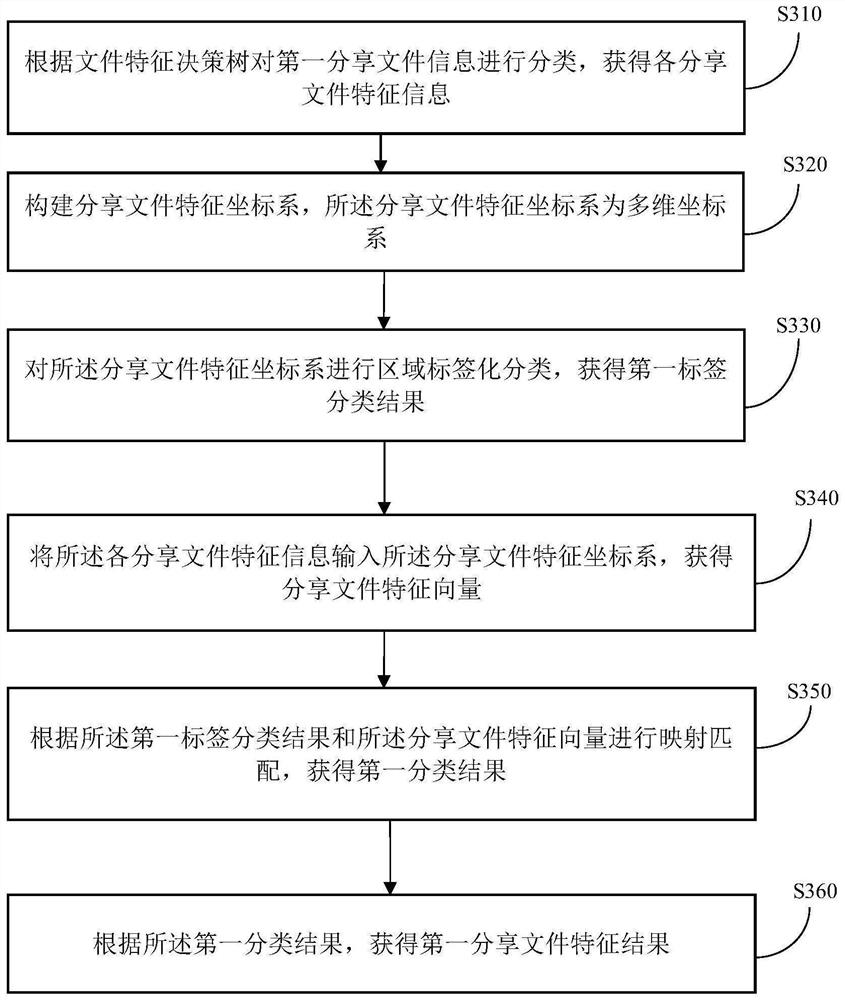
[0085] A third obtaining unit 13, the third obtaining unit 13 is configured to classify the first shared file information according to the file feature decision tree, and obtain the first shared file feature result;
[0086] A fourth obtaining unit 14, the fourth obtaining unit 14 is configured to evaluate the sensitivity of the characteristic result of the first shared file,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com