Dangerous behavior early warning method and device based on action law and application thereof
A behavior and law technology, applied in the field of dangerous behavior early warning based on action law, can solve problems such as low superiority, weakened relevance of key personnel events, inability to effectively evaluate the danger of surrounding personnel, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
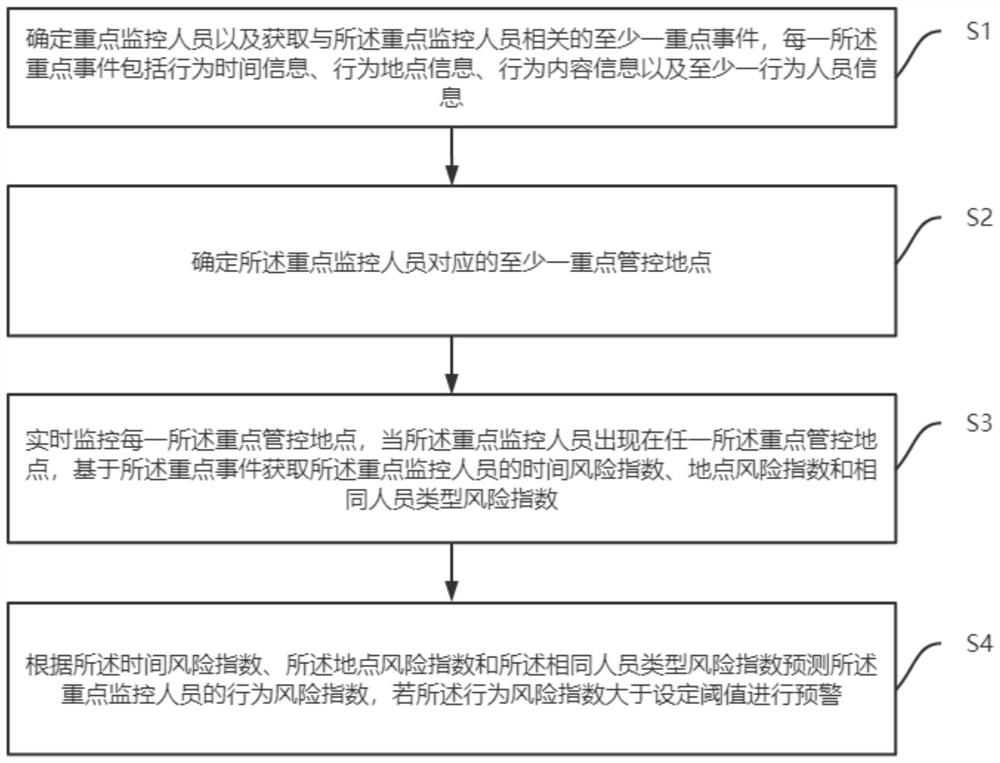
[0028] This embodiment provides a dangerous behavior early warning method based on action rules. In this embodiment, the method is as follows: figure 1 Shown can be summarized as the following 4 steps:
[0029] Step S1: Determine the key monitoring personnel and obtain at least one key event related to the key monitoring personnel, each of the key events includes behavior time information, behavior location information, behavior content information and at least one behavior personnel information;
[0030] Step S2: Determine at least one key control location corresponding to the key monitoring personnel;
[0031] Step S3: Monitor each of the key control locations in real time, and when the key monitoring personnel appear in any of the key control locations, obtain the time risk index, location risk index and the same personnel of the key monitoring personnel based on the key event type risk index;
[0032] Step S4: Predict the behavior risk index of the key monitoring personn...
Embodiment 2
[0056] Based on the same idea, this embodiment also provides a dangerous behavior early warning device based on action trajectory, which is used to realize the dangerous behavior early warning method based on action rules described in Embodiment 1. For details, refer to figure 2 , the device consists of the following modules:
[0057] An acquisition module, configured to determine key monitoring personnel and acquire at least one key event, each of the key events includes behavior time information, behavior location information, behavior content information and at least one behavior personnel information, and the key events include information related to the Focus on events of the same type of personnel as the monitoring personnel;
[0058] An deployment and control module, configured to determine at least one key control location corresponding to the key monitoring personnel;
[0059] A monitoring module, configured to monitor each of the key control locations in real time,...
Embodiment 3
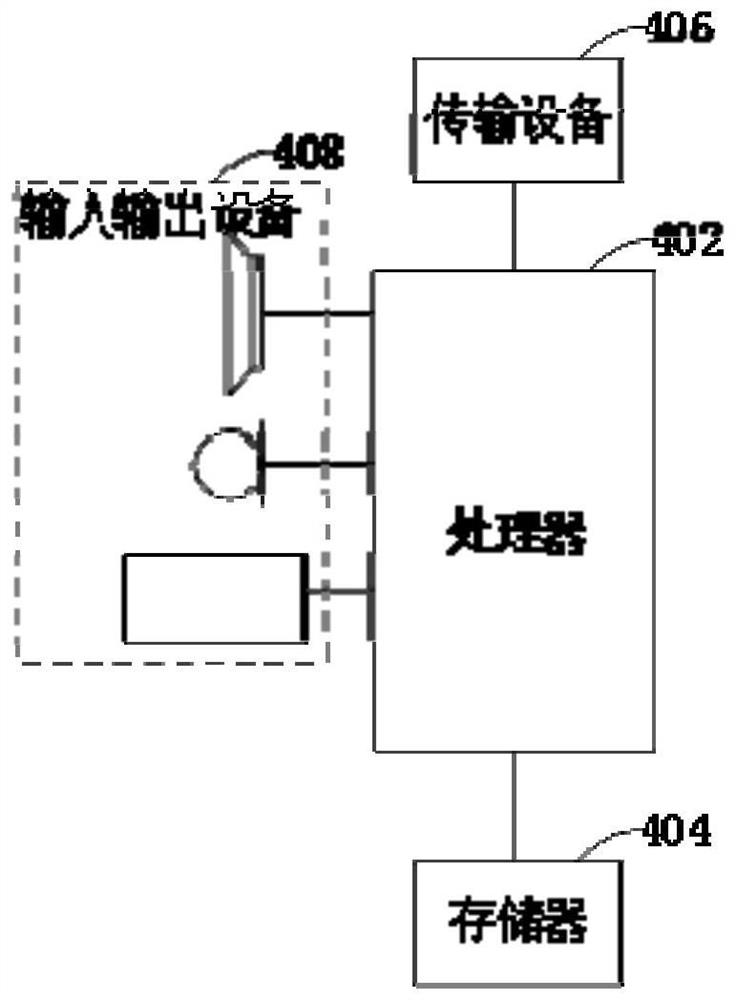
[0062] This embodiment also provides an electronic device, refer to image 3 , including a memory 404 and a processor 402, the memory 404 stores a computer program, and the processor 402 is configured to run the computer program to execute the steps of any method for early warning of dangerous behaviors based on action rules in the above embodiments.
[0063] Specifically, the processor 402 may include a central processing unit (CPU), or an Application Specific Integrated Circuit (ASIC for short), or may be configured to implement one or more integrated circuits in the embodiments of the present application.
[0064] Wherein, the memory 404 may include a mass memory 404 for data or instructions. By way of example and not limitation, the memory 404 may include a hard disk drive (Hard Disk Drive, referred to as HDD), a floppy disk drive, a solid state drive (Solid State Drive, referred to as SSD), flash memory, optical disk, magneto-optical disk, magnetic tape or general serial ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com