Security authentication system and method
A security authentication and security technology, applied in the field of security authentication systems, can solve problems such as inability to authenticate terminals, inability to timely and accurate terminals, and single-point failures, and achieve the effect of improving timeliness and accuracy and reducing the risk of single-point failures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0066] Example 1:
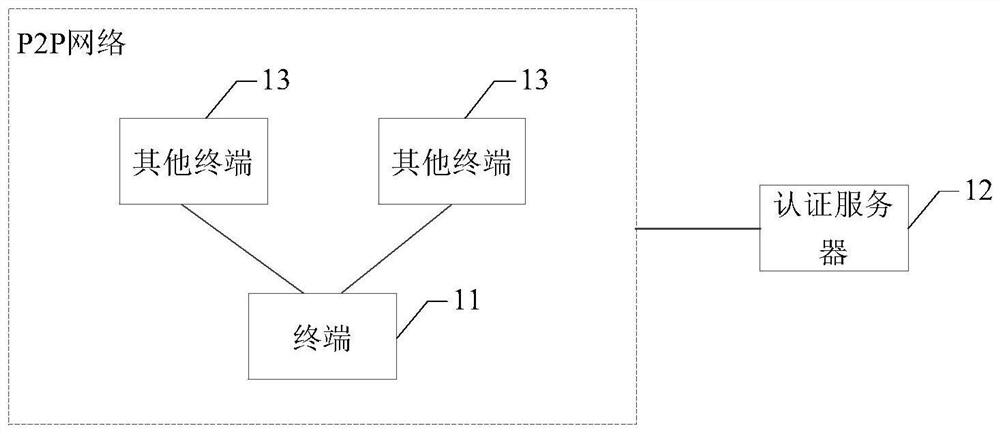
[0067] figure 1 A schematic diagram of a security authentication system provided by some embodiments is shown, and the system includes: a terminal 11, an authentication server 12, and a plurality of other terminals 13 located in the same peer-to-peer network P2P network as the terminal 11;
[0068] The terminal 11 is configured to send a first authentication request to the target other terminal 13 in the P2P network when receiving an access request to any application installed in itself, wherein the first authentication request is carrying the identification information of the terminal 11;
[0069] The target other terminal 13 is used to search for the target environment information corresponding to the terminal 11 of the identification information in the saved environment information according to the identification information; according to whether the target environment information contains the set risk environment information , determine the security s...
Example Embodiment
[0144] Example 2:
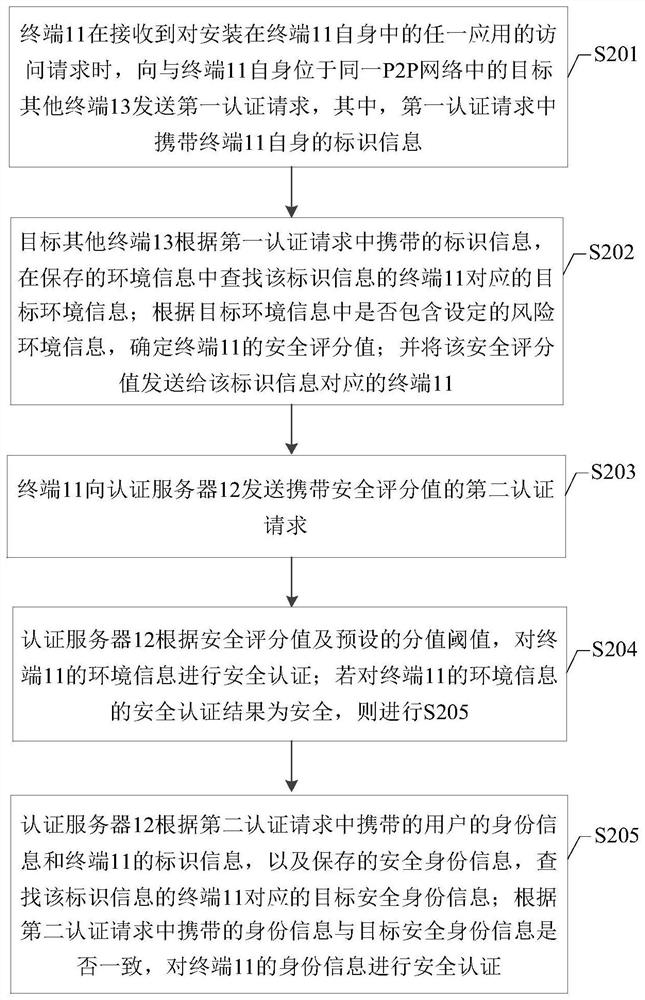
[0145] Based on the same technical concept, the present application provides a security authentication method, the method is applied to a terminal (for convenience of description, referred to as the first terminal), Figure 7 A schematic diagram of the sixth security authentication process provided by some embodiments is shown, such as Figure 7 As shown, the process includes:
[0146] S701: When receiving an access request for any application installed in the terminal itself, send a first authentication request to a target other terminal among multiple other terminals located in the same peer-to-peer P2P network as the terminal, wherein , the first authentication request carries the identification information of the terminal.
[0147] S702: Receive a security score value sent by the target other terminal; wherein, the security score value is the target other terminal, according to the identification information, searches the saved environment information...
Example Embodiment
[0159] Example 3:
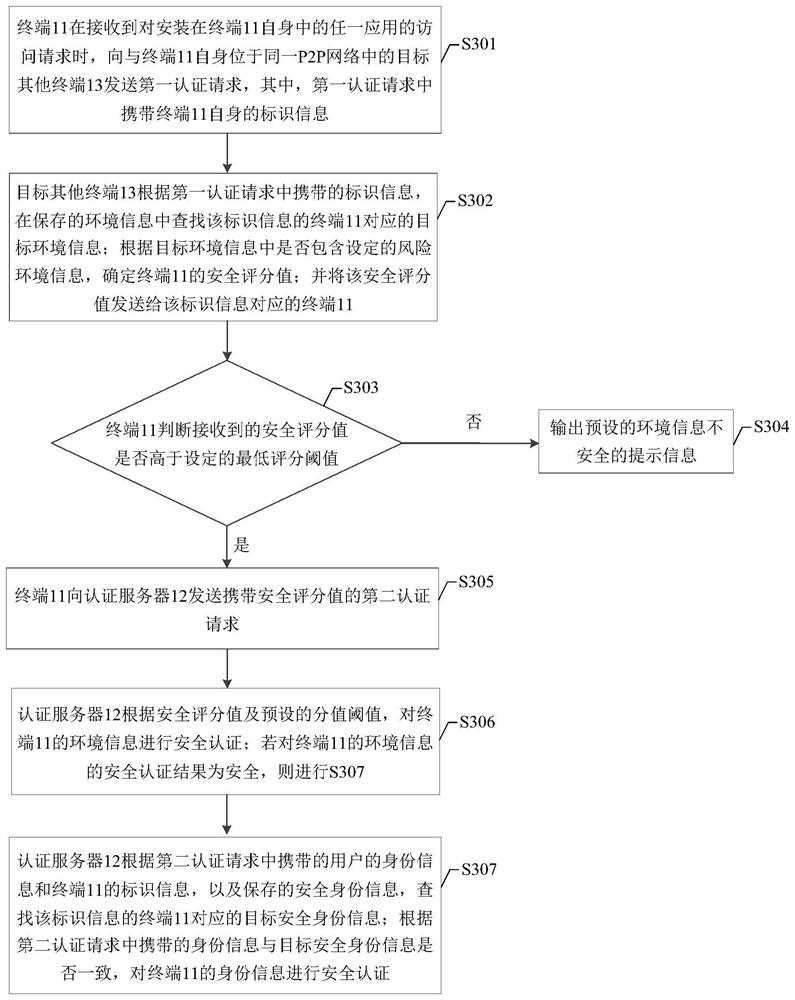
[0160] Based on the same technical concept, the present application provides a security authentication method, and the method is applied to a terminal (for convenience of description, referred to as a second terminal), Figure 8 A schematic diagram of the seventh security authentication process provided by some embodiments is shown, such as Figure 8 As shown, the process includes:
[0161] S801: Receive a first authentication request, wherein the first authentication request is that a first terminal located in the same peer-to-peer P2P network as the second terminal receives an authentication request for any application installed in the first terminal itself Sent when an access request is made, the first authentication request carries the identification information of the first terminal.
[0162] S802: According to the identification information, search the saved environment information for the target environment information corresponding to the terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com