Intrusion detection method based on traceability graph
A technology for intrusion detection and detection, which is applied in the field of intrusion detection based on traceability graphs, can solve the problems of massive traceability data performance overhead, loss of effective information, high overhead, etc., to meet timeliness requirements, expand perception scale, and speed up detection speed effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
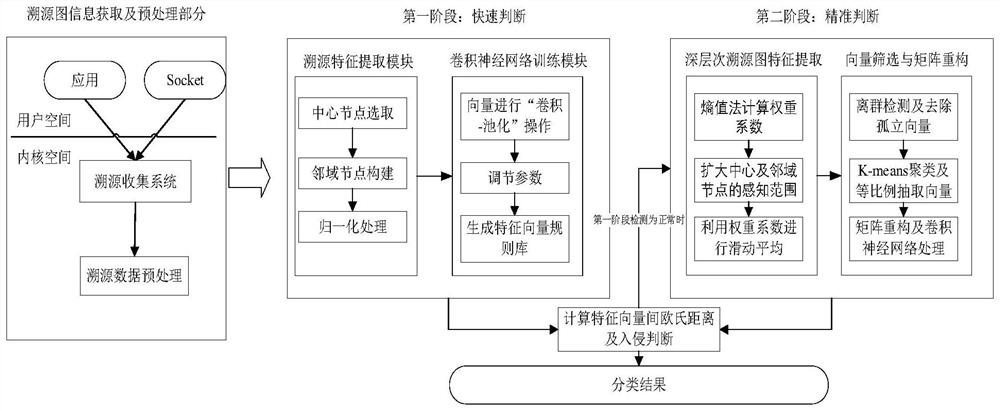
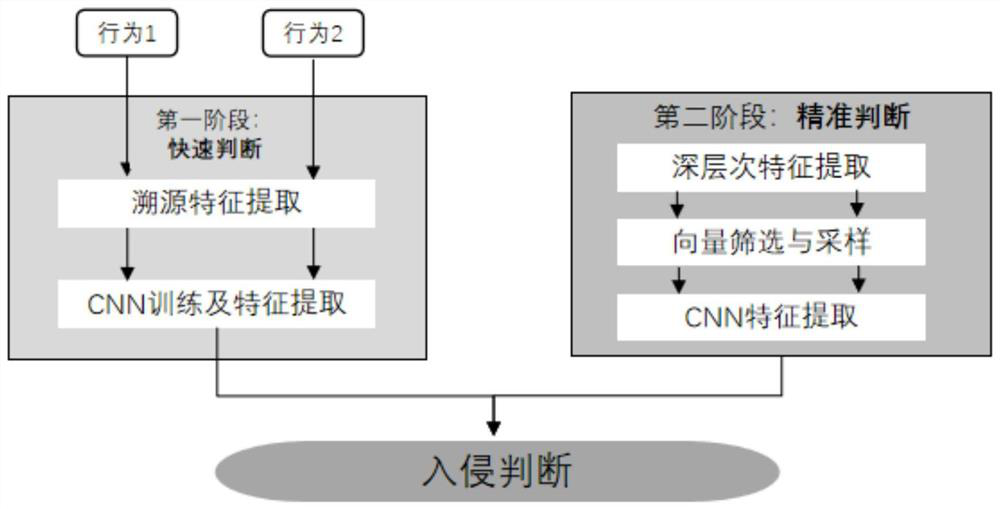
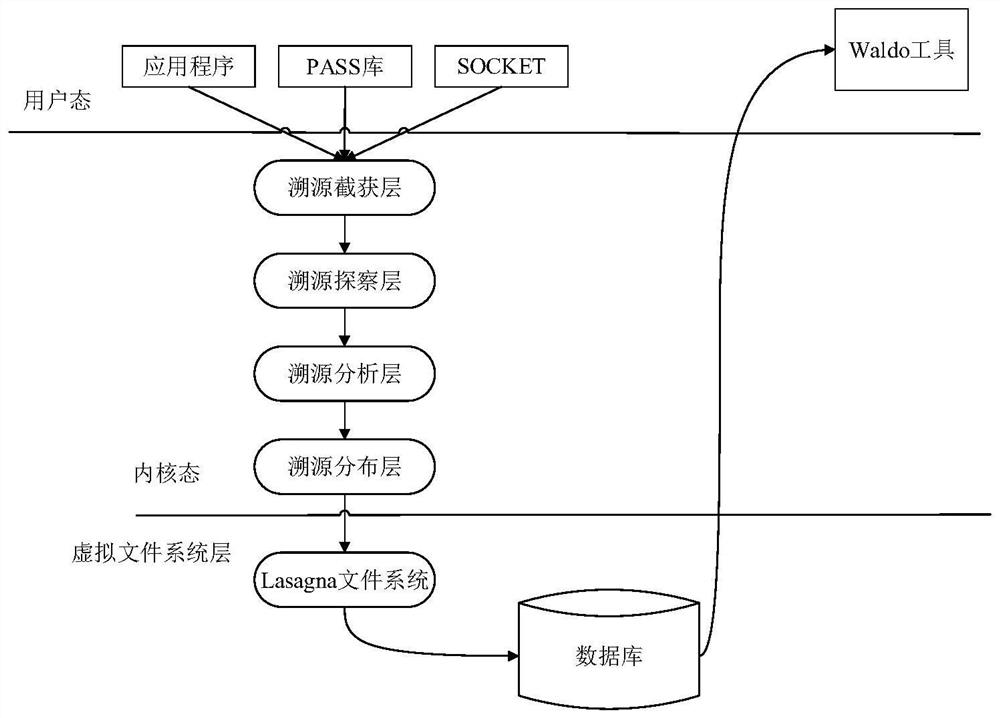
[0064] An intrusion detection method based on traceability graph, comprising the following steps:
[0065] (S1) Obtain the traceability graph of the behavior to be detected, and calculate the importance of each node;
[0066] In order to further save storage space and improve detection efficiency, after collecting the traceability data of the behavior to be detected in this embodiment, information unrelated to intrusion detection, such as temporary files and environment variables generated during program execution, is also filtered out, so as to compress the dependency relationship. quantity;
[0067] (S2) Obtain the top N with the highest importance in the traceability graph 1 Each node is used as the central node, and K is selected from the neighborhood of each central node. 1 After constructing the first neighborhood matrix, perform feature extraction on it to obtain the first traceability feature;
[0068] (S3) Calculate the difference m between the first traceability f...
Embodiment 2
[0115] A computer-readable storage medium, including a stored computer program, when the computer program is executed by a processor, controls the device where the computer-readable storage medium is located to execute the intrusion detection method based on the traceability graph provided in the above-mentioned Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com