Malicious traffic detection method based on computer memory evidence obtaining technology
A technology of malicious traffic and detection methods, applied in digital transmission systems, secure communication devices, electrical components, etc., can solve the problems of being attacked by the network, the host is not absolutely safe, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to clearly and completely describe the technical solutions in the embodiments of the present invention, the present invention will be further described in detail below with reference to the accompanying drawings in the embodiments.
[0038] Step 1 The process of taking the memory dump file is as follows:
[0039] Take a Windows 764-bit system host as an example.
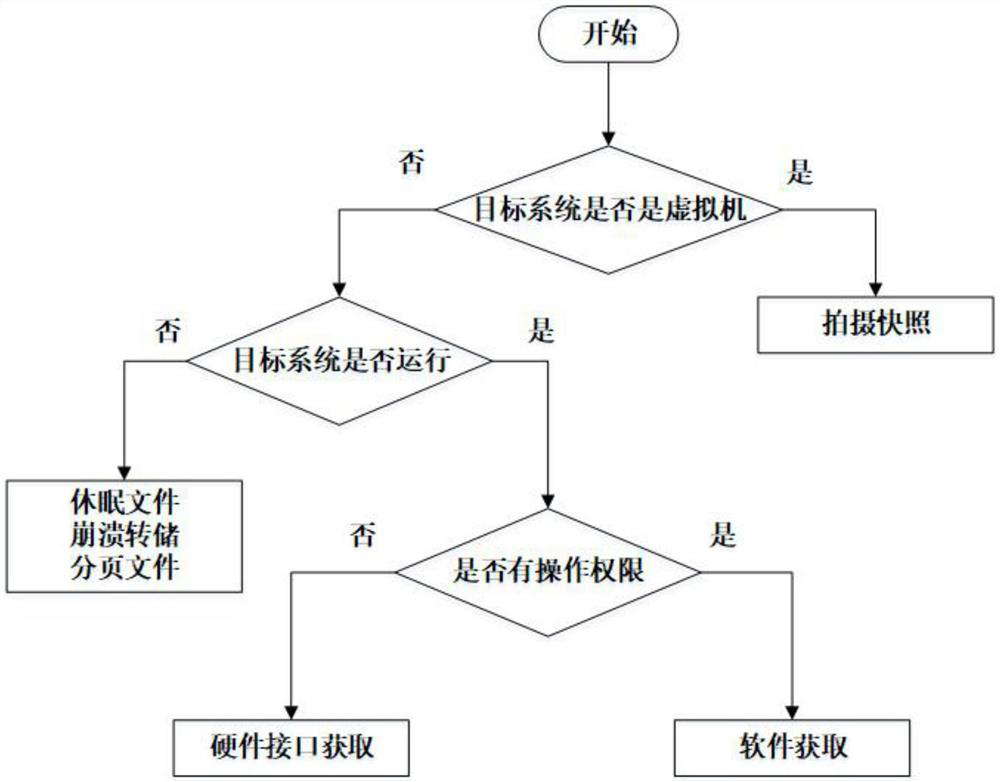
[0040] The flowchart of acquiring the memory dump file in the embodiment of the present invention is as follows: figure 1 shown, including the following steps.
[0041] Step 1-1 determines that the victim host is not a virtual machine;
[0042] Step 1-2 determines that the victim host is running;
[0043] Steps 1-3 determine that you have the operation authority of the victim host, then use software to obtain the memory dump file of the target operating system.
[0044] Step 2 Extract the traffic from the memory image using the Volatility forensics framework
[0045] Step 2-1 Find the kernel debu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com