File redundancy removal method for terminal equipment, terminal equipment and storage medium
A terminal device and file technology, applied in the file system, file metadata retrieval, file/folder operation, etc., can solve the problems of large time and system resource overhead, and achieve the effect of reducing time and eliminating redundant files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
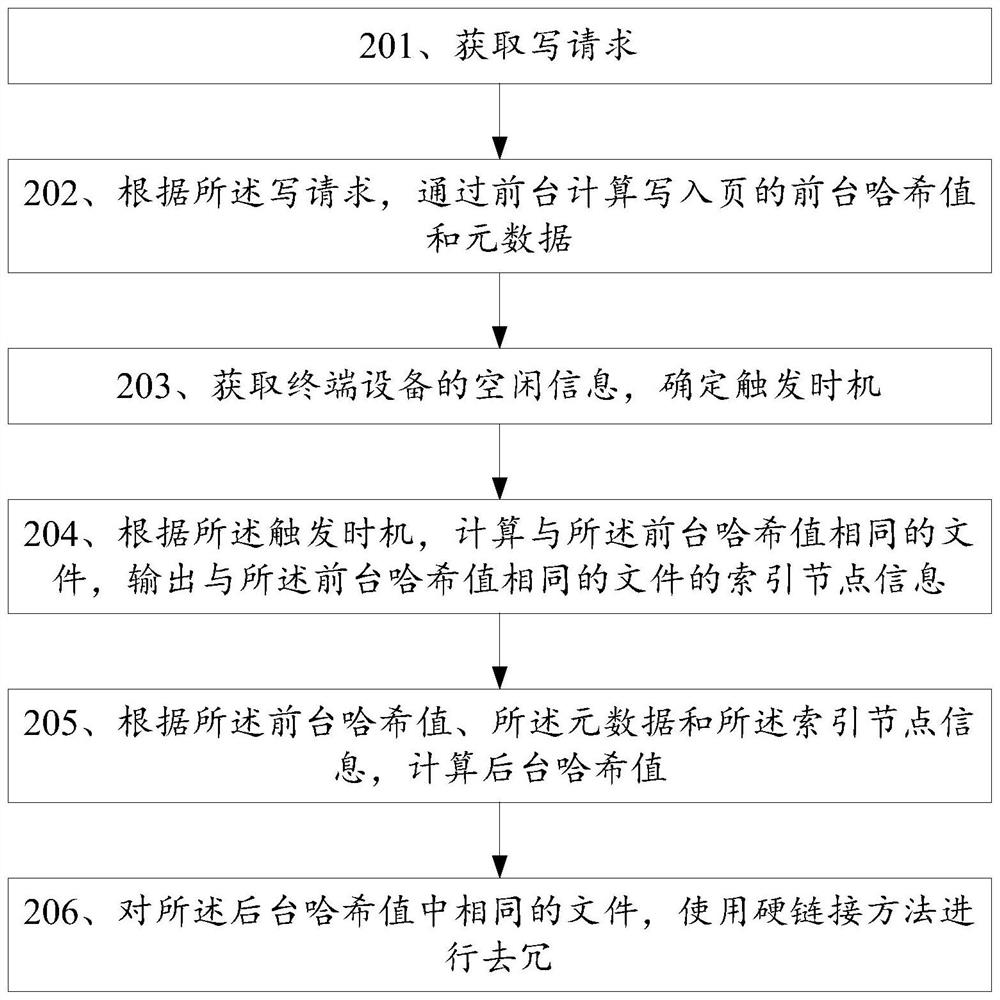
[0033] Embodiments of the present application provide a method, terminal device, and storage medium for de-duplicating files on a terminal device, which are used to eliminate redundant files generated by a user when using the terminal device, and also reduce the time required for the de-duplication process.
[0034] In order to make those skilled in the art better understand the solutions of the present application, the technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application. Obviously, the described embodiments are only a part of the present application. examples, but not all examples. Based on the embodiments in this application, all should belong to the scope of protection of this application.
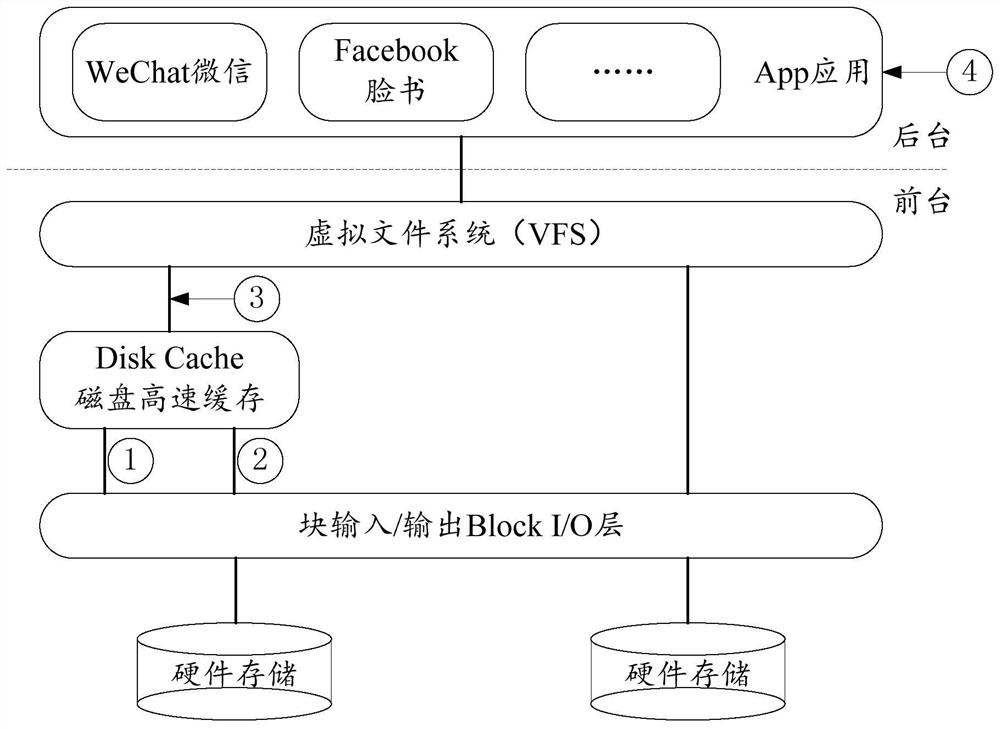
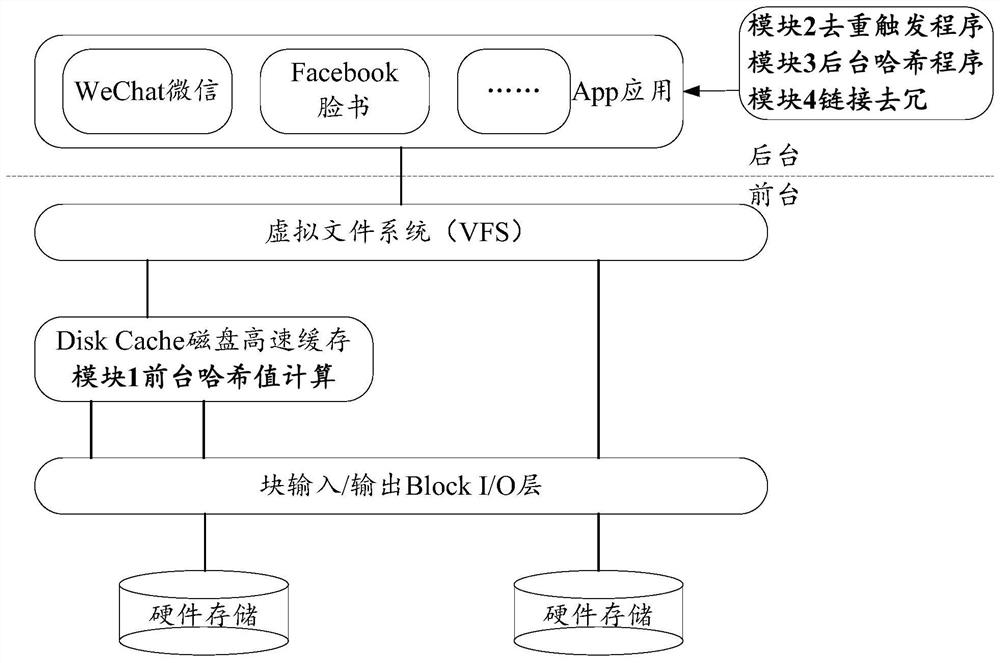
[0035] Since the redundant program involves the reading and writing process of files, this scenario involves each application (Application, App) application in the backgrou...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap