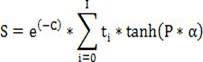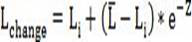Network security situation awareness method based on artificial intelligence
A technology of situational awareness and network security, which is applied in the directions of secure communication devices, energy consumption reduction, advanced technology, etc., can solve the problems of ineffective allocation of resources, large IP uplink traffic due to the number of bandwidth resource connections, and large bandwidth resource encroachment, etc., to achieve Realize the effect of network security situation awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to further illustrate the technical means and effects adopted by the present invention to achieve the predetermined purpose of the invention, the following describes an artificial intelligence-based network security situational awareness method proposed by the present invention with reference to the accompanying drawings and preferred embodiments, and its specific implementation The mode, structure, features and efficacy are described in detail as follows. In the following description, different "one embodiment" or "another embodiment" are not necessarily referring to the same embodiment. Furthermore, the particular features, structures, or characteristics in one or more embodiments may be combined in any suitable form.
[0036] Unless otherwise defined, all technical and scientific terms used herein have the same meaning as commonly understood by one of ordinary skill in the art to which this invention belongs.
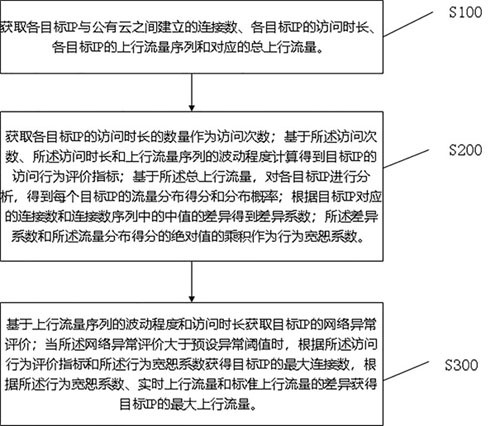
[0037]The embodiment of the present invention ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com