System attack protection method supported by CPU hardware
A technology supported by hardware and operating system, applied in the direction of preventing unauthorized use of memory, protecting storage content from loss, etc., can solve problems such as inflexibility and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
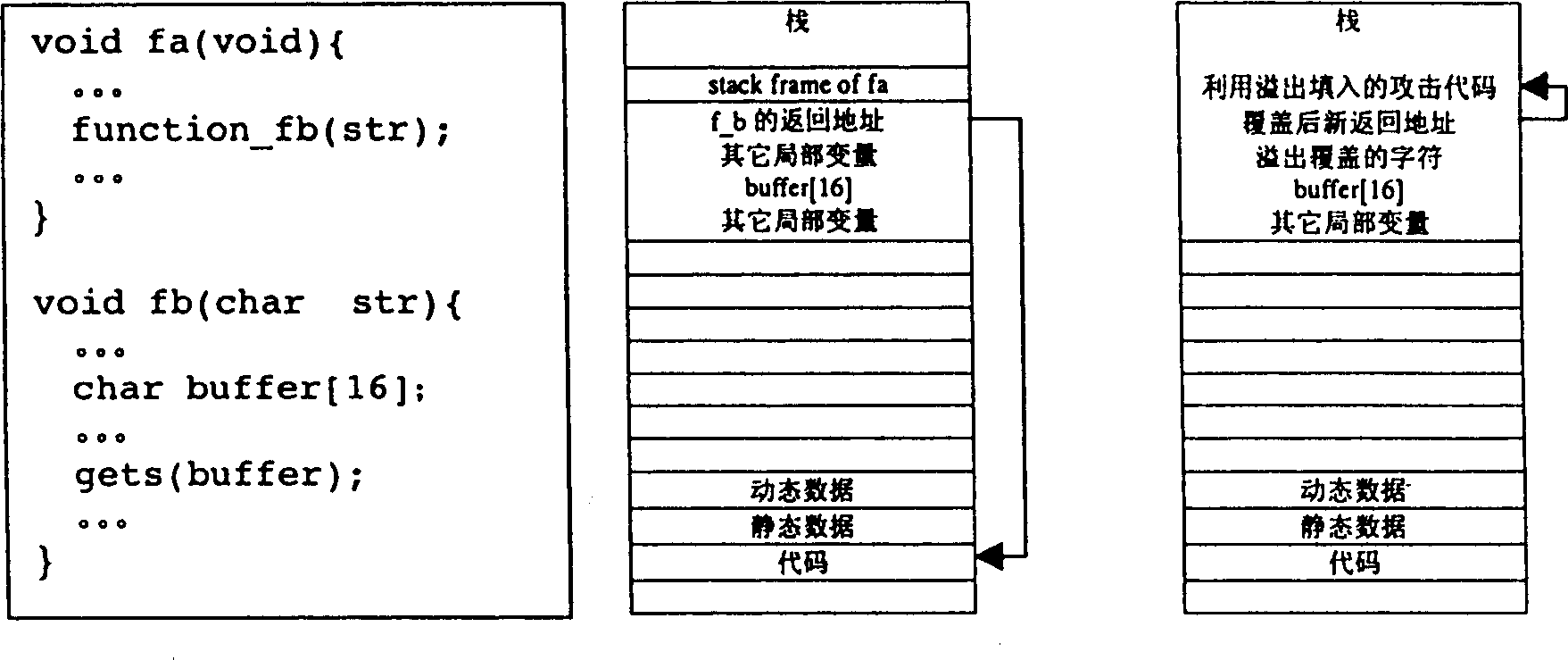
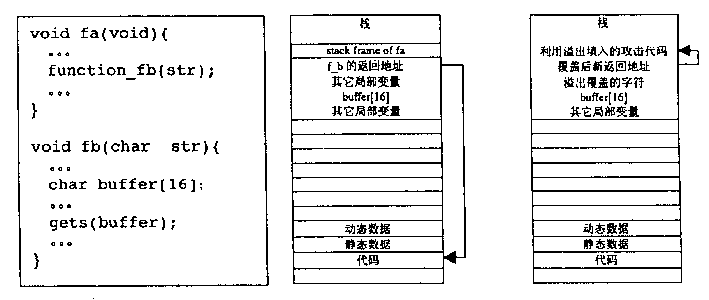
[0019] The present invention is specifically implemented for MIPS R4000 compatible CPU (referring to (1) SGI / MIPS.MIPS R4000 Microprocessor User's Manual, 1996. (2) Dominic Sweetman.See MIPSRun.Morgan Kaufmann Publishers Inc.1999.) and Linux operating system , which will be described in detail below.
[0020] To execute a certain instruction, the CPU must first fetch the instruction from the memory. Therefore, the executable permission to control a certain address can be realized through the MMU component when fetching the instruction. In order to provide maximum flexibility, the present invention provides two types of CPU hardware supporting executable permission control.
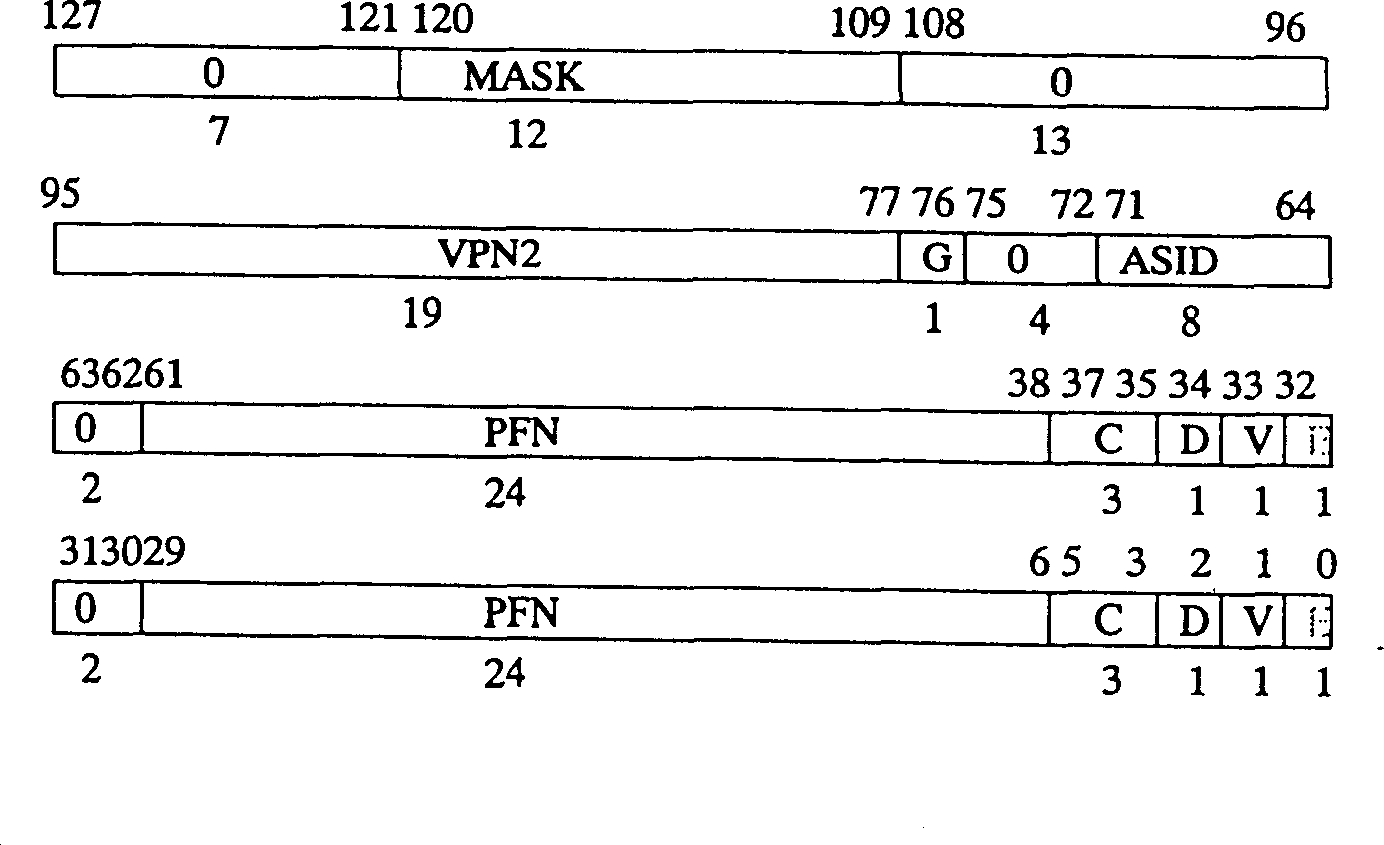
[0021] One is a segmented control hardware. Two control registers, ProtMask and ProtAddr, are added to the control register group of the MIPS CPU to allow the system to control the range of virtual addresses that can be fetched. ProtMask specifies the address bit to check when fetching instructions: the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com