Method of locking network delocking and number burglary for PHS mobile phone
A technology for locking the network and mobile phones, which is applied in the field of restricting and unblocking PHS mobile phone network access, which can solve problems such as unresolved and inability to re-enter the network for use, and achieve the effect of facilitating after-sales problems and solutions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
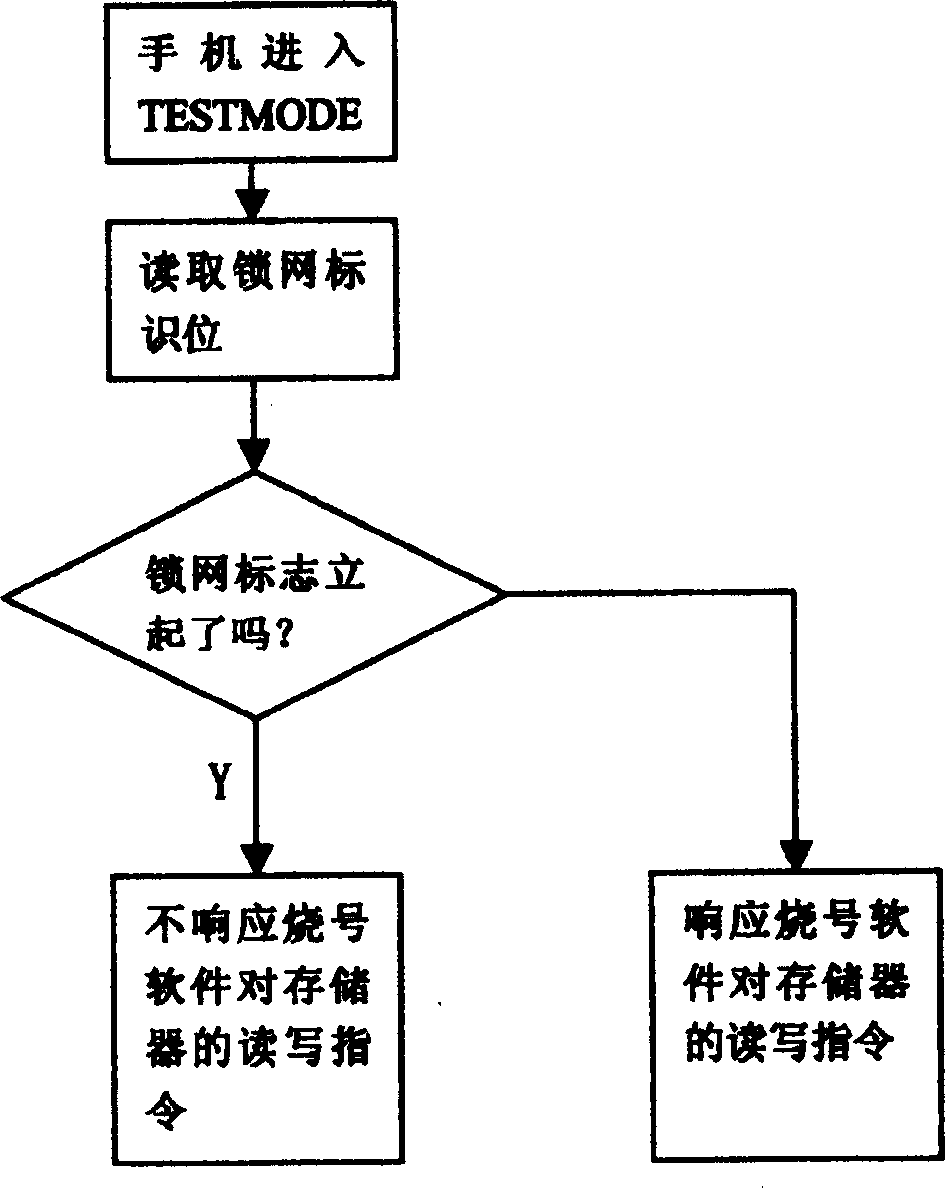
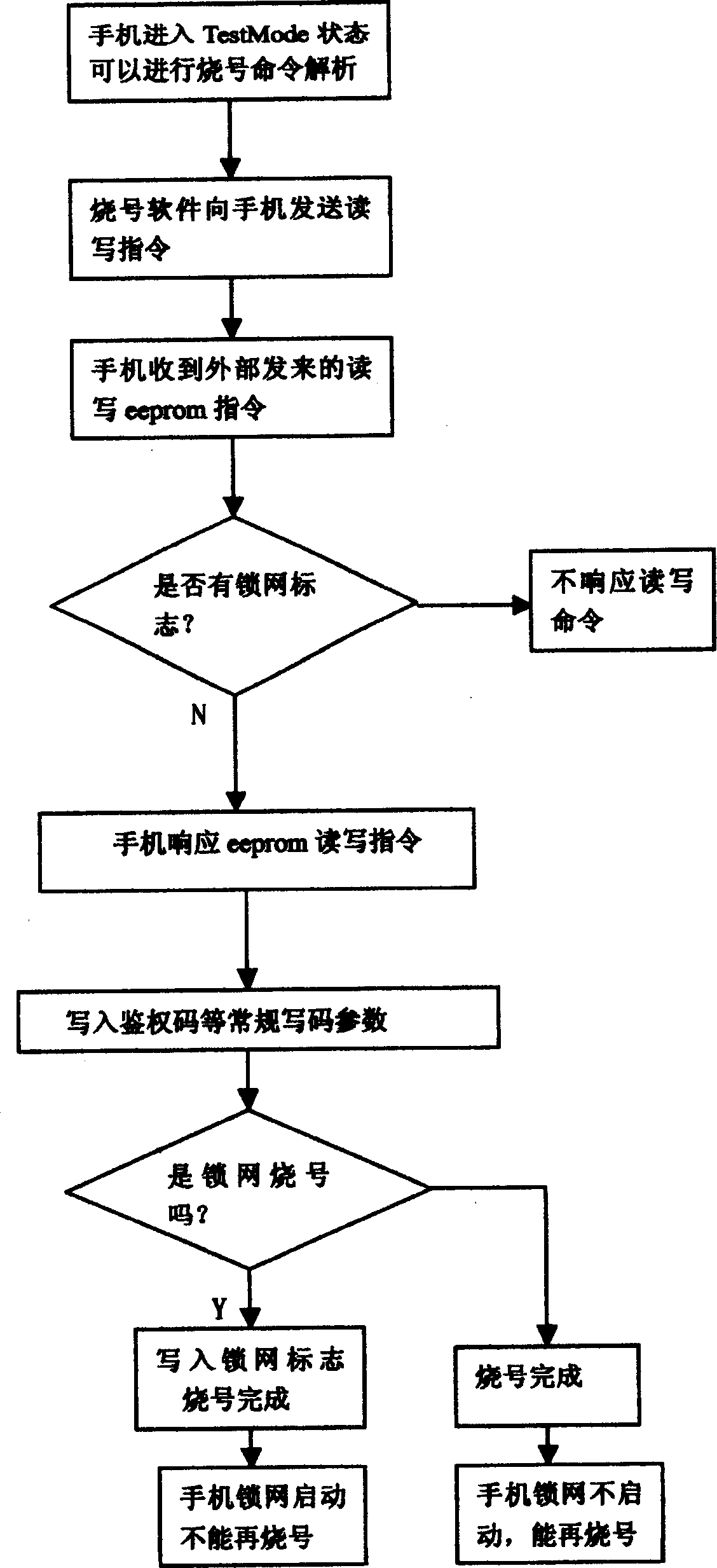
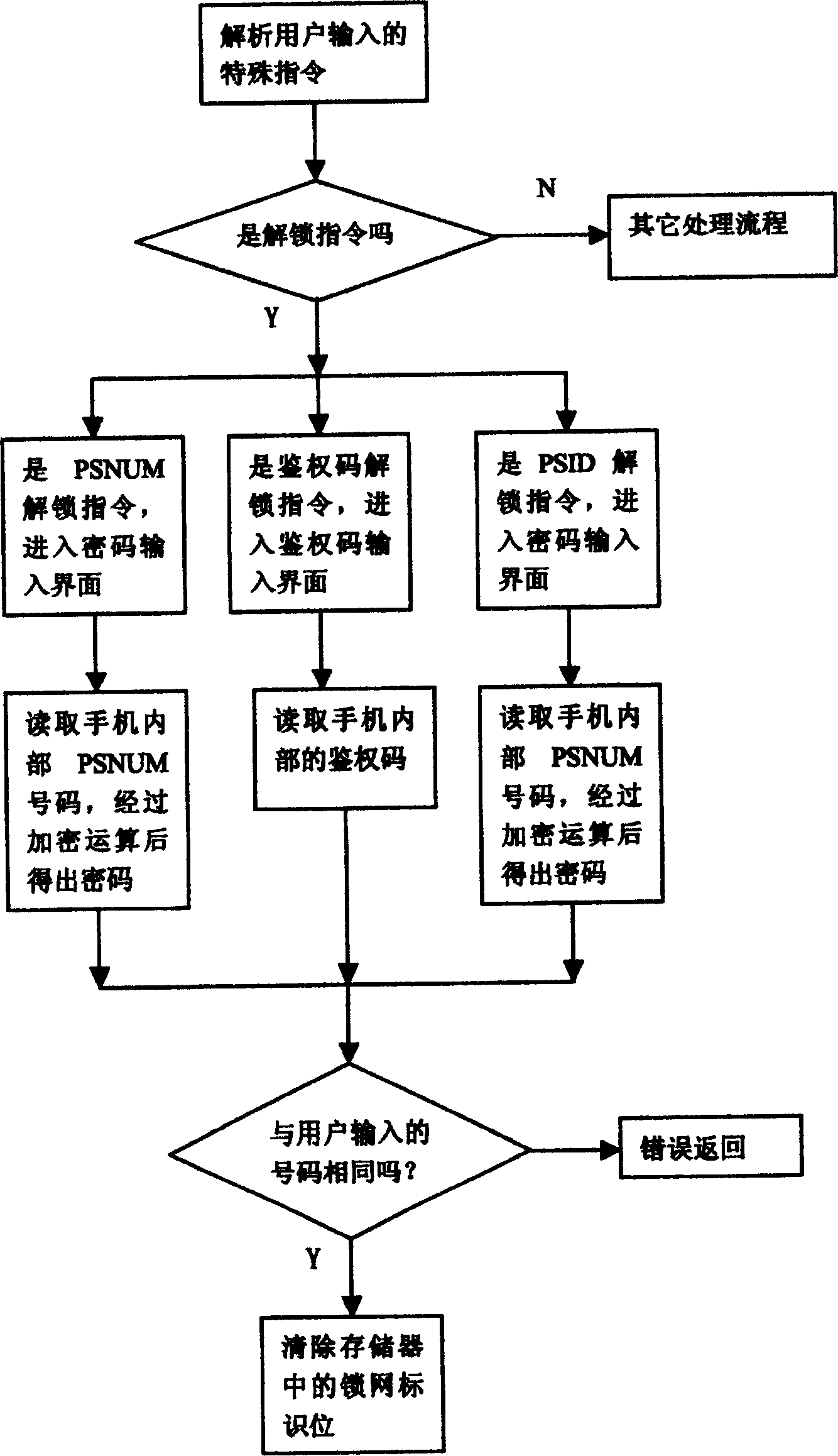
[0022] Now when the PHS mobile phone is burning the number, the general mobile phone will enter a special mode, which we call "TestMode" (called test mode or burning mode in Chinese), such as figure 1 . After entering this mode, the mobile phone software is already running. When receiving the burning software, read and write to the memory (here we refer to eeprom, Electrically Erasable & Programmable ROM, Electrically Erasable Programmable Read-Only Memory, or other storage media) When the command is issued, the mobile phone software will analyze the read and write command, and the mobile phone software will specifically read and write the memory, and then return to the state of reading and writing; in this way, the burning software can write some parameters into the mobile phone to complete Code writing work on mobile phones. In order to lock the network, we can determine an address bit of the eeprom as the network lock flag. When the mobile phone enters the number burning m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com