Method for realizing network accreditation by encipher clobber generating
A network identity and authentication method technology, which is applied in the field of network identity authentication by encryption system, which can solve the problems of short user passwords, infrequent replacement, and insecure identity authentication methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] The implementation steps of the identity authentication method are illustrated below in conjunction with the accompanying drawings:
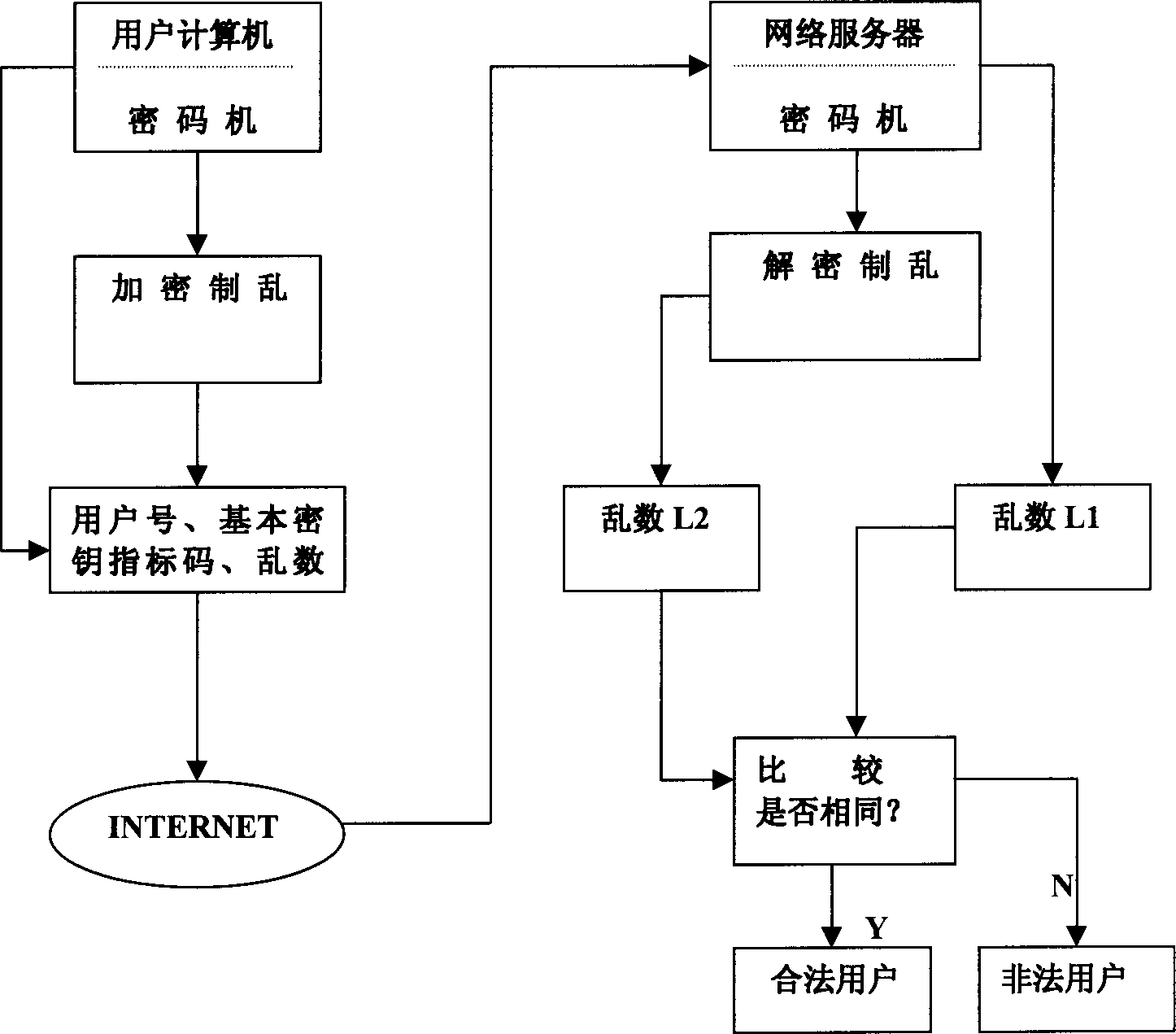
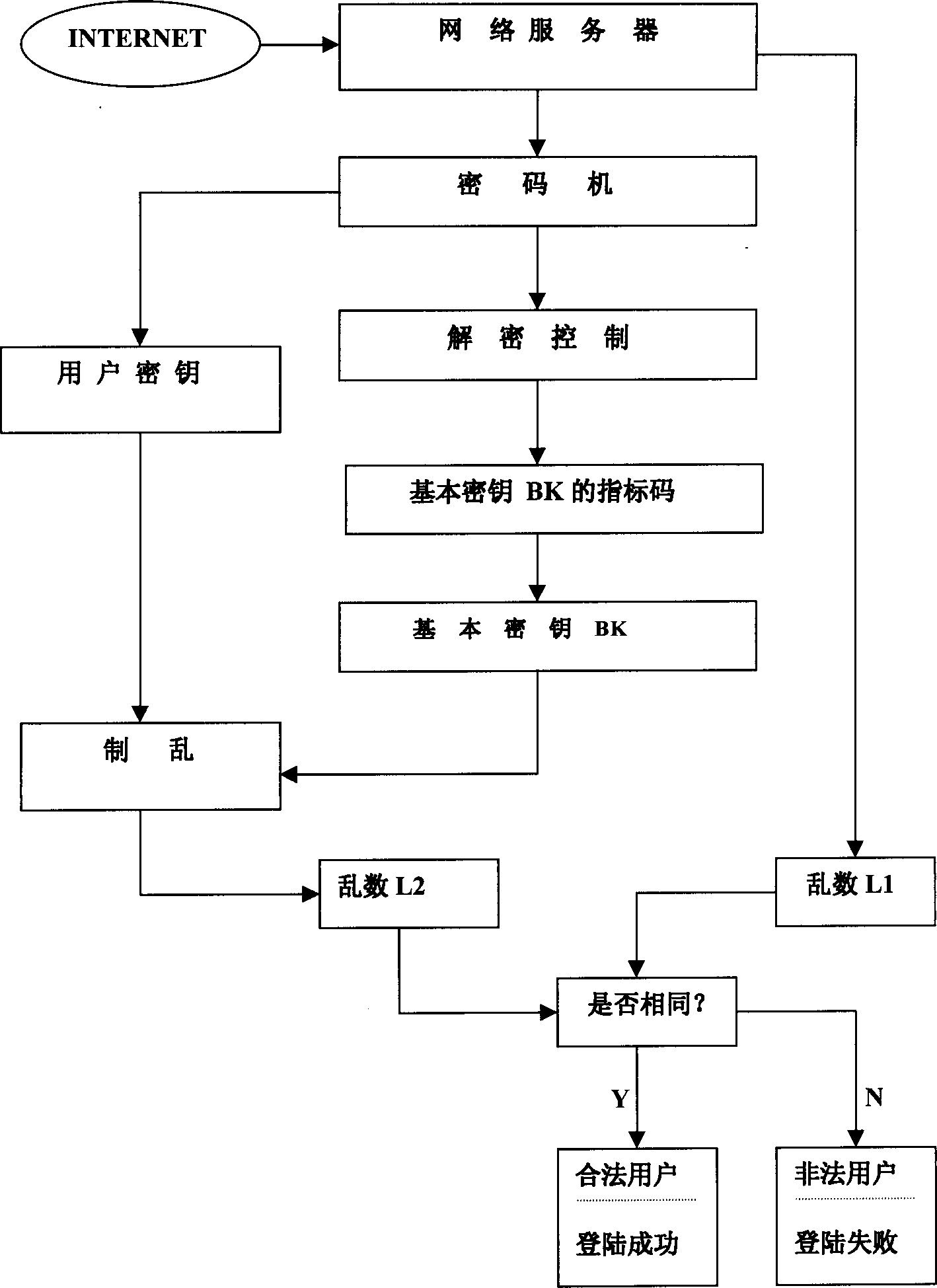
[0014] figure 1 : It shows that the user computer uses the cipher machine at this end to encrypt the scramble, and transmits the user number, the index code of the basic key BK and the random number to the network server through the network, and the network server uses the same key to decrypt the scramble through the cipher machine at this end. Random, compare the random numbers generated at both ends to achieve identity authentication.
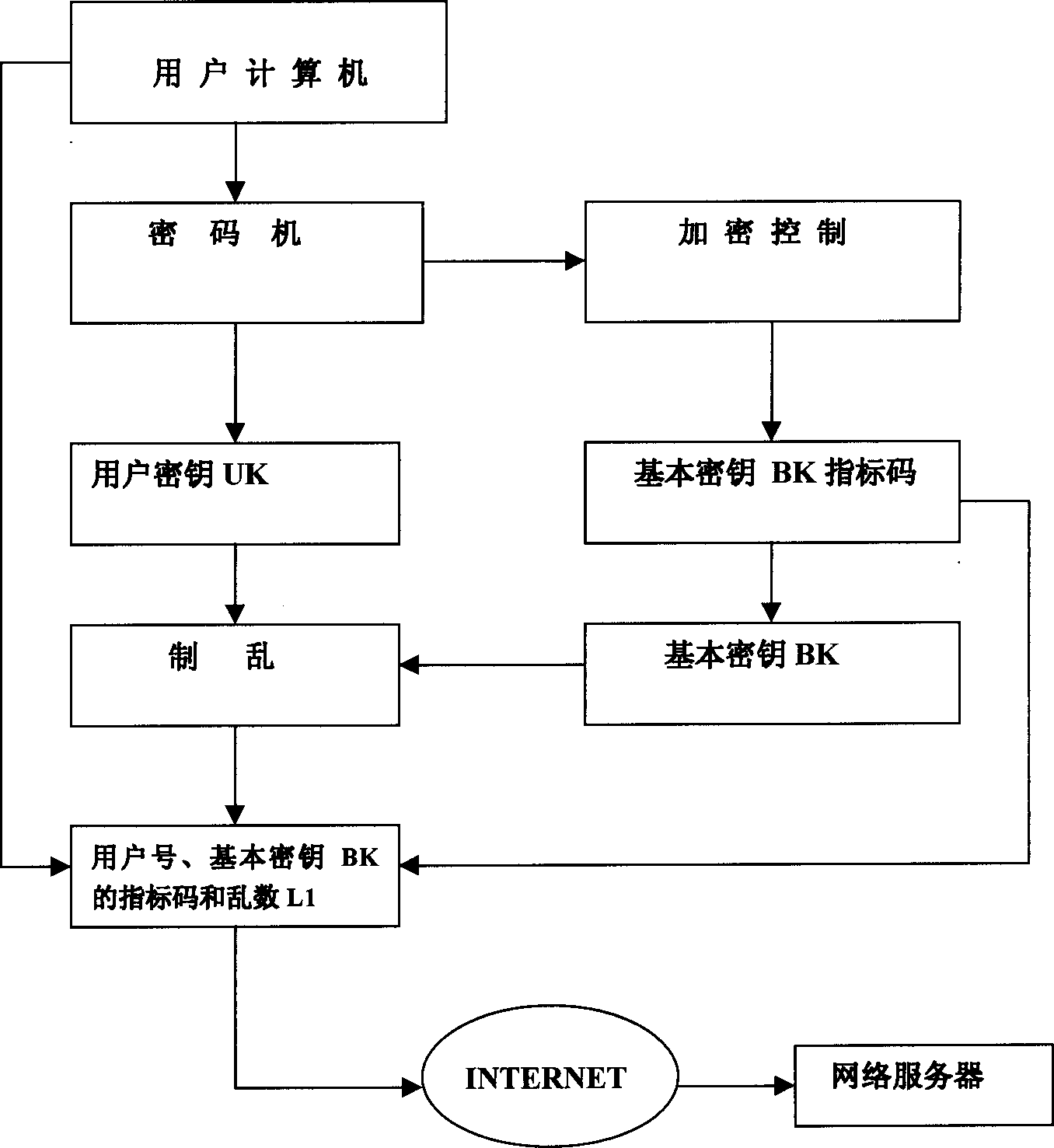
[0015] figure 2 : Explain that the user computer controls the cipher machine at this end to input the user key UK into the scrambling system of the cipher machine, and then generate the index code of the basic key BK through the encryption control system, then select BK from the index code, and input it into the scrambling system System, UK and BK are combined to generate the initial state in the chao...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com