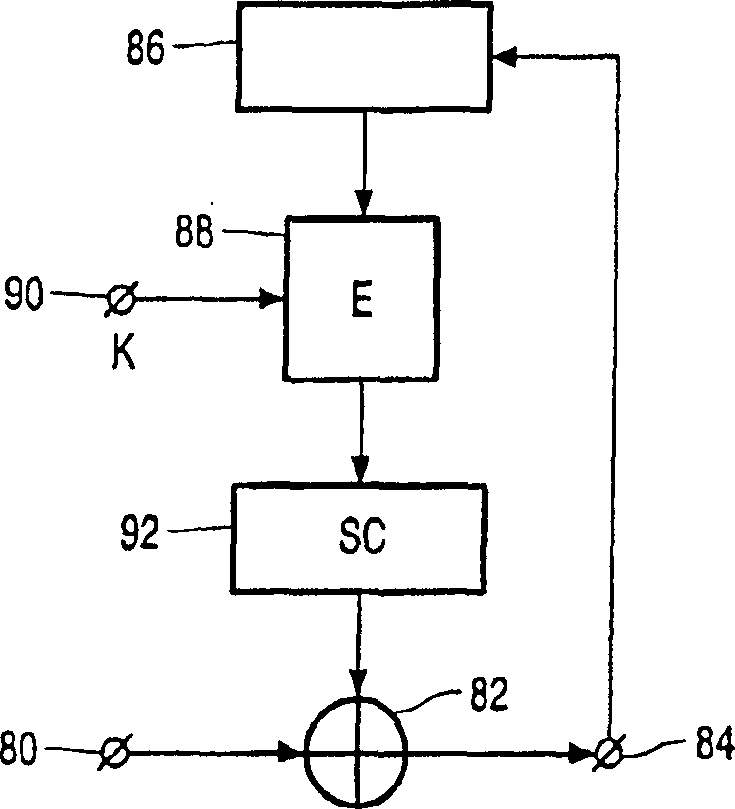
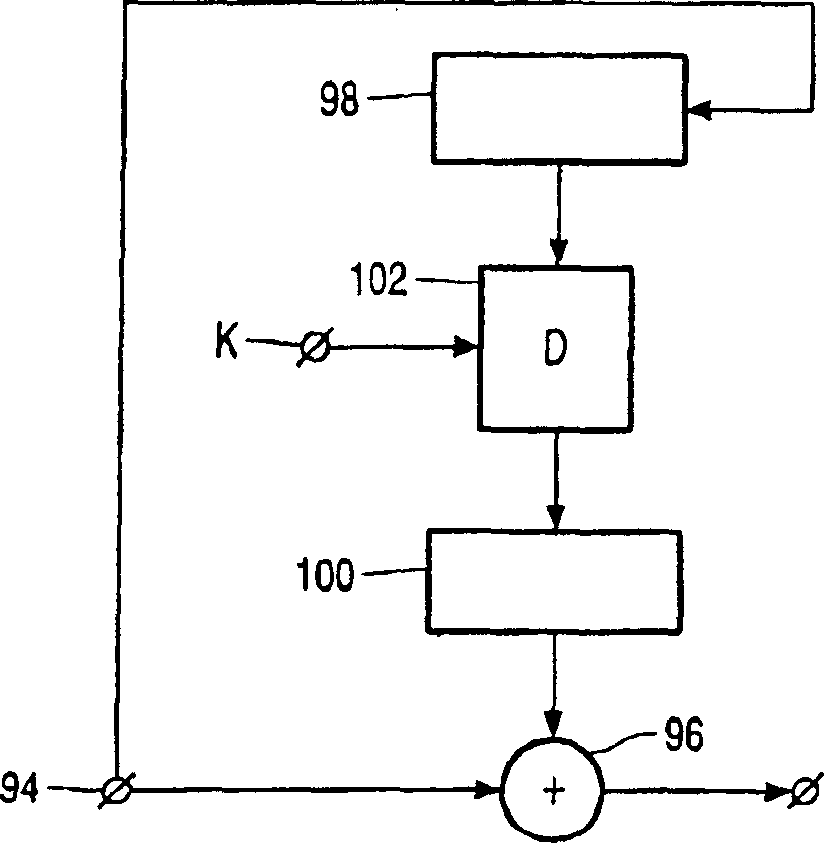
Streamcipher information redundant in next packet of encrypted frame
A stream encryption, encryption key technology, applied in secure communication, synchronous send/receive encryption equipment, encryption device with shift register/memory, etc., can solve problems such as reducing content quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
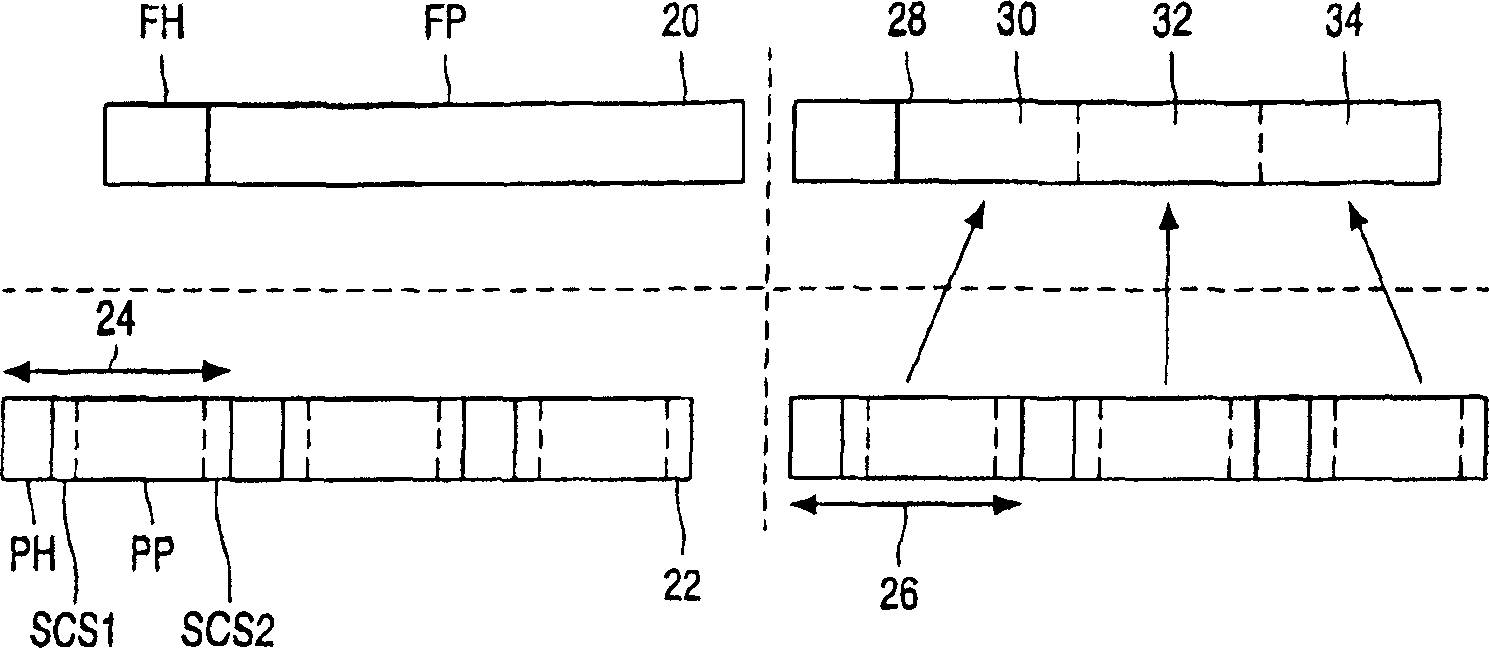
[0013] figure 1 The encryption format used by the present invention is described. The top row relates to user information such as audio or video, and consists of a frame 20 comprising a frame header FH and a frame payload FP. This sequence of frames does not need to have a consistent amount of payload data, but its size will depend on the degree of information compression applied. In addition, for the frame structure shown, the format may include an application-dependent subframe format, which is not further shown in the subframe format diagram, but there is no notable division in the further encryption / decryption process considered below. In some cases, further frame division (dividing of the frame) can be formed on various subframes. These subframes may refer to another information structure related to the application to which the transmitted payload refers.
[0014] In the second line, the frame 20 is mapped onto a sequence 22 of three transport packets, this number bei...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com