Safety Service fee metering method
A technology for security services and billing methods, applied in the field of communication and information security, it can solve the problem that users cannot customize security services according to security requirements, and achieve the effect of deterministic accuracy and simple realization.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
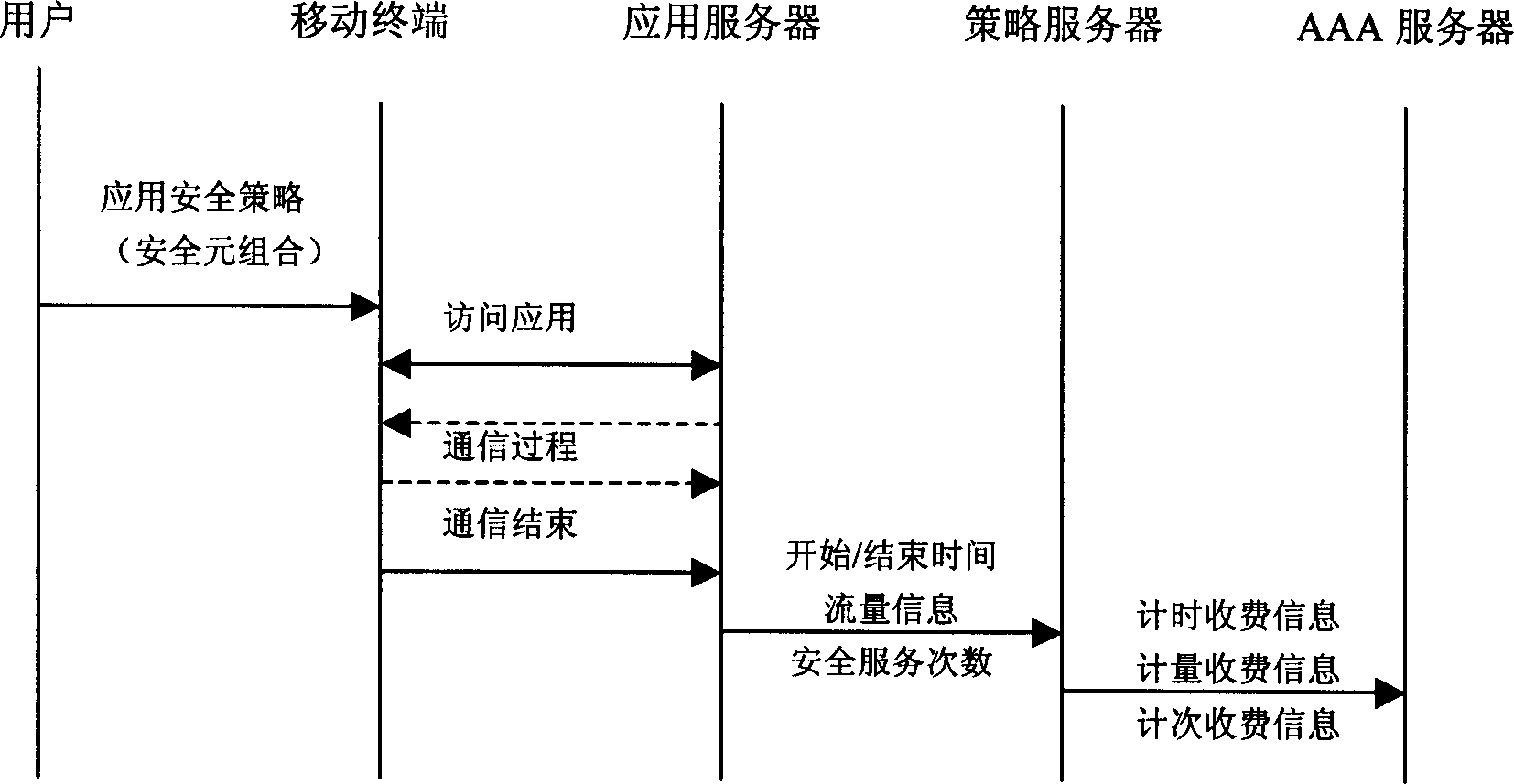
[0032] The application and implementation of the secure service charging method will be described below in conjunction with the illustrations.
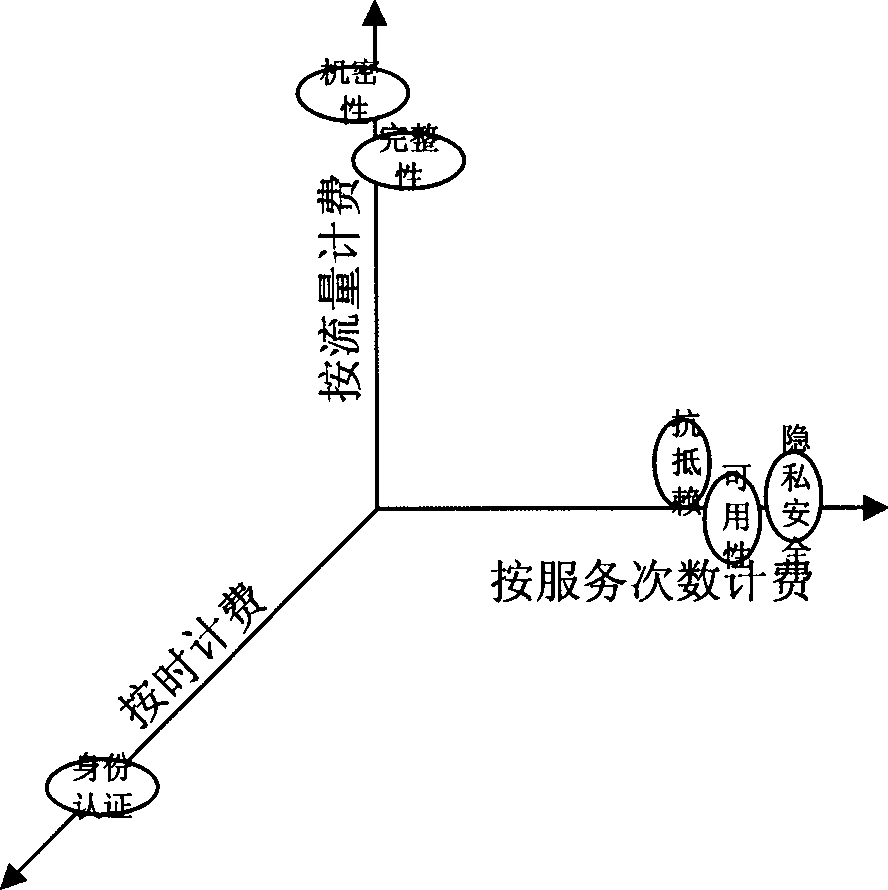
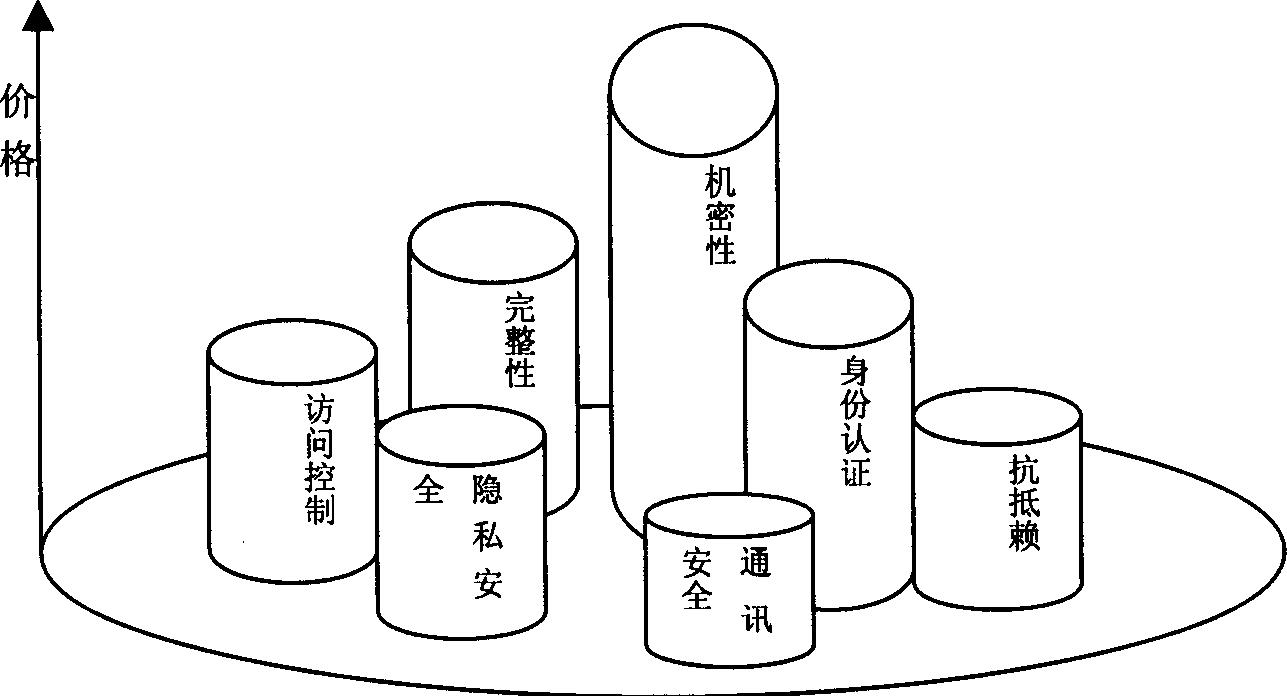
[0033] Security elements can be classified according to various attributes, but the following goals must be achieved: the division of security elements is non-overlapping, that is, there is no security element belonging to two categories; the classification of security elements is complete, that is, any Safe Meta always finds its own category. figure 1 It is based on the common billing methods of AAA servers—traffic, duration, and number of communications to divide the security element. Considering that the policy controller cannot authorize and control the specific objects accessed by the user (by the ASP authorization that provides the service and Control), so the "Access Control" security element is not counted. Similarly, "communication security" refers to the prevention of line eavesdropping during communication, and does not in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com