Generation and validation of Dieffie-Hellman digital signatures
A digital signature and large number technology, applied in the field of encryption, can solve problems such as mathematical calculation attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
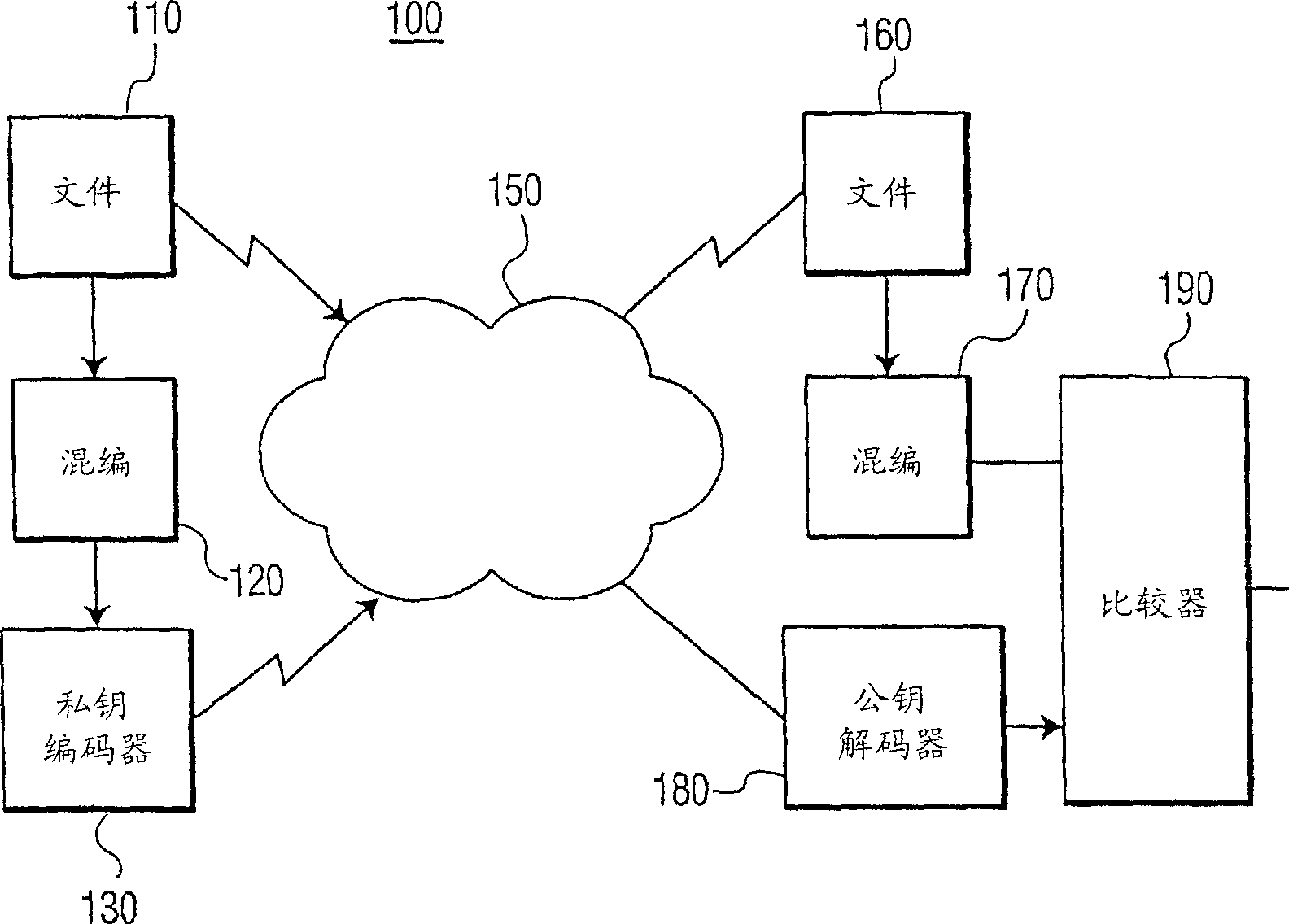
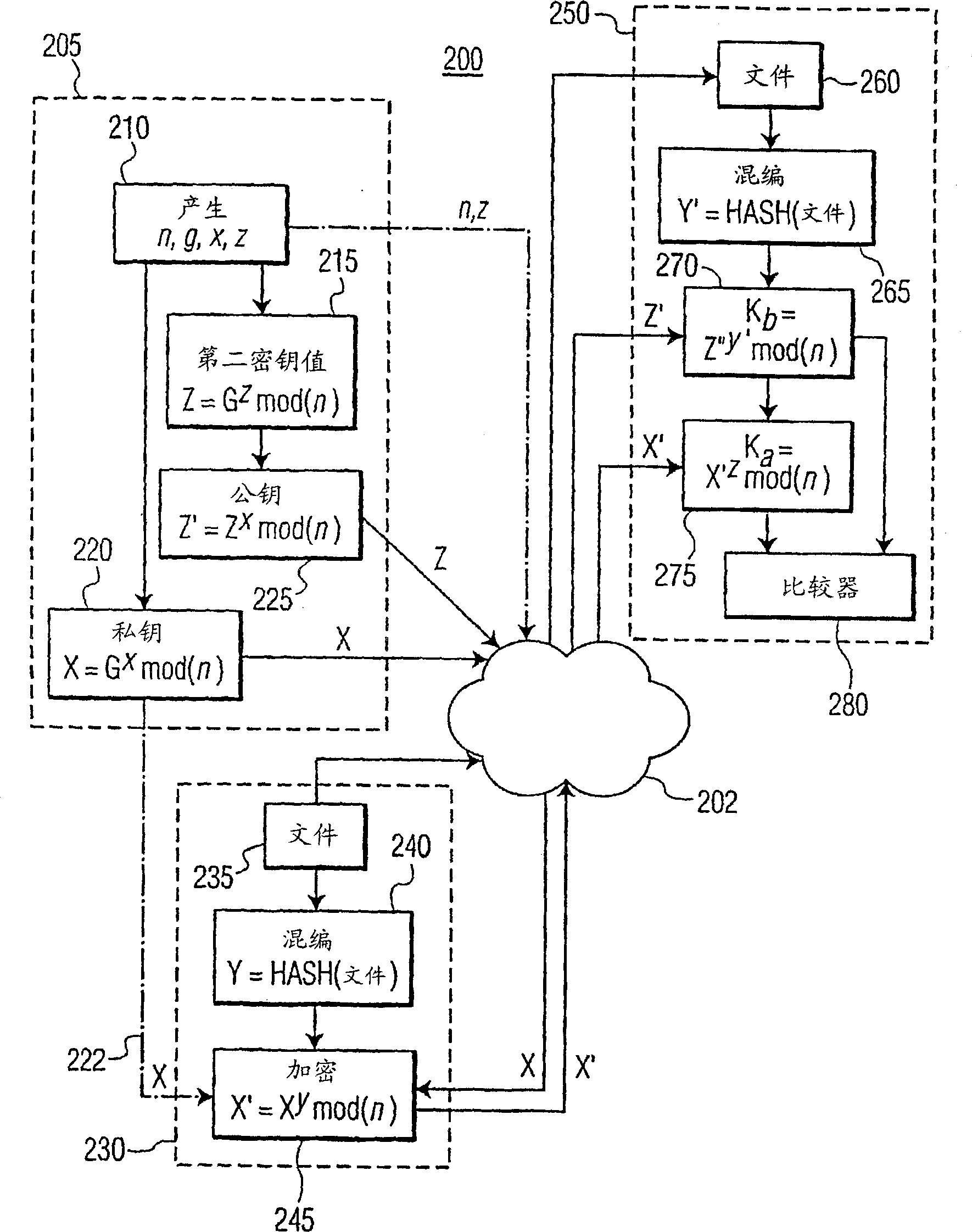
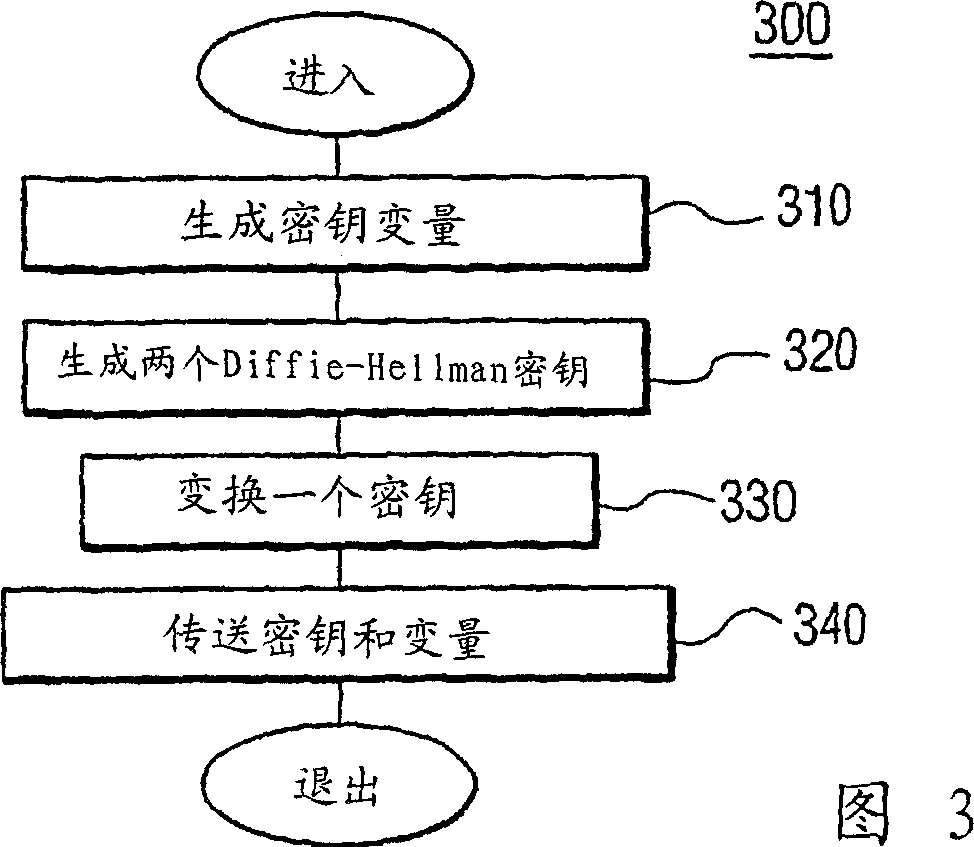
[0013] The use of the Diffie-Hellman algorithm in cryptography has been extended to three parties, as described in " Applied Cryptography 2 nd edition "(Bruce Schneier (Ed.), p.514), as explained more fully in this encryption technique, each party transmits elements of a key provided by the other party. Each party establishes a key for the session based on the provided information Determine the public encryption key. For example, assuming that each party knows the encryption variables g and n, where n is a large prime number, it can be shown that the following procedure can be used to form a three-party key exchange:
[0014] "A" randomly selects a large integer x, forming X = g x mod(n), and transfer X to "B";
[0015] "B" randomly selects a large integer y, forming Y=g y mod(n), and transfer Y to "C"; and
[0016] "C" randomly selects a large integer z, forming Z=g z mod(n), and transfer Z to "A";
[0017] "A" then yields the transformation of Z as Z'=Z x mod(n),...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap