The method of safe certification service
A service method and security access technology, applied in the field of preventing leakage of button input passwords of access control locking devices, can solve problems such as inability to intercept information, and achieve the effects of expanding the scope of passwords, preventing phishing, and preventing authentication attempts
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
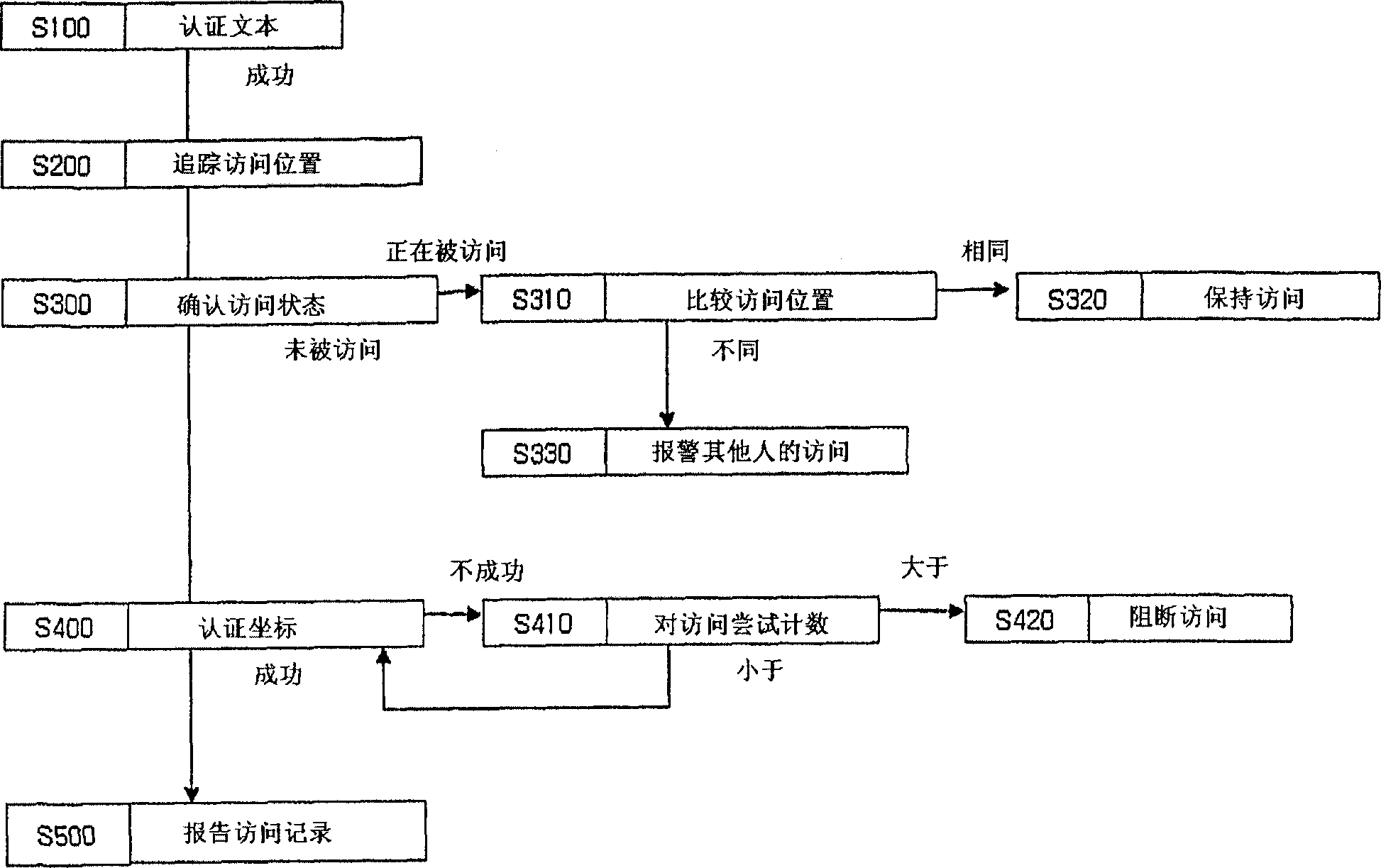
[0020] The present invention consists of four main steps. The individual steps are now described.
[0021] figure 1 It is a flow chart showing the main program flow of the present invention.
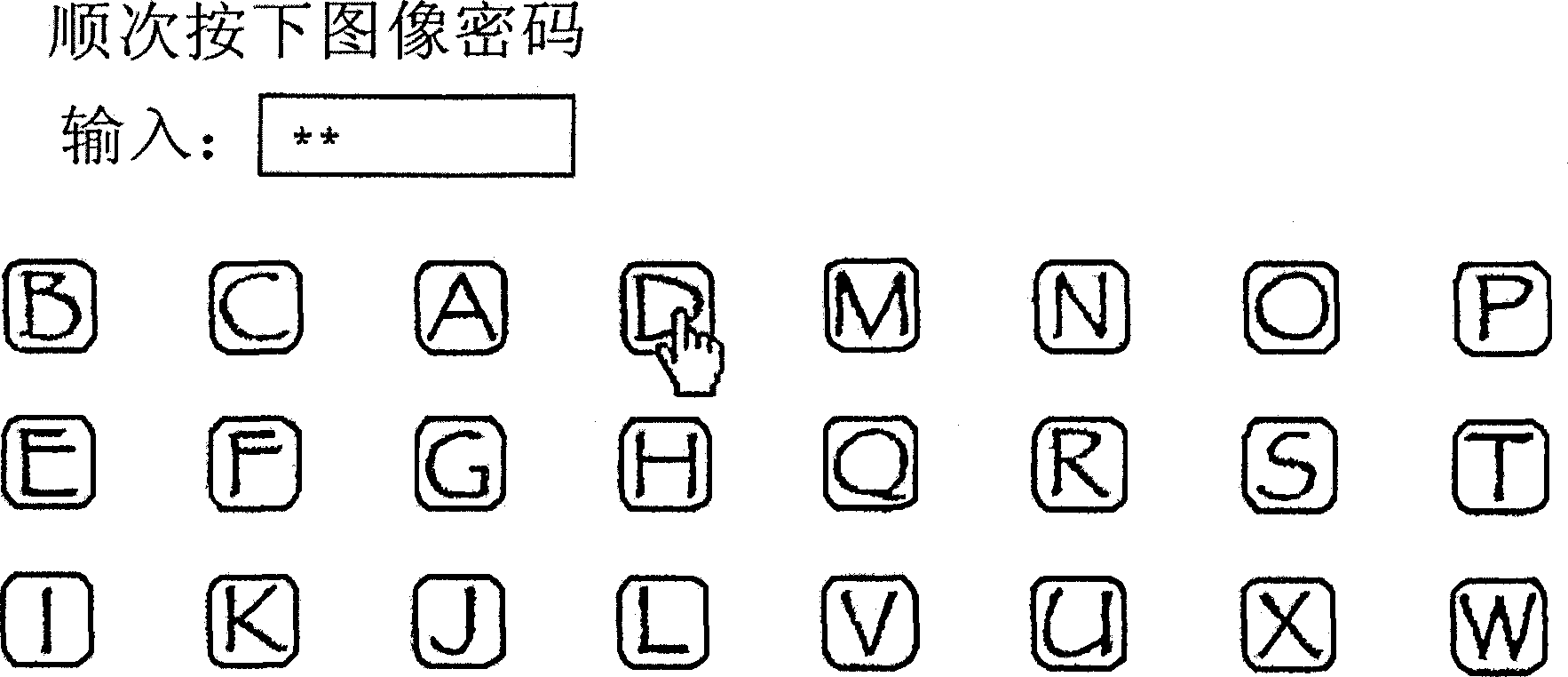
[0022] 1. Authentication step by text input (S100)
[0023] This step is the most common method of authenticating by keying in ID and password. Therefore, its detailed description is omitted here.
[0024] 2. Access location tracking step (S200)
[0025] If the user passes the authentication step using text input, flow proceeds to the web page for the authentication step by coordinate input. At this time, a JAVA program (JAVA applet) executing the access location tracking function is automatically downloaded into the user's computer, and then the user's current access location is reported to the server. The server stores this information.
[0026] A description of the technology for tracking access locations by JAVA programs can be found in Korean Patent Application No. 10-2001-00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com