Method for identification
A technology of identification and statistics, applied in the field of transaction processing, can solve problems such as identity abuse
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention is discussed below by describing preferred embodiments and referring to the accompanying drawings. However, a person skilled in the art will realize other applications and modifications within the scope of the invention as defined in the appended independent claims.
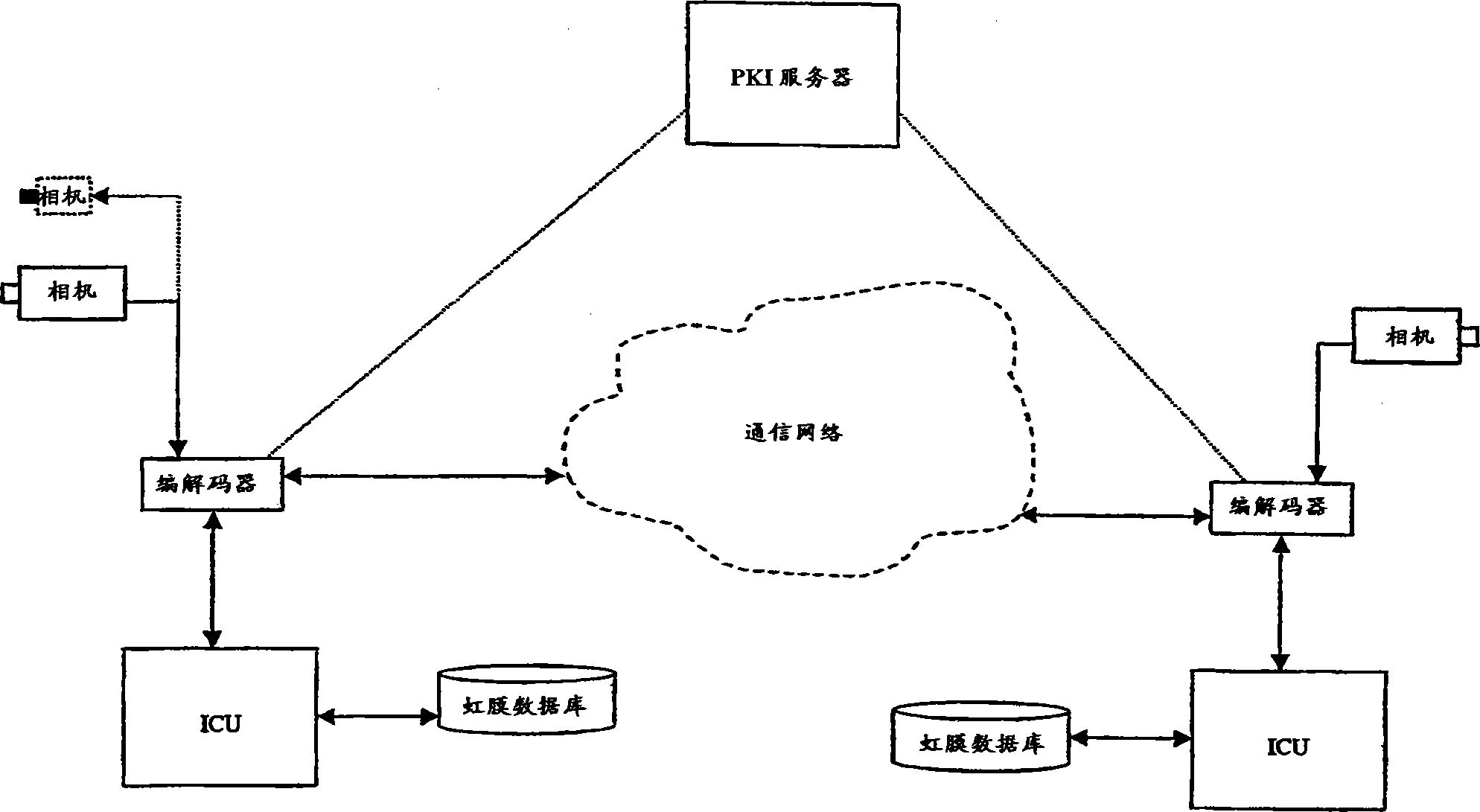
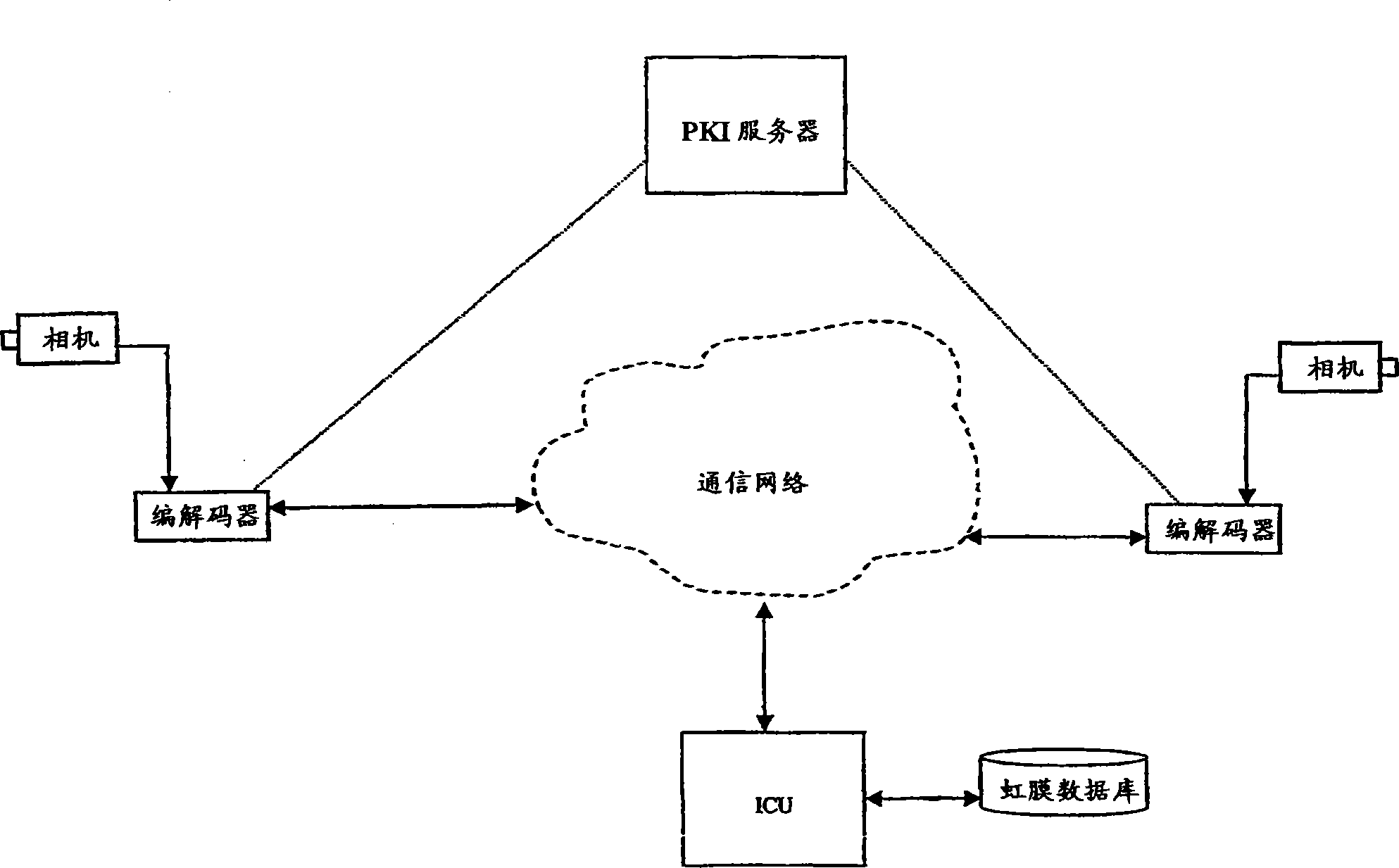
[0020] According to a preferred embodiment of the present invention, biometric uniqueness and PKI robustness and reliability are combined for conferencing applications.
[0021] The field of biometrics includes all human patterns that are individually unique and identifiable. The most common patterns used for identification are fingerprints, face patterns and irises. The great advantage of biometrics is that unique patterns are always carried and attached to the body and remain constant throughout life.
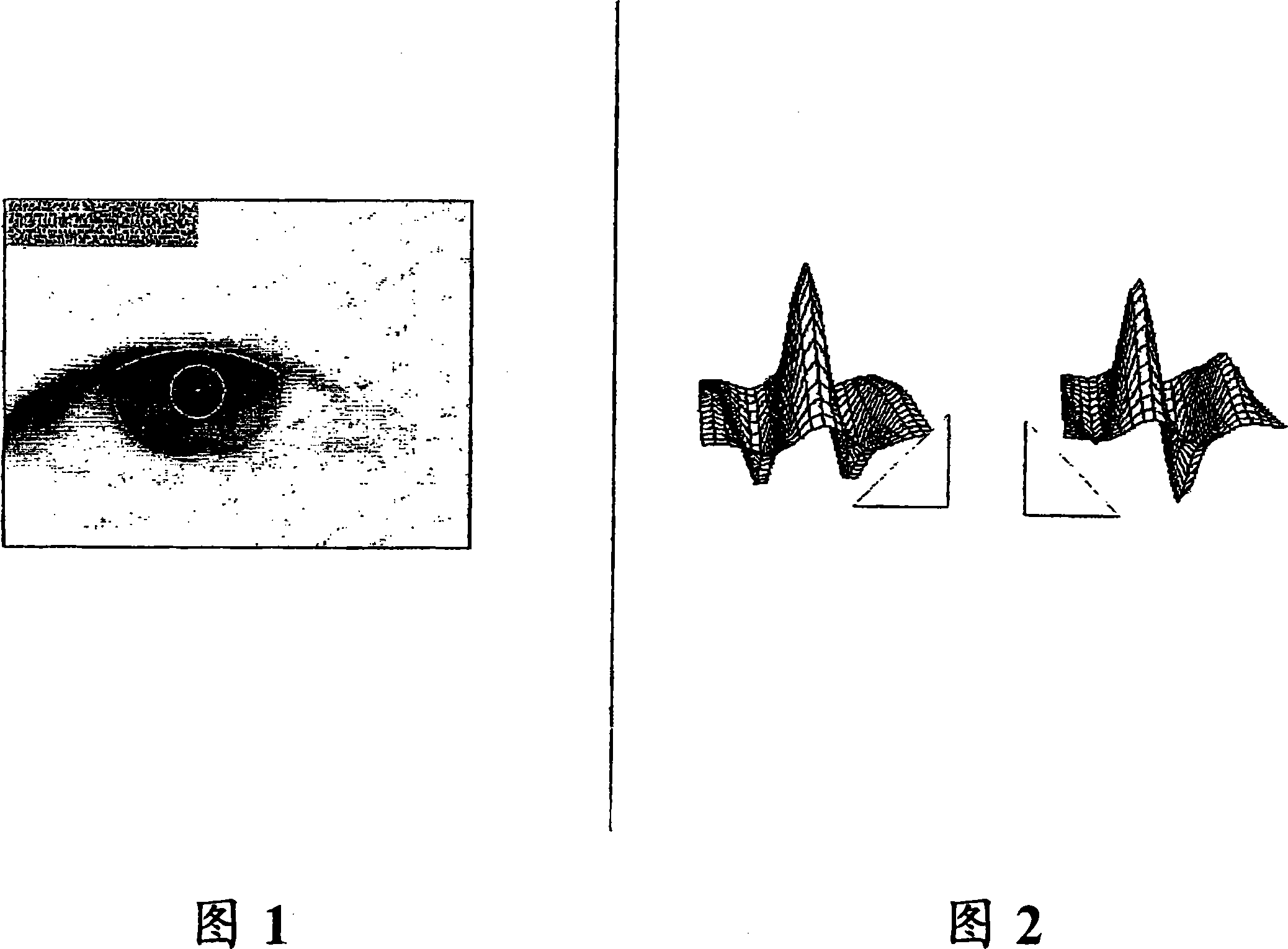
[0022] According to one aspect of the invention, iris recognition is used to identify participants in a video conference. Iris recognition itself combines computer vision, pattern...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com