Monitoring and controlling applications executing in a computing node
a computing node and monitoring system technology, applied in computing, error detection/correction, instruments, etc., can solve the problems of insufficient code testing, insufficient protection against byzantine errors, and insufficient built-in sandboxing features of conventional process monitoring tools
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example 1
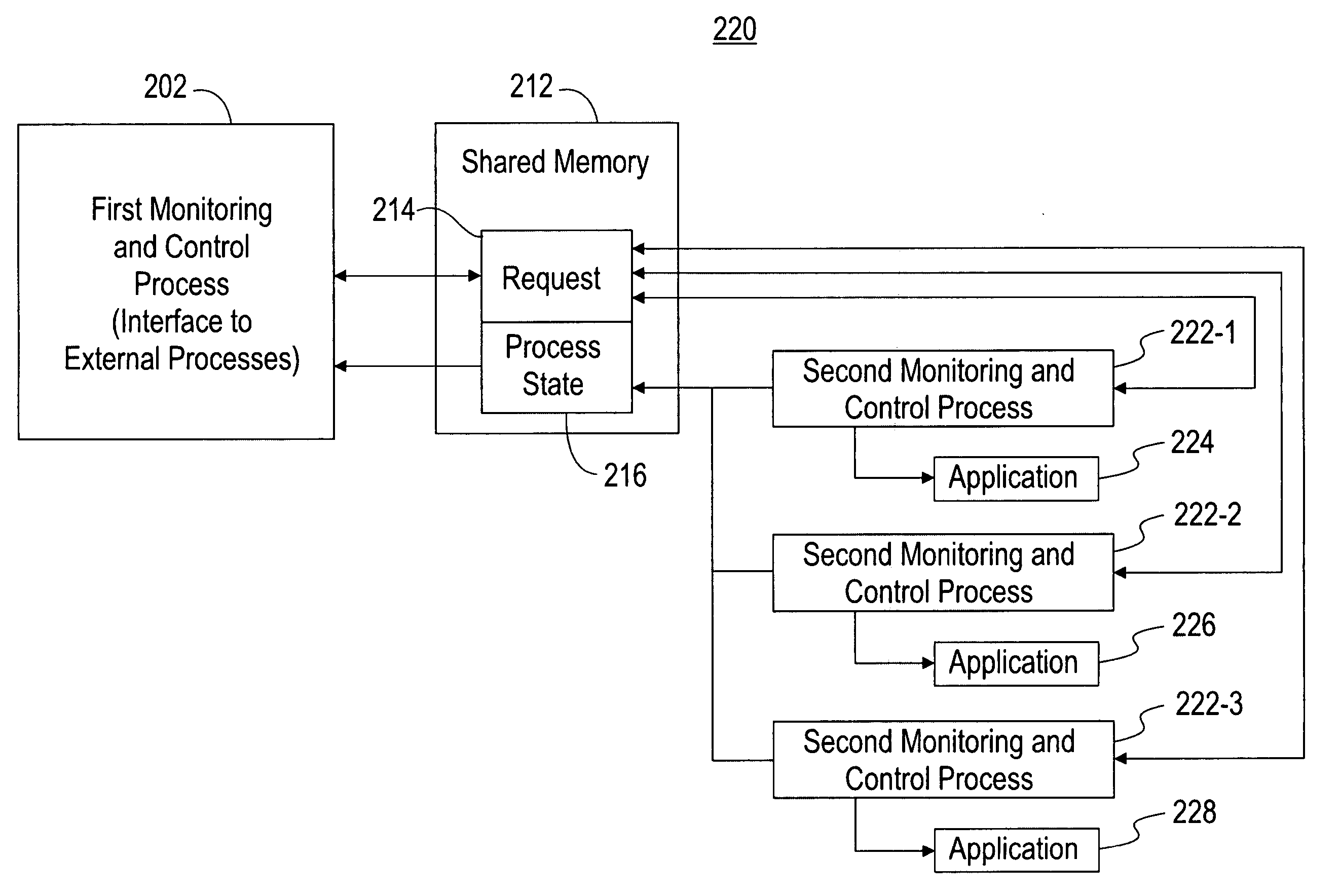
[0071] As one example of the monitoring and control process of FIG. 3, a configuration of computing node 240 is provided. In this example, each reference numeral corresponds to a reference numeral in FIG. 2C, but it will be understood that the steps of this example can also be implemented in the computing node configuration of FIG. 2A or FIG. 2B. Computing node 240 executes untrusted application 244 and one other application 246. It will be understood that the other application can also be a trusted application such as application 248 or 250. The steps of an execution of an application are included in Example 2 presented below. Second process 242-1 functions as the parent application to the untrusted application 244. As a parent application, second process 242-1 is capable of obtaining a status of application 244. Computing node 240 also executes first process (i.e., status request process) 202 and second processes (i.e., control processes) 242-1 and 242-2.
[0072] In this example, a...
example 2
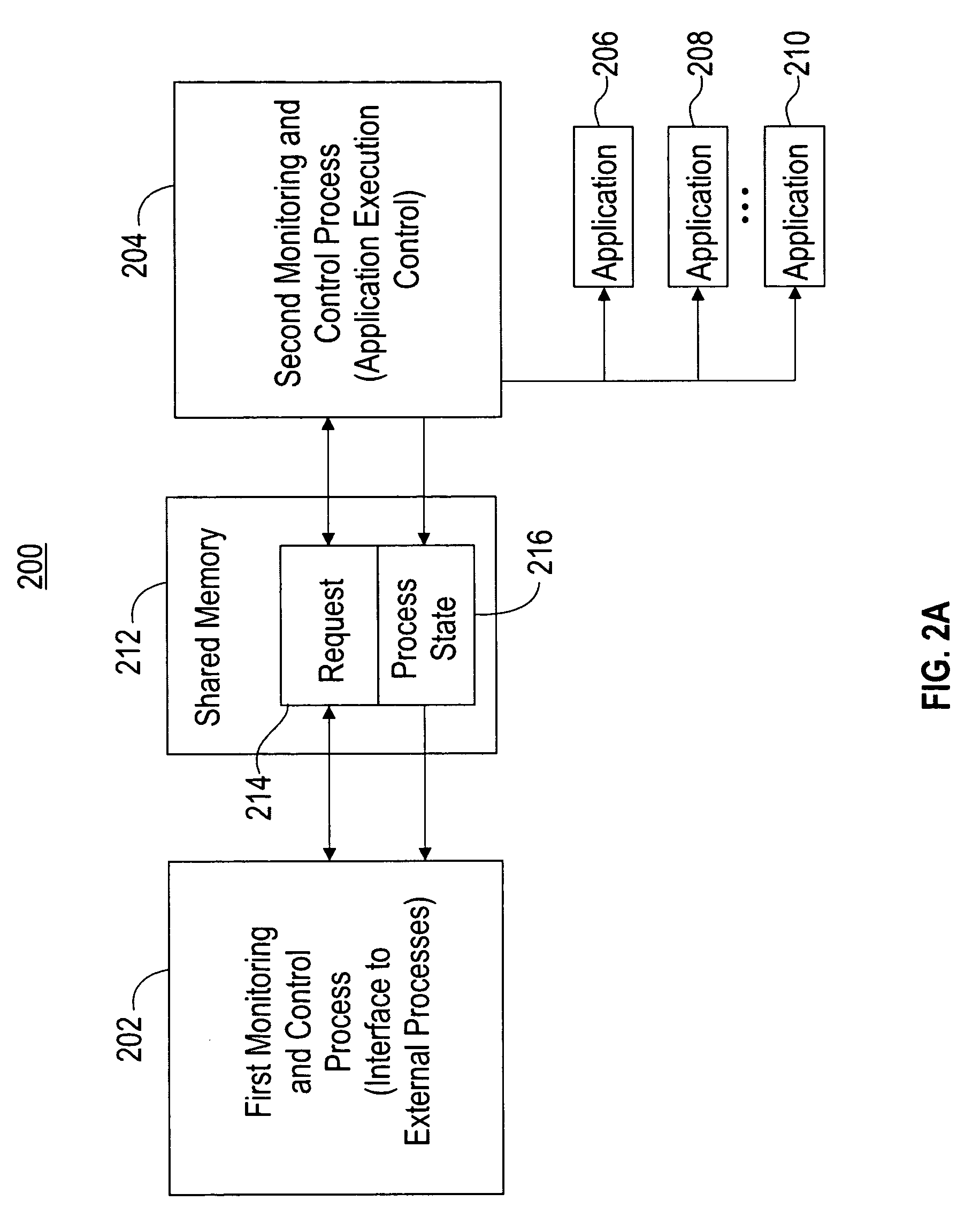
[0077]FIG. 4 is a flow chart of an exemplary process of executing an application on a computing node of FIGS. 2A, 2B or 2C, in accordance with embodiments of the present invention. In this example, reference numerals refer to components of FIG. 2B, and the application to be executed is application 224, but it will be understood that the steps in this example can also be implemented to execute an analogous application in the computing node configuration of FIG. 2A or FIG. 2C.
[0078] The application execution process begins at step 400. In step 402, first process 202 sends a start command message to second process 222-1 via request portion 214 of shared memory 212. The start command message indicates that an execution of application 224 is to be initiated. In step 404, second process 222-1 receives the start command message from request portion 214 of shared memory 212. In step 406, second process 222-1 utilizes a fork system to spawn off application 224. In step 408, second process 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com