Methods and apparatus for scoped role-based access control
a role-based access control and scope technology, applied in the field of information technology (it) systems, can solve problems such as the inability to distinguish roles across organizations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
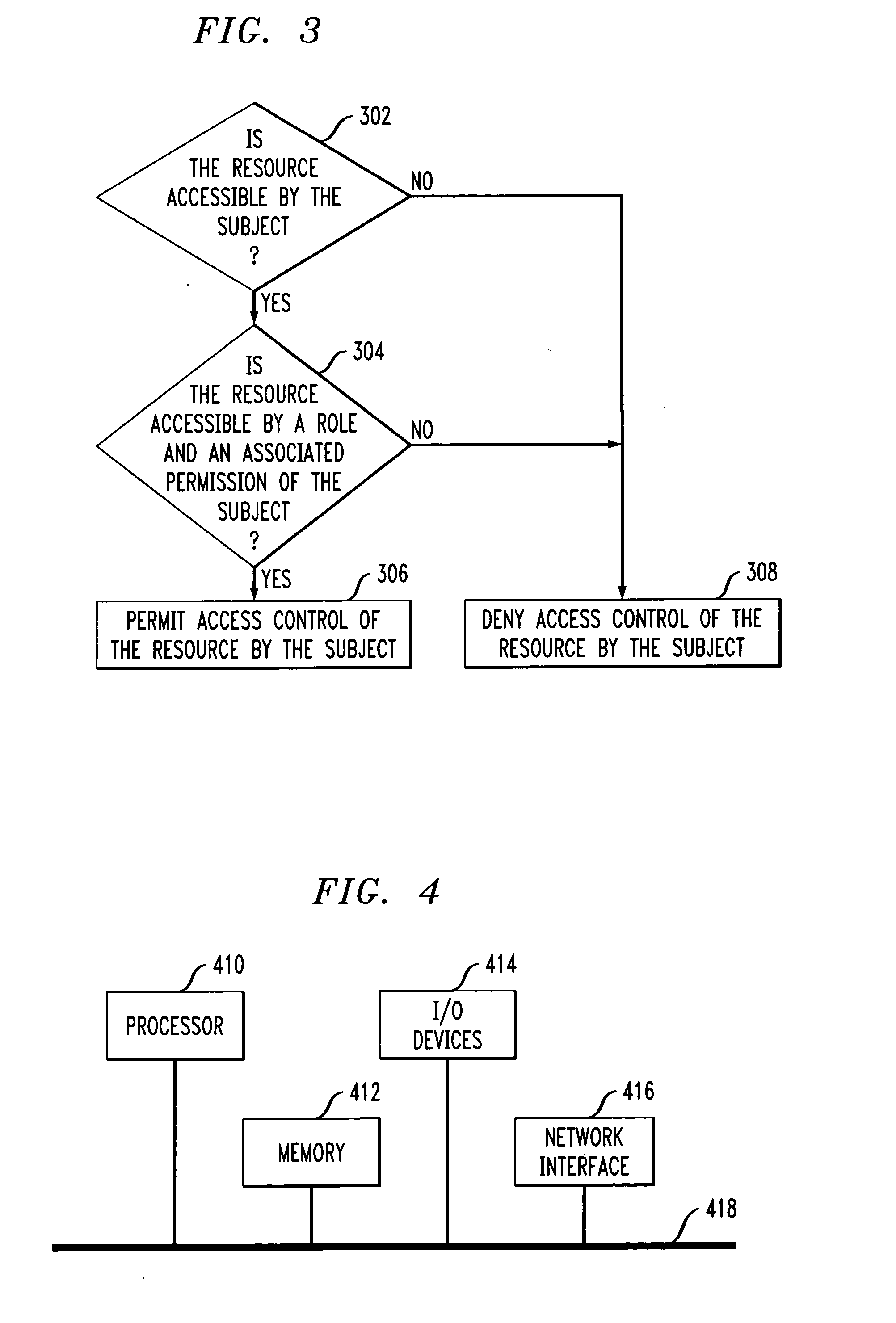
[0017]As will be illustrated in detail below, the embodiments of the present invention introduce techniques for providing scoped role-based access control of a resource by a subject in an access control system.
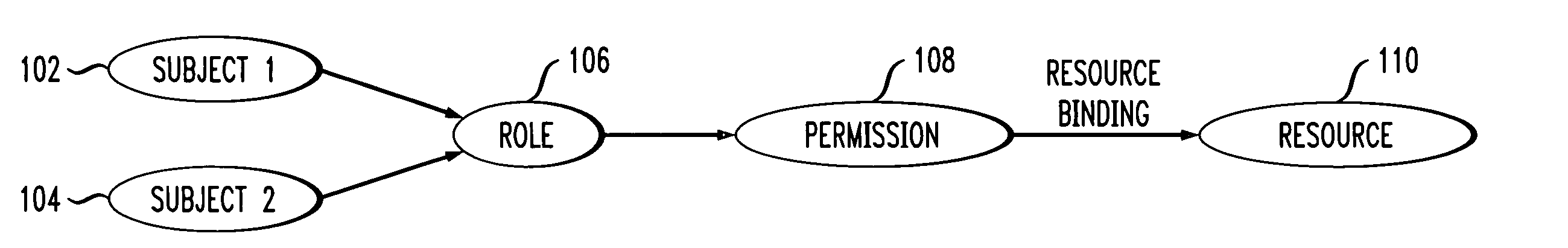
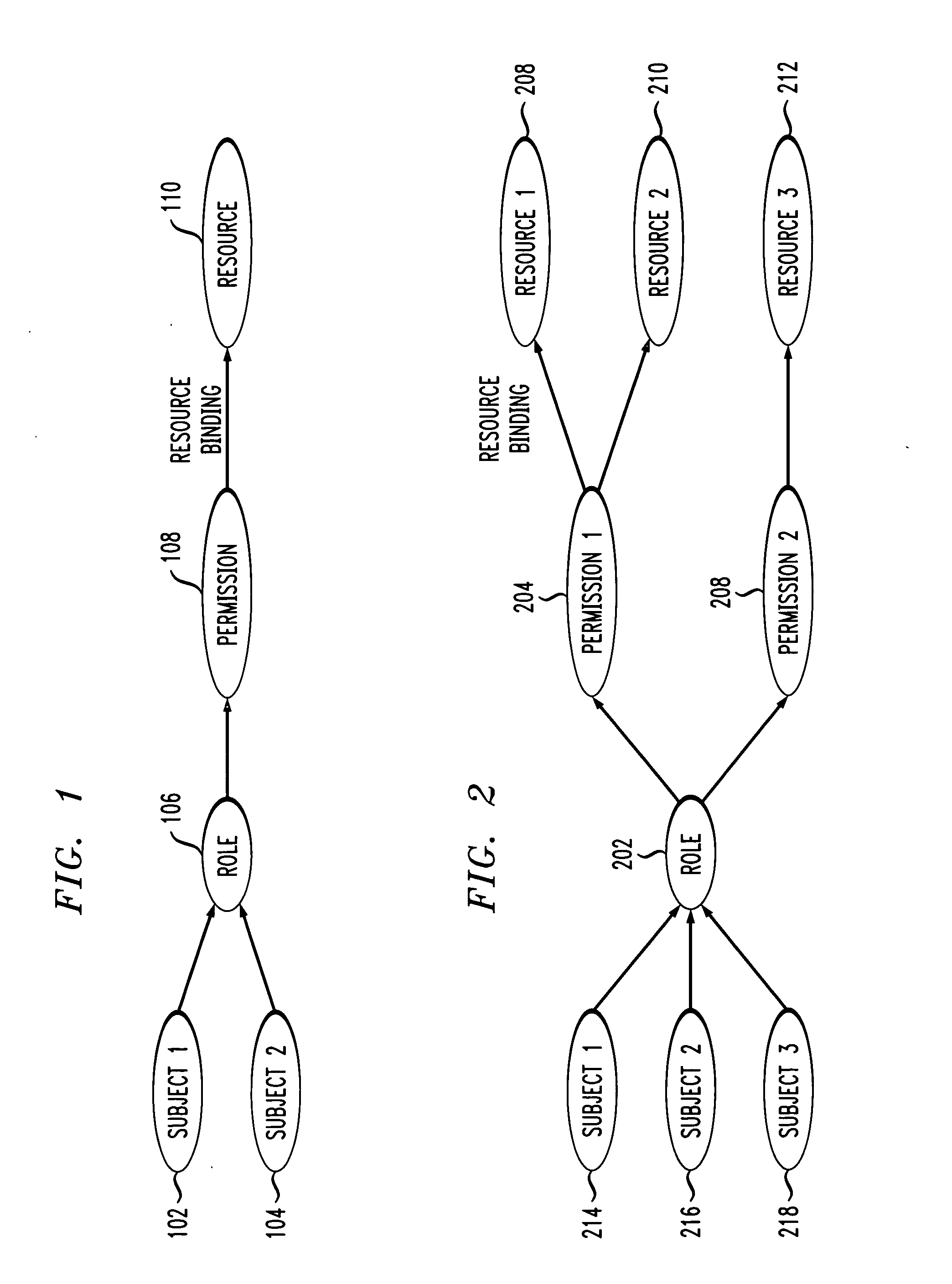
[0018]Referring initially to FIG. 1 a diagram illustrates a conventional RBAC system. Subject-1102 and Subject-2104 are assigned a role 106 for access to specific resources. Role 106 is assigned to a specific set of permissions 108, and the specific resources 110 are bound to this set of permissions 108.
[0019]Referring now to FIG. 2, a diagram illustrates a scoped RBAC system, according to an embodiment of the present invention. A role 202 is associated with multiple permission sets 204, 206. Then a scope is created to associate a set of resources 208, 210 with permission set 204. In the embodiment of FIG. 2, two such scopes are shown, in that resource 212 is associated with permission set 206. This scope conveys the permission a subject has when accessing the resource under t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com