Improved sub-tree access control in network architectures
An access control and data request technology, applied in instrumentation, computing, electrical digital data processing, etc., can solve problems such as limiting the flexibility of CSP operation equipment vendors, hardware does not tend to be adjusted economically, and spare capacity blocks cannot be effectively used by CSP.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Overview
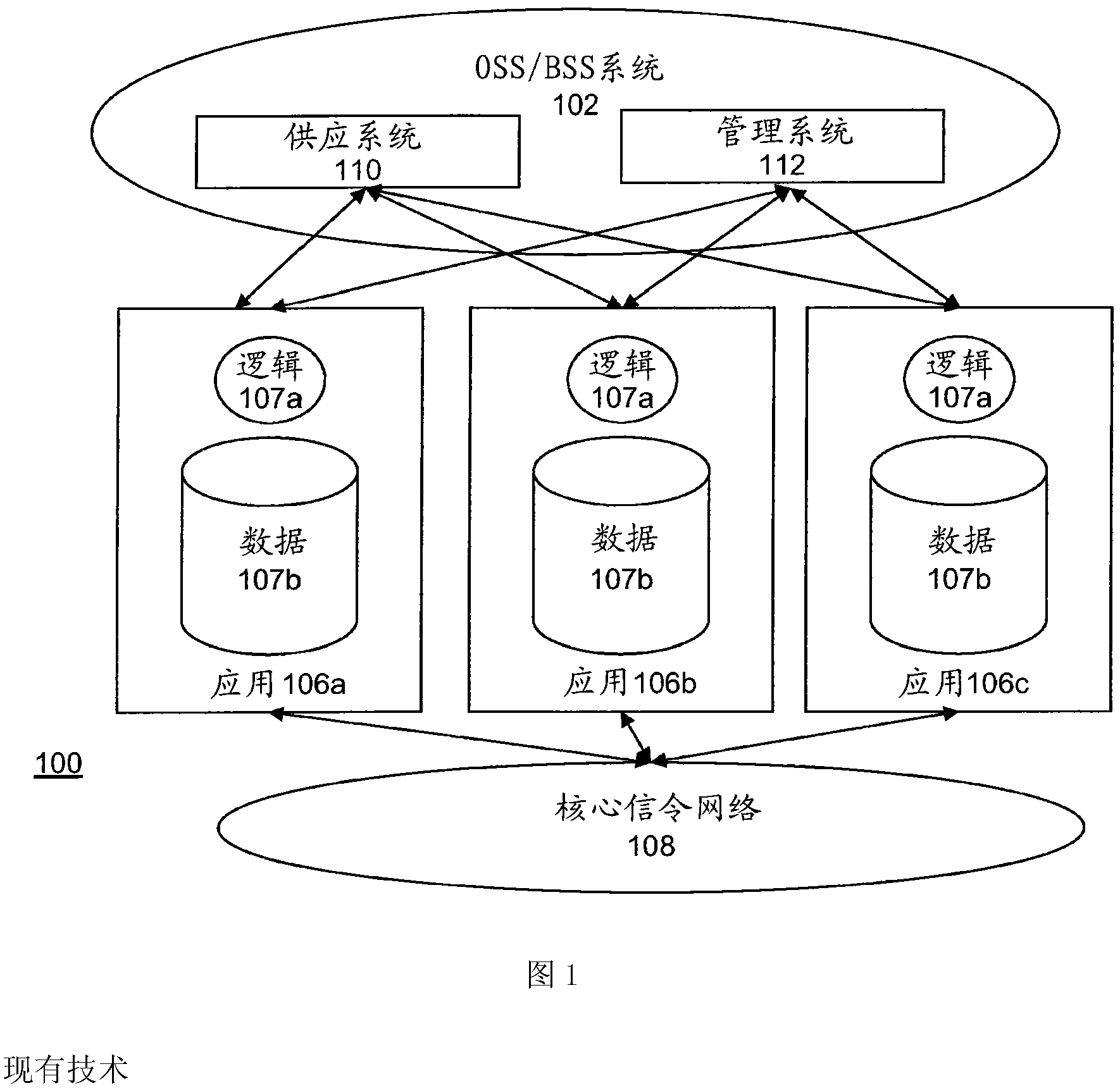
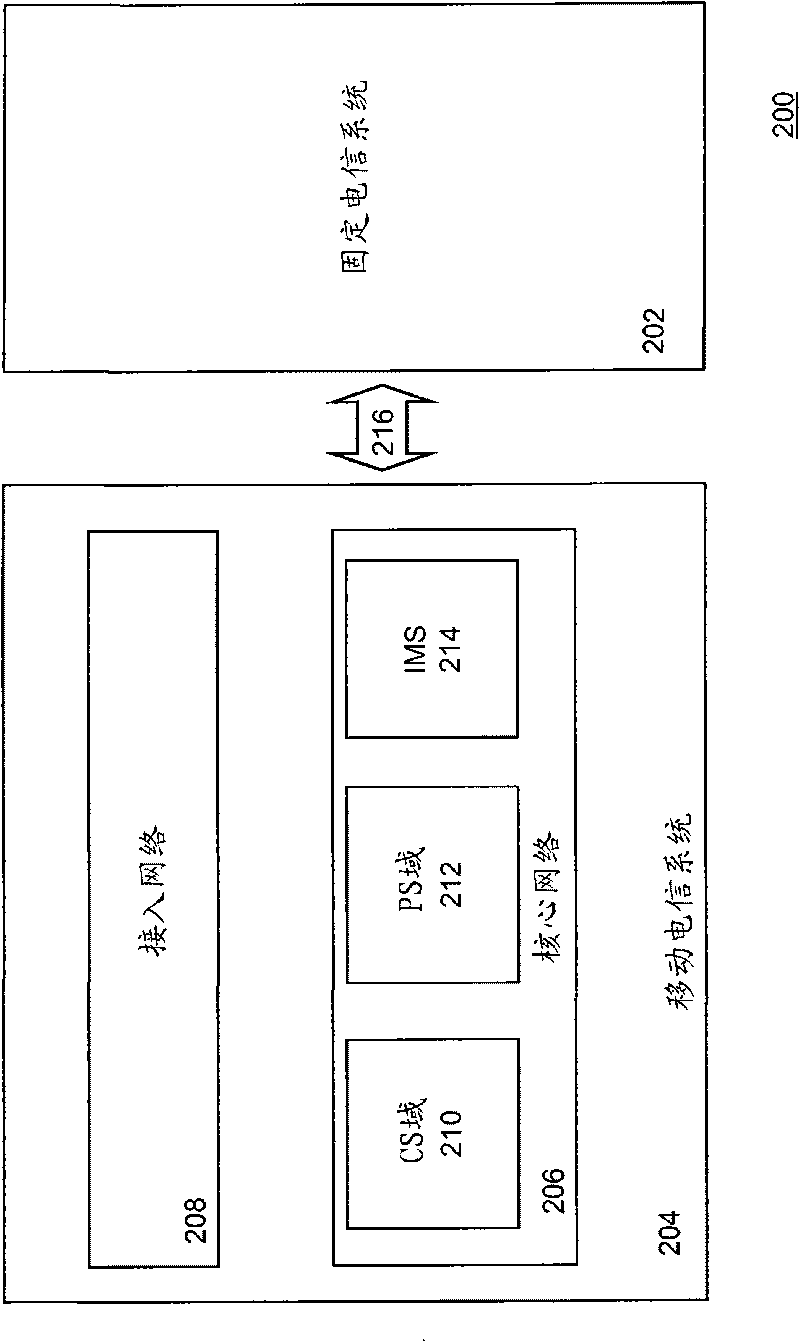
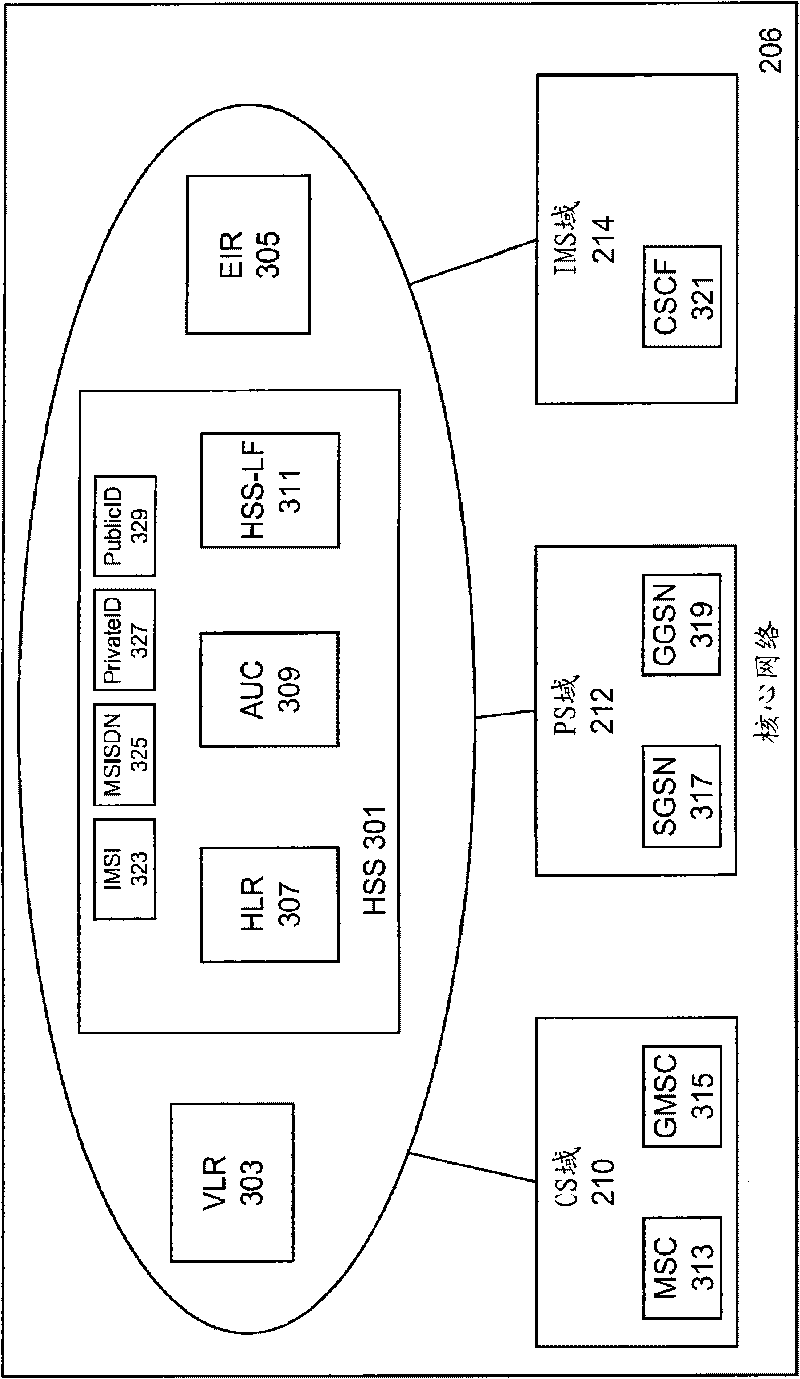
[0046] Traditional mobile telecommunications networks are the result of evolution rather than revolution. As the communications market has evolved, consolidation and acquisition, along with changing business strategies, have resulted in operational and functional data silos within a typical communications service provider (CSP). A typical network arises from a series of functional overlays to a core network built primarily for voice communications. Thus, duplication often exists in user databases, service creation and provisioning processes, administration, support, and billing. Many CSPs want to rationalize and consolidate their businesses to remove this duplication in order to reduce costs, increase efficiency and ultimately improve customer service. At the same time, CSPs often need to add capacity, add functional enhancements, and replace aging infrastructure. In addition, CSPs may also want to prepare for further convergence between voice communicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com