Point of entry authorization utilizing RFID enabled profile and biometric data
a biometric and user-enabled technology, applied in the field of user biometric authentication, can solve the problems of insecure access control system, pre-set codes are often forgotten, and electronic and mechanical system security has rapidly become an important issu
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052]The particular values and configurations discussed in these non-limiting examples can be varied and are cited merely to illustrate at least one embodiment and are not intended to limit the scope thereof.
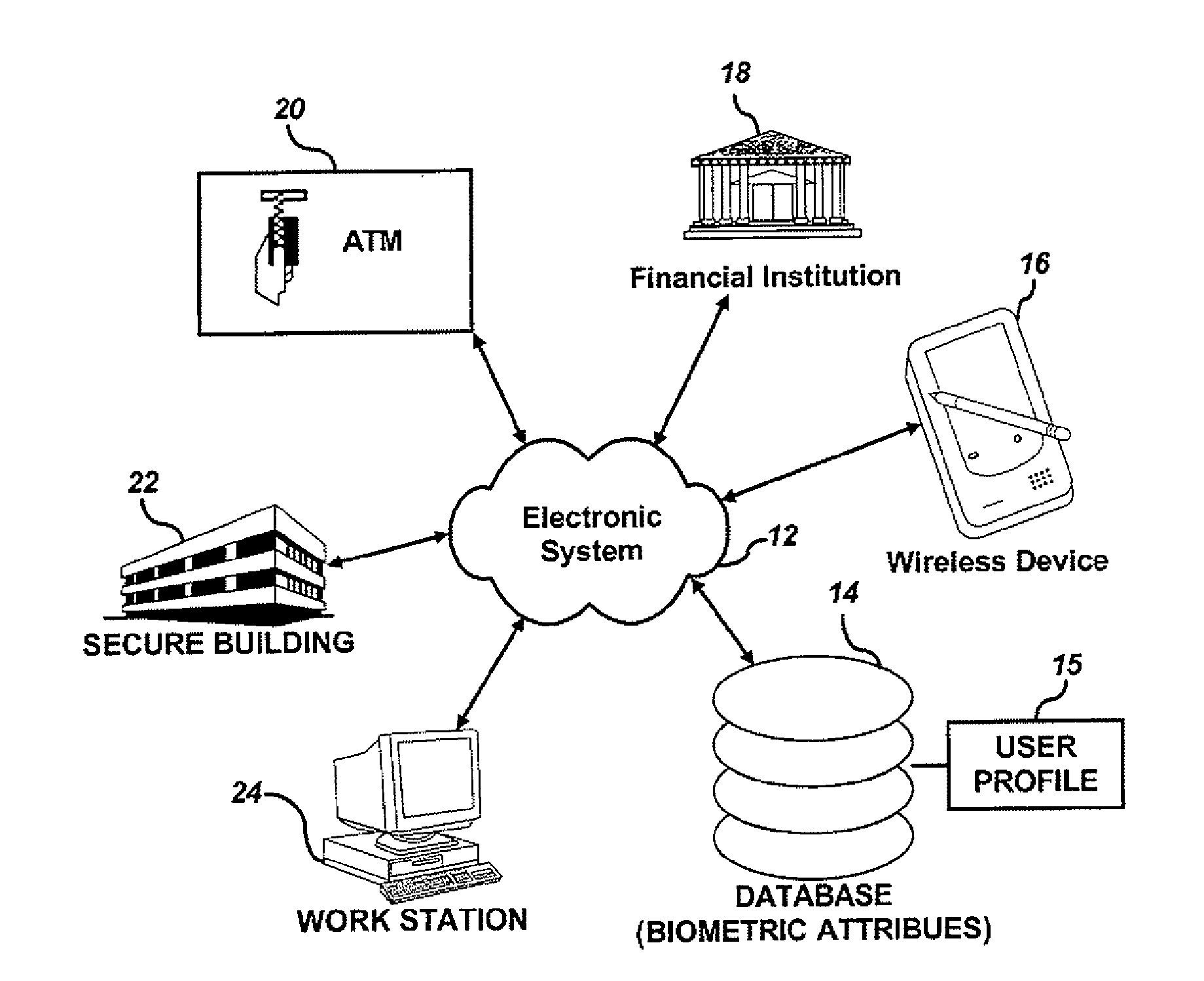
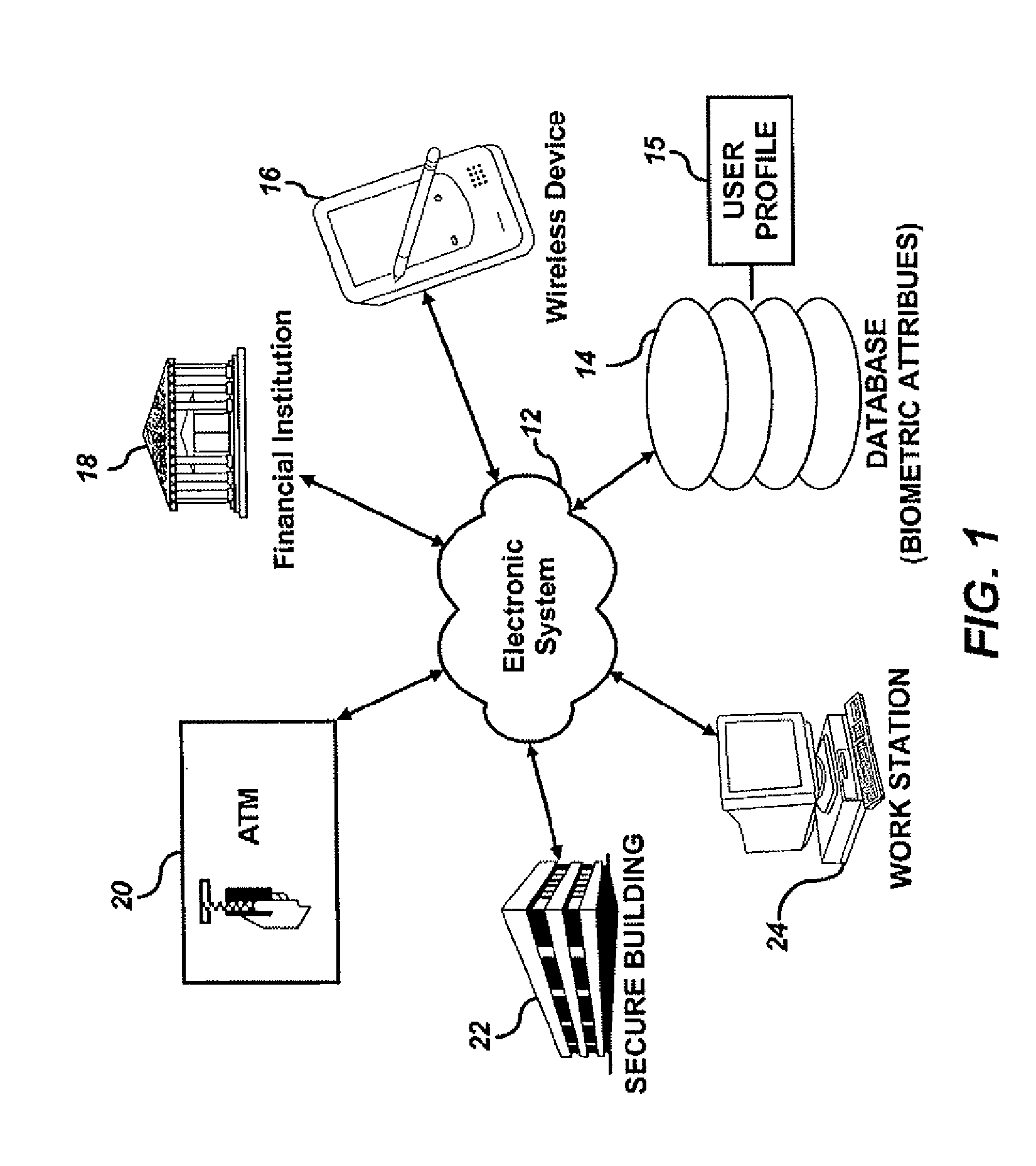
[0053]FIG. 1 depicts a block diagram illustrating components of an electronic system 12 associated with a database or memory containing biometric attributes 14, in which embodiments can be implemented. Database 14 can be linked or integrated with electronic system 12 and can include at least one user profile 15 containing biometric templates (i.e., samples) of biometric attributes provided previously by particular users. Electronic system 12 can interact with and communicate with a variety of devices and mechanical systems.
[0054]Electronic system 12 can, for example, communicate with a computer workstation 24. In such an example, electronic system 12 can be configured as a remote computer network (e.g., the Internet), or a dedicated computer network (e.g., Intranet, WLAN, LAN, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com