Method and Apparatus for Dynamic Generation of Symmetric Encryption Keys and Exchange of Dynamic Symmetric Key Infrastructure
a technology of dynamic symmetric encryption and key infrastructure, applied in electrical equipment, digital transmission, securing communication, etc., can solve problems such as the inability to produce or reproduce keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034]The following description is provided to enable any person skilled in the art to make and use the invention and sets forth the best modes presently contemplated by the inventors of carrying out the invention. Various modifications, however, will remain readily apparent to those skilled in the art, since the generic principles of the present invention have been defined herein.
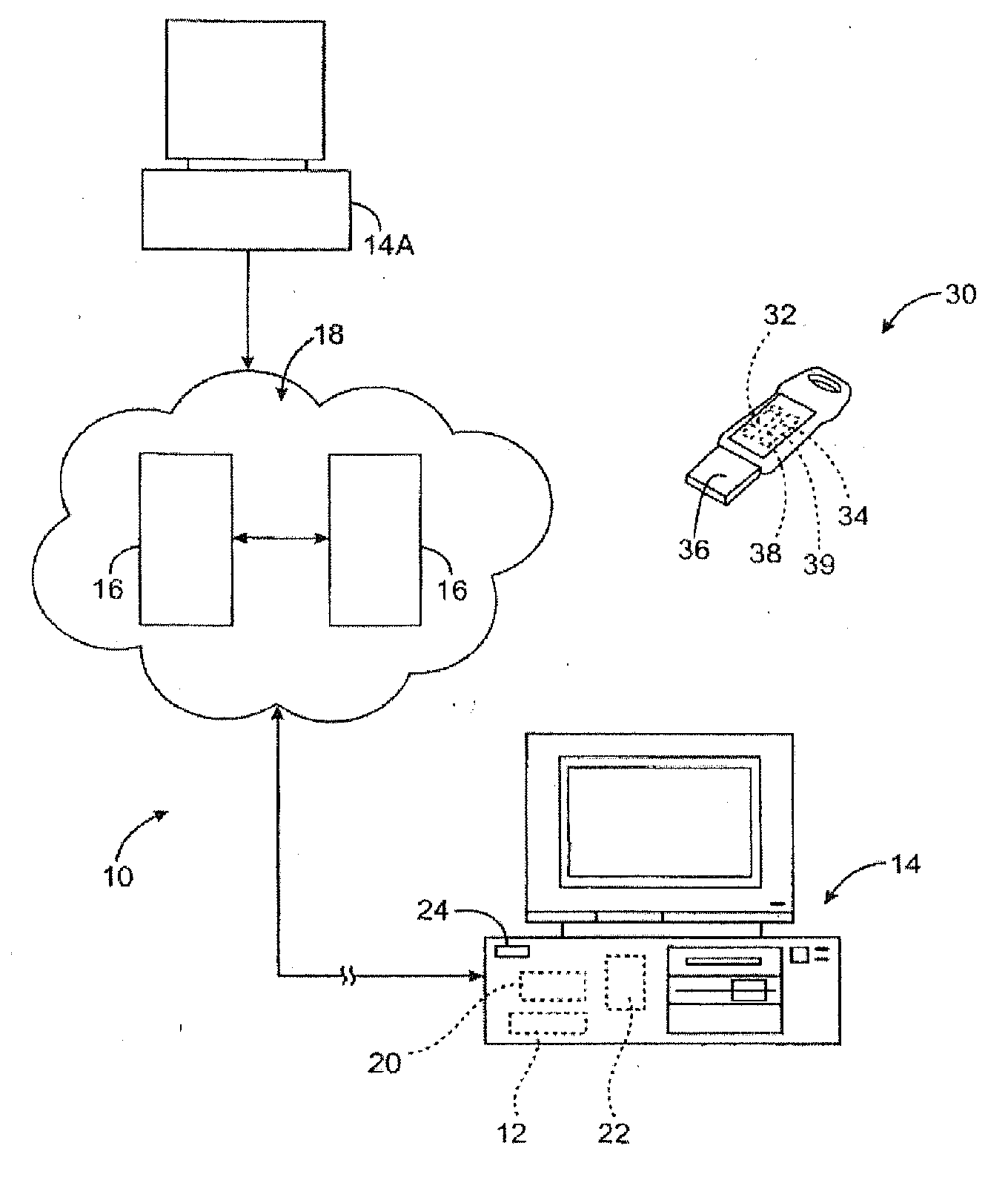
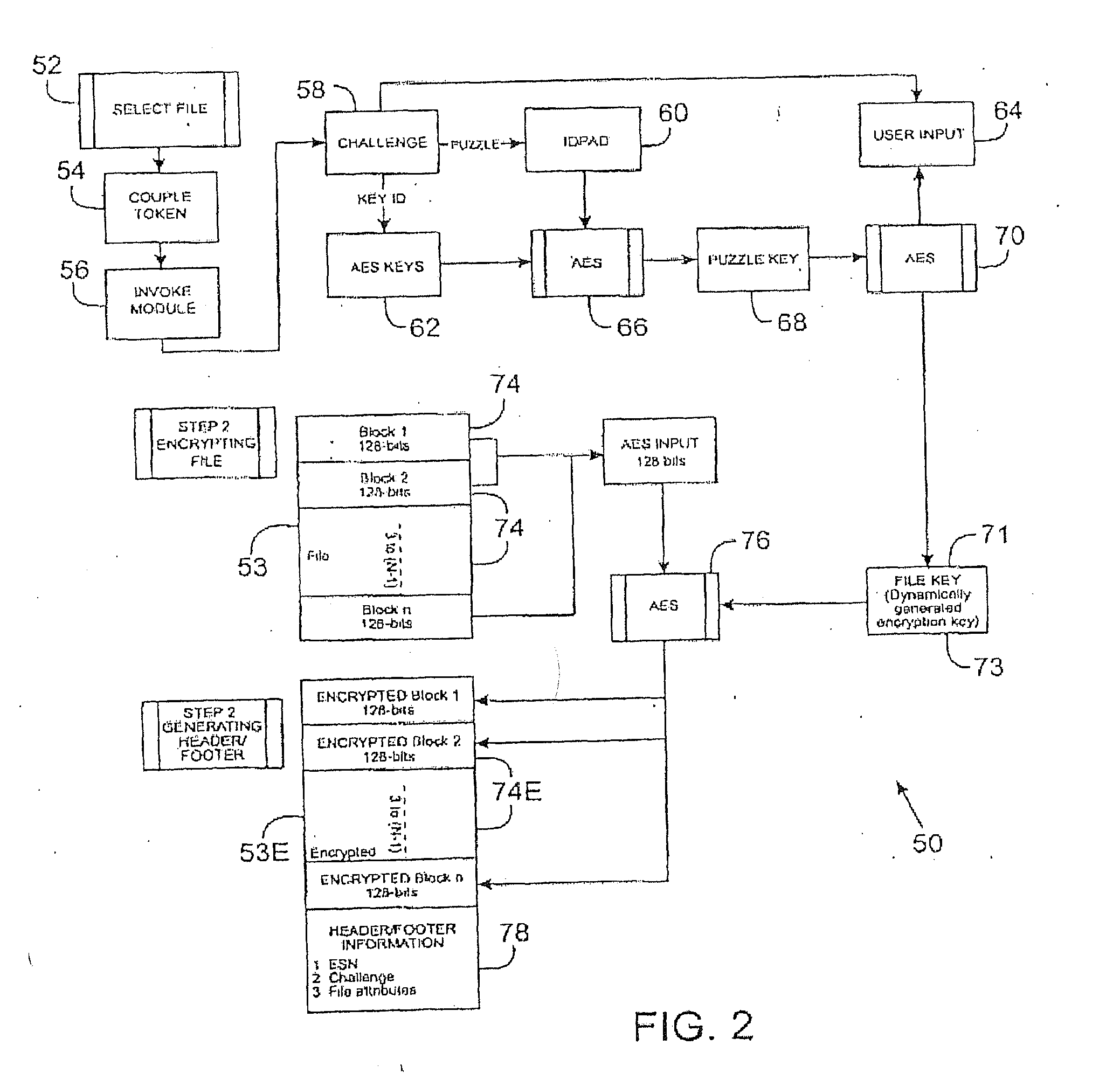
[0035]The present invention provides a method and apparatus for dynamically generating data encryption keys for encrypting data files and for decrypting encrypted data files via a key exchange method. The present invention provides a method and apparatus for dynamically generating an encryption key for each encryption event. The dynamically generated encryption key is not saved after an encryption event, so that the key cannot be produced or reproduced. Resultantly, a file encrypted with the dynamically generated key is prevented from unauthorized decryption. Thus, the present invention is not substantiall...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com