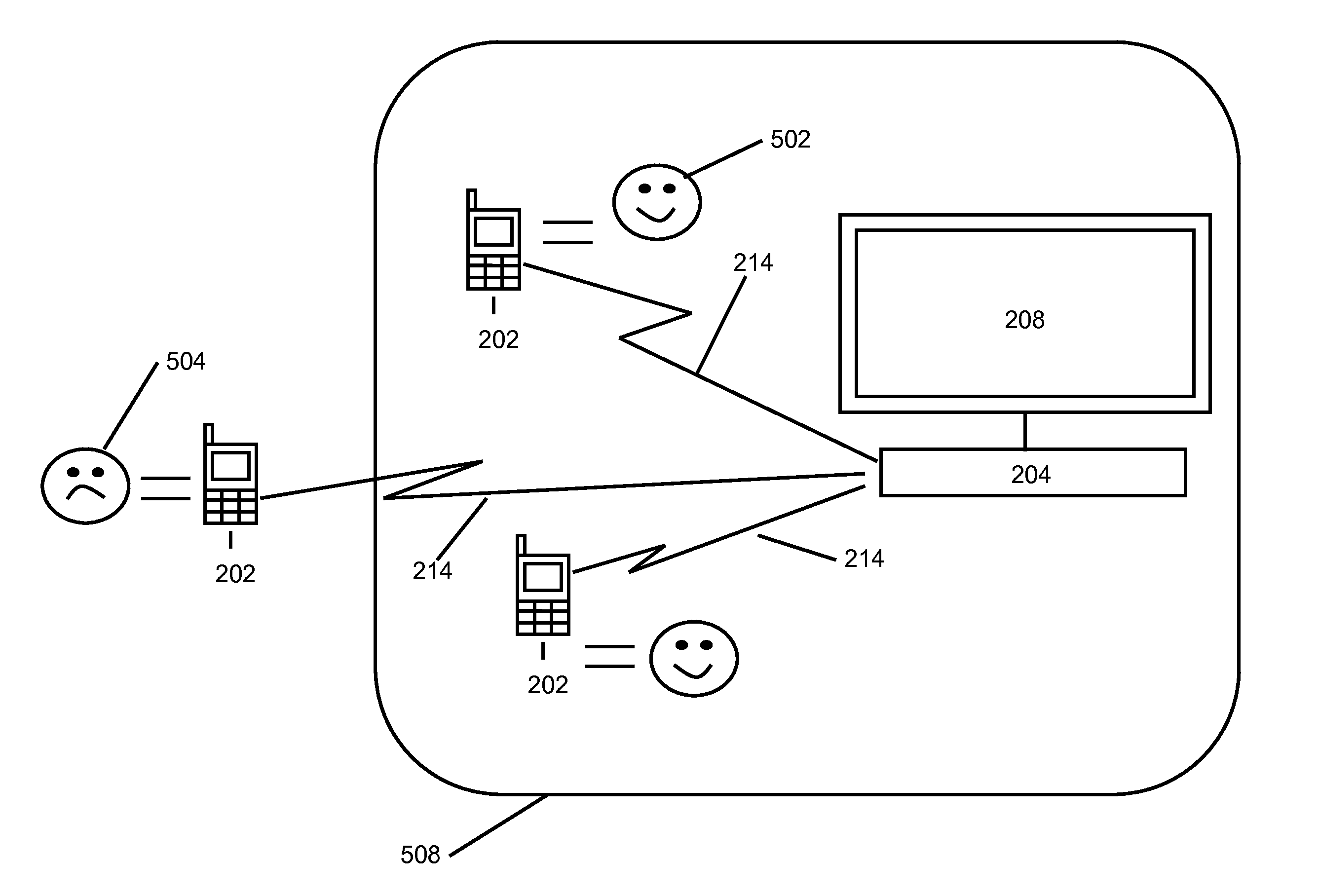
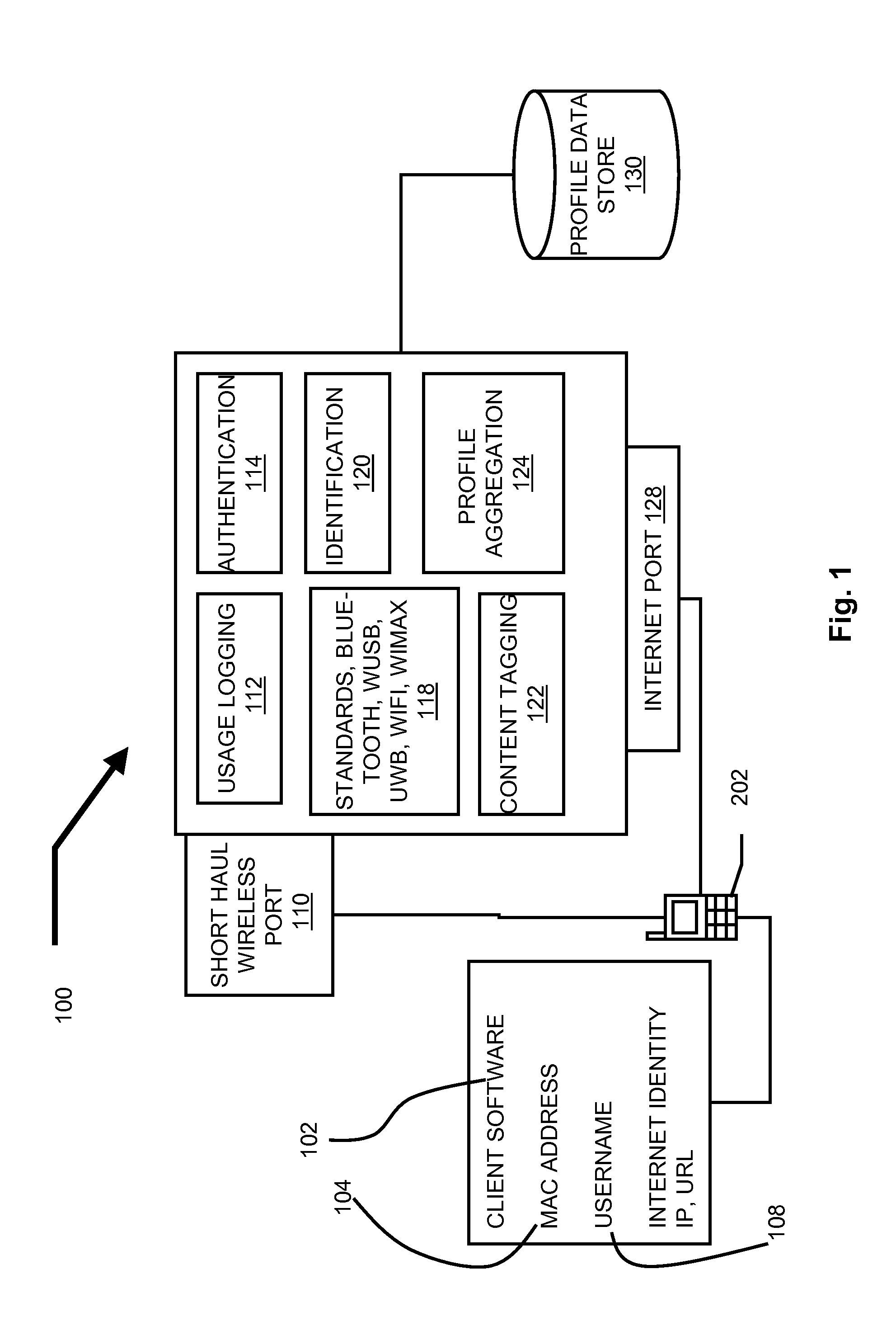
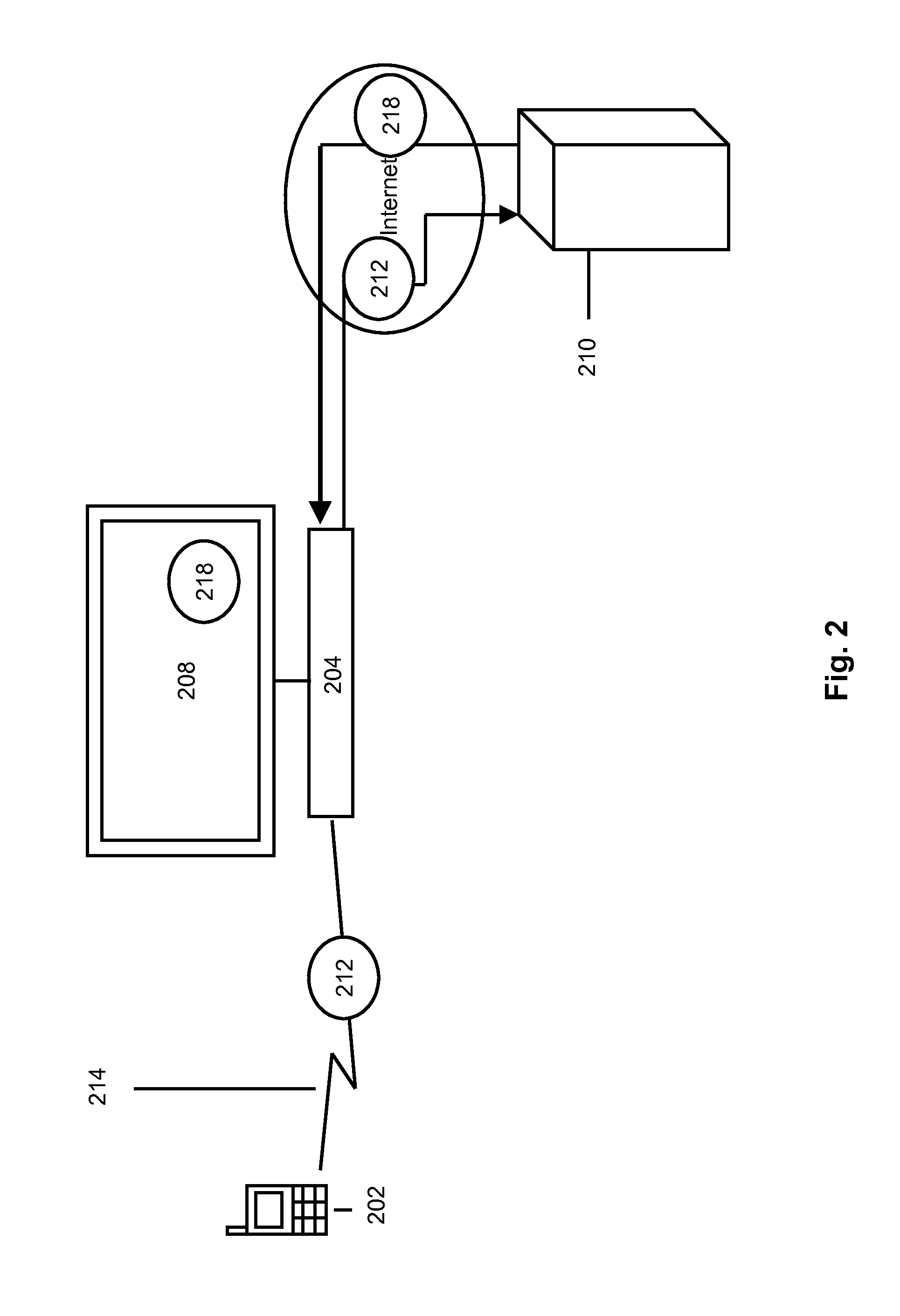
Real world behavior measurement using identifiers specific to mobile devices
a mobile device and real-world behavior technology, applied in the field of wireless communication, can solve problems such as misleading content-targeting methods that face various challenges, and limitations, and achieve the effects of reducing the number of profiles based on that usage, limited targeting, and misleading profiles
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0086]The following disclosure relates generally to mobile device identification and authentication for access to and presentation of targeted content.
[0087]As used herein, the terms “comprises,”“comprising,”“includes,”“including,”“has,”“having” or any other variation thereof, are intended to cover a non-exclusive inclusion. For example, a process, method, article, or apparatus that comprises a list of elements is not necessarily limited to only those elements but may include other elements not expressly listed or inherent to such process, method, article, or apparatus. Further, unless expressly stated to the contrary, “or” is intended to mean “and / or” unless otherwise stated to the contrary. Also, use of the “a” or “an” are employed to describe elements and components of the invention. Thus in the foregoing description references to the singular (“a”, “an”, “the”, “one”, etc.) are also intended to refer to the plural unless otherwise stated or clear from the context.
[0088]The Figur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com