Credential validation using multiple computing devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
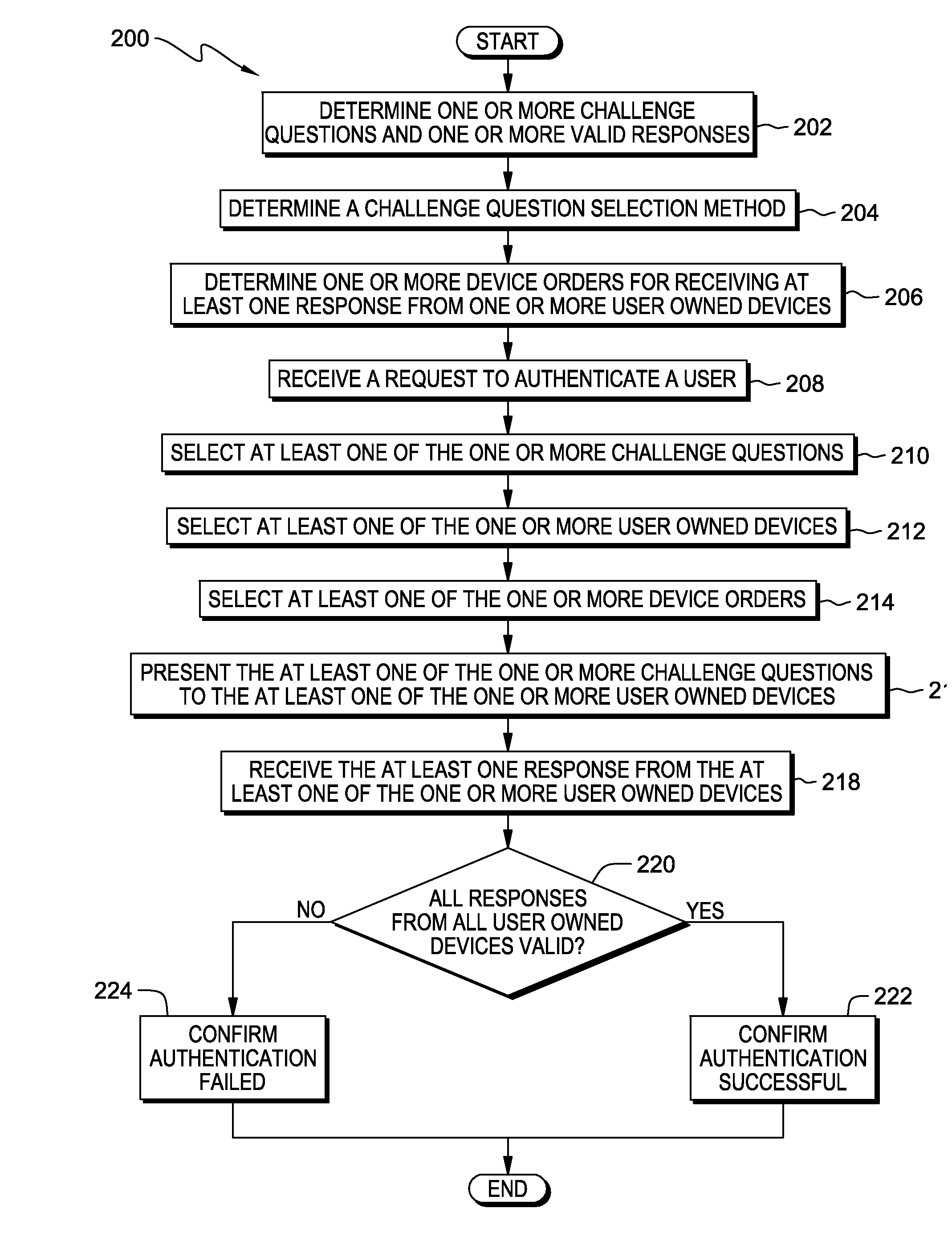
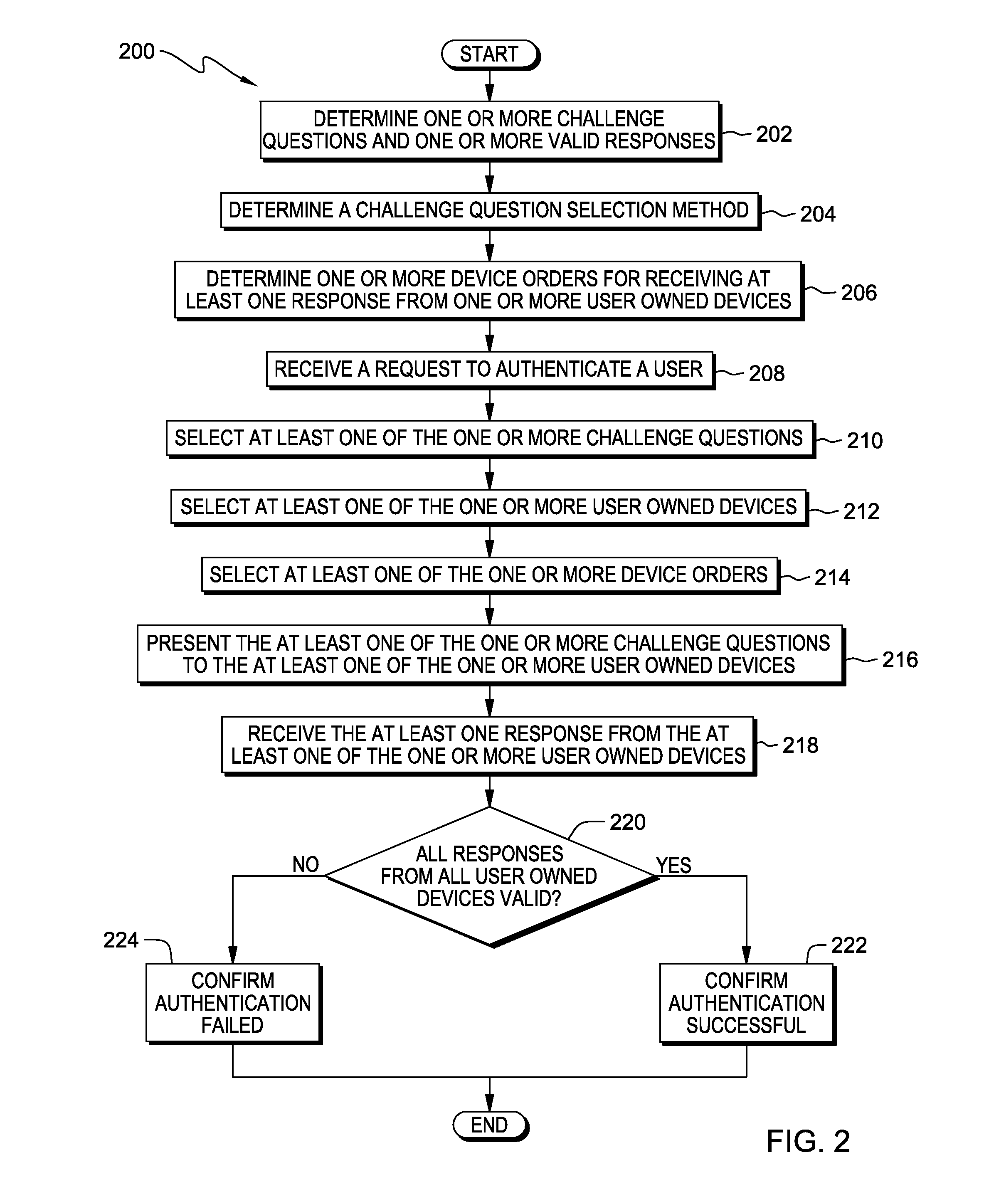
[0007]Embodiments of the present invention recognize that hackers are using publically available information to reset user passwords to gain access to accounts. Embodiments of the present invention further recognize that exposing a challenge question to the public provides a hacker with an opportunity to spoof a system by finding personal or publically available information to overcome the challenge question.
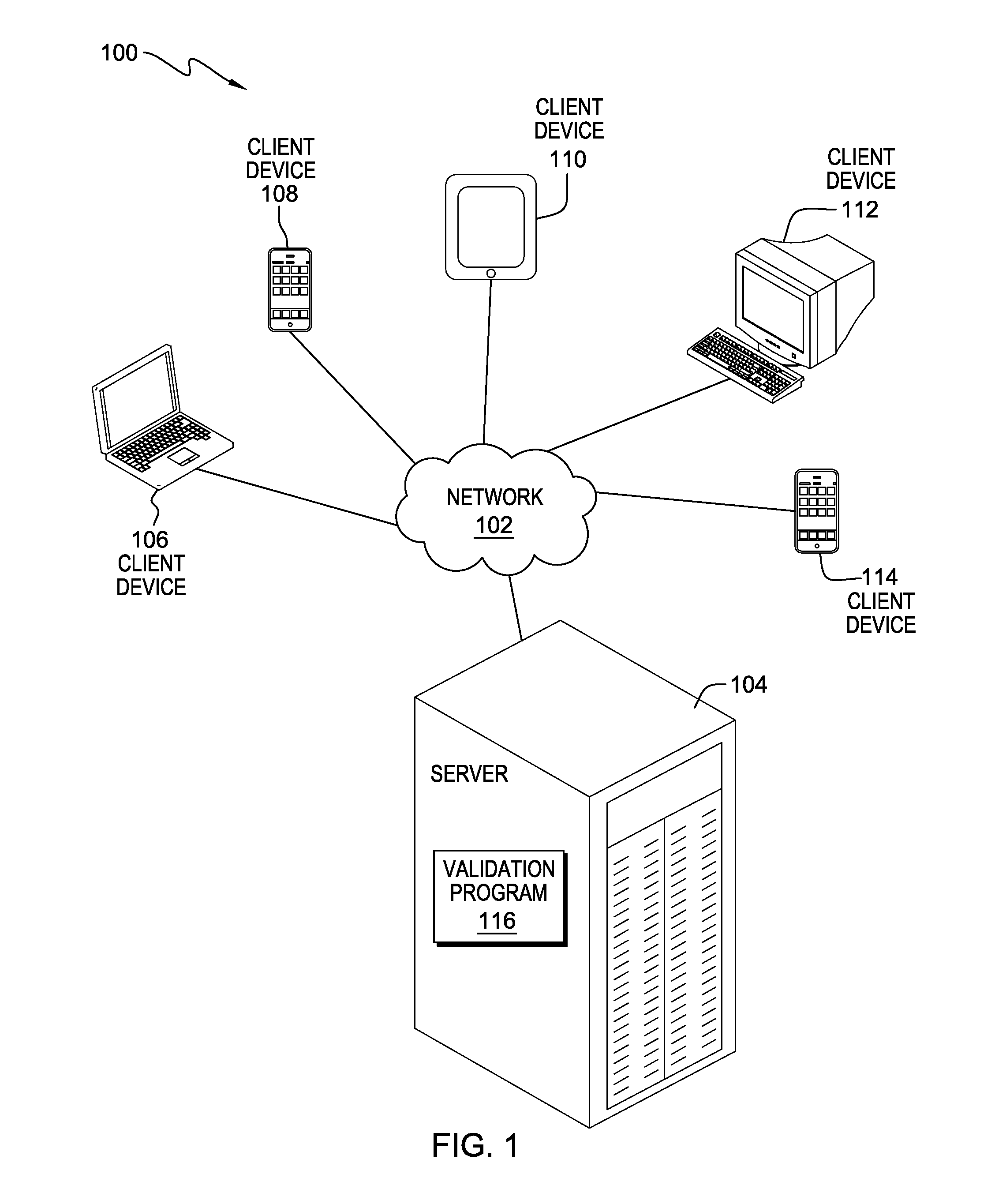
[0008]Embodiments of the present invention provide the capability to utilize multiple user owned devices, linking them in an ordered method, to bolster security through additional scrutiny in credential validation. Embodiments of the present invention further provide the capability to present challenge questions to specific user owned devices, and receive responses from the specific user owned devices in a predetermined order. Embodiments of the present invention further provide the capability to authenticate a user's credentials based, at least in part, on the response, the dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com