Restriction control apparatus, restriction control system, and restriction control method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first example
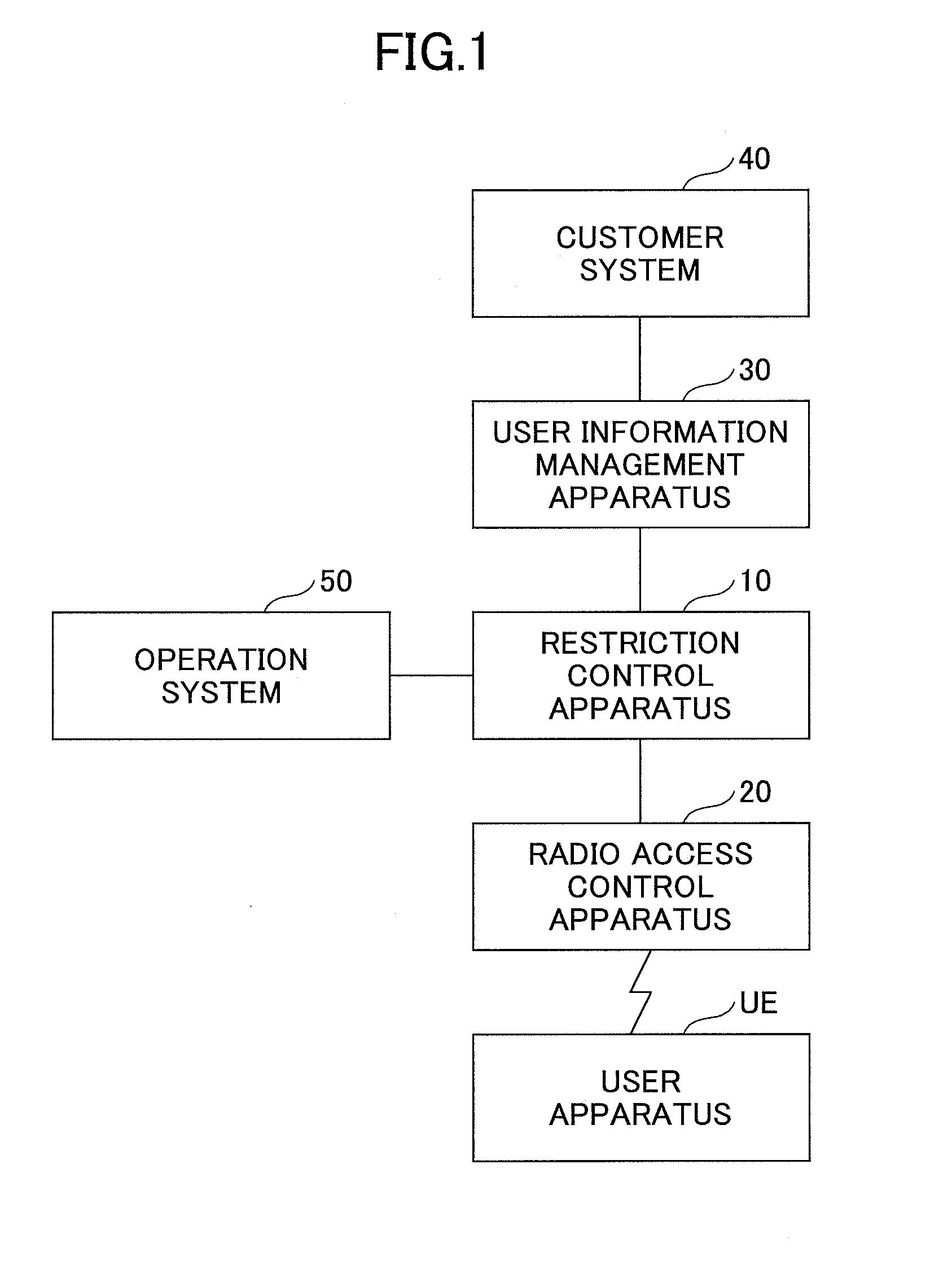
[0038]In one or more embodiments of the first example, the restriction control apparatus 10 holds correspondence information (to be referred to as user information, hereinafter) between a user ID and an M2M group ID, and determines whether to reject or permit a communication request from a user apparatus UE based on the user information so as to realize restriction control for each group.
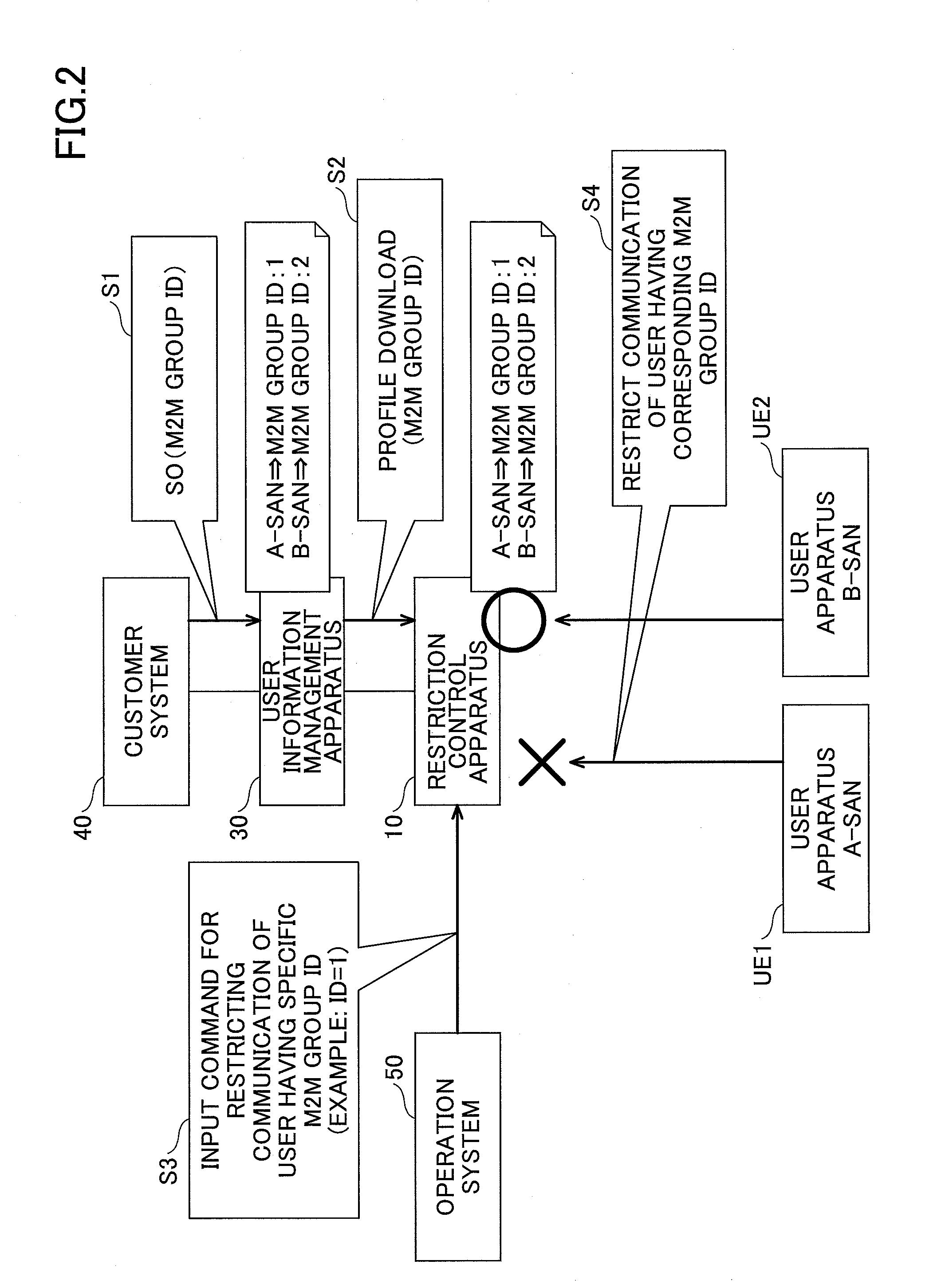
[0039]Outline of processing in one or more embodiments of the first example is described with reference to FIG. 2. First, an M2M group ID is set for each user ID from the customer system 40 to the user information management apparatus 30 (step 1). In the example of FIG. 2, it is shown that M2M group ID1 is set to a user A (A-san), and M2M group ID2 is set to a user B (B-san).
[0040]The user information (profile) including the M2M group ID is downloaded to the restriction control apparatus 10 that accommodates the user apparatus UE of the corresponding user, and the restriction control apparatus 10 ho...
second example
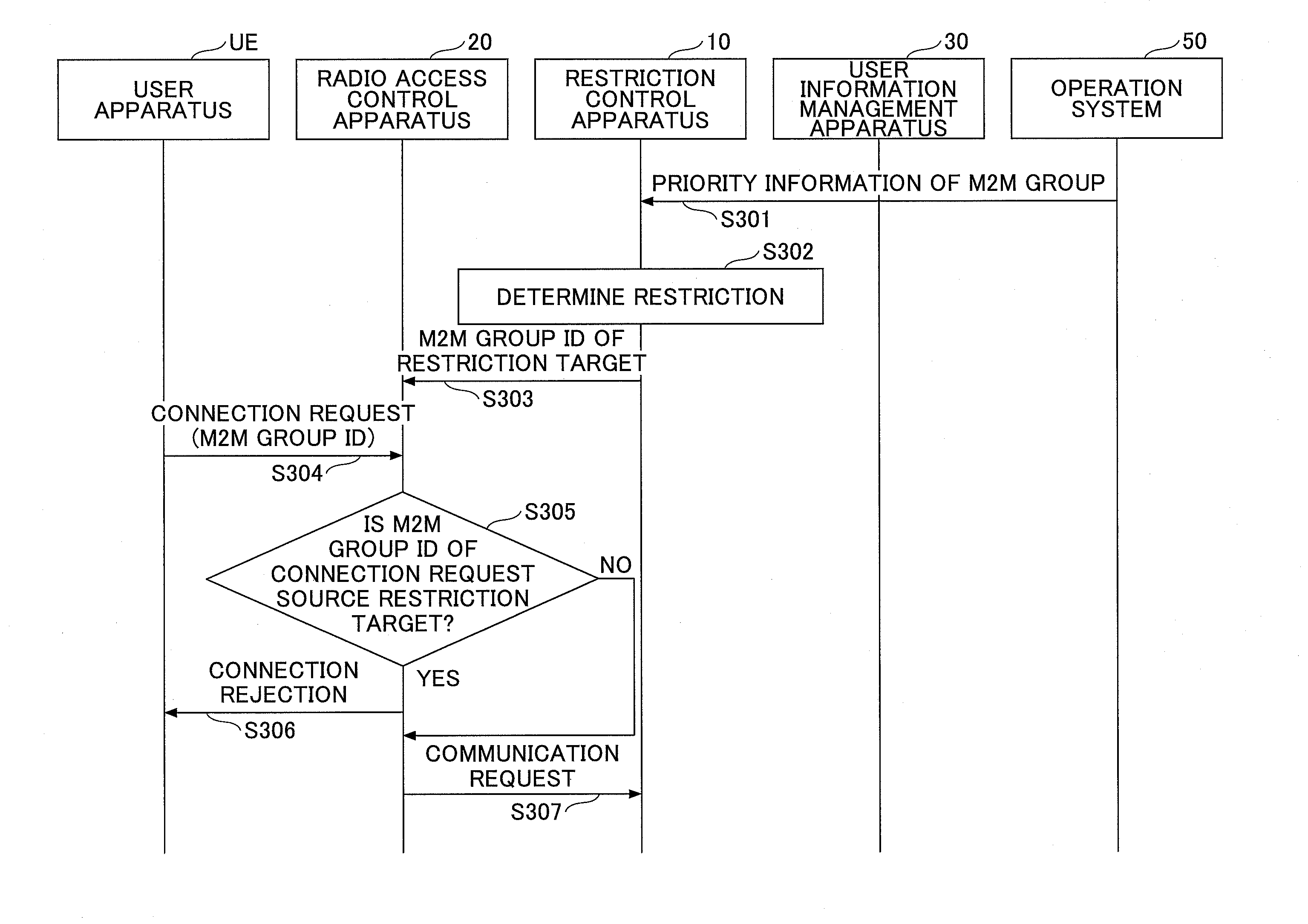
[0074]Next, one or more embodiments of the second example is described. In one or more embodiments of the second example, each user is assigned an M2M group ID, the user apparatus UE holds the M2M group ID, the user apparatus UE transmits a connection request including the M2M group ID to the radio access control apparatus 20 when establishing a radio connection with the radio access control apparatus 20, so that the radio access control apparatus 20 performs restriction determination based on the M2M group ID. In one or more embodiments, although it is not necessary that the user information management apparatus 30 has M2M group IDs for the purpose of restriction control, the M2M group IDs may be held. However, the customer system 40 or the operation system 50 holds information in which a user ID (arbitrary ID for identifying user or user apparatus UE) is associated with an M2M group ID for the purpose of determining which user apparatus UE to select as a restriction target.
[0075]T...
first example and second example
COMBINATION OF FIRST EXAMPLE AND SECOND EXAMPLE
[0094]Although the first example and the second example have been described separately so far, the communication system shown in FIG. 1 may have functions of both of the function of the first example and the function of the second example.
[0095]In this case, for a user apparatus UE that does not have an M2M group ID, restriction control can be performed by the method described in the first example. Also, for a user apparatus UE that has an M2M group ID, restriction control may be performed by the method described in the second example, or may be performed by the method described in the first example.
[0096]In the combination of the first example and the second example, for example, there is provided a restriction control system including the restriction control apparatus 10 in the first example and the radio access control apparatus 20 in the second example.
[0097]The user apparatus UE described in one or more embodiments may include a CP...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap