Self-independent access control method for database list row data
A technology of autonomous access control and access control, which is applied in the fields of electronic digital data processing, special data processing applications, instruments, etc. Row-level data, the effect of improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
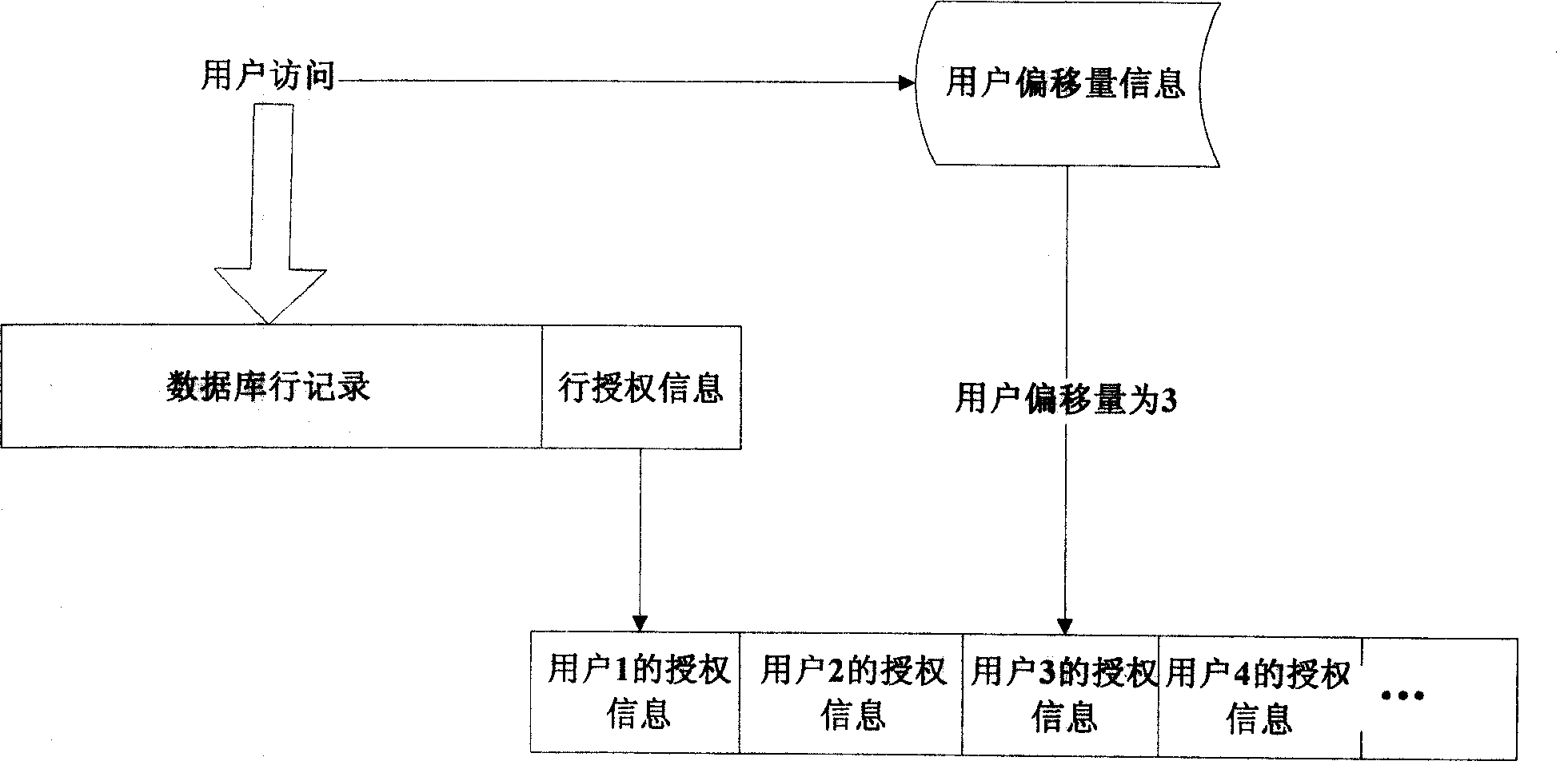
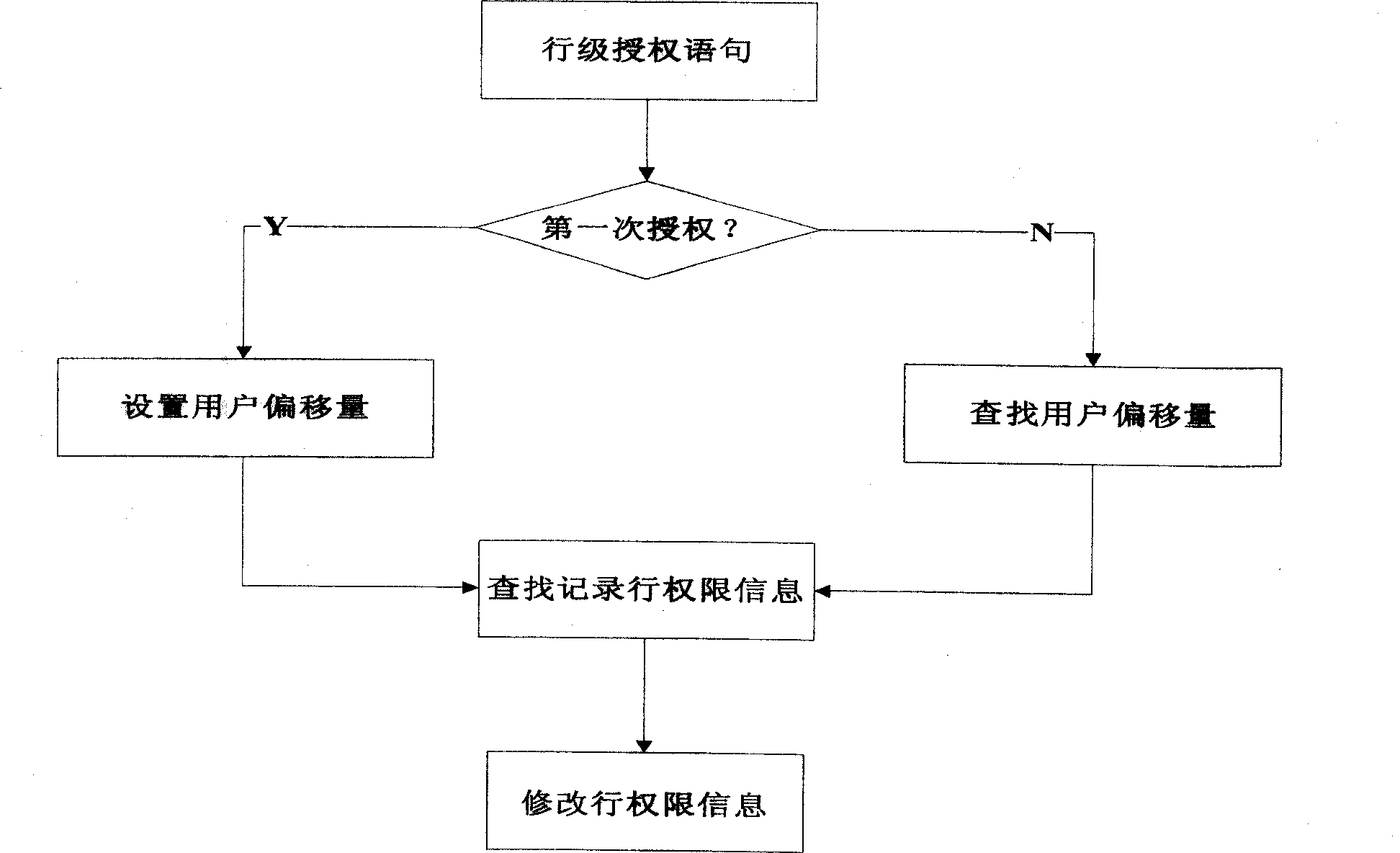
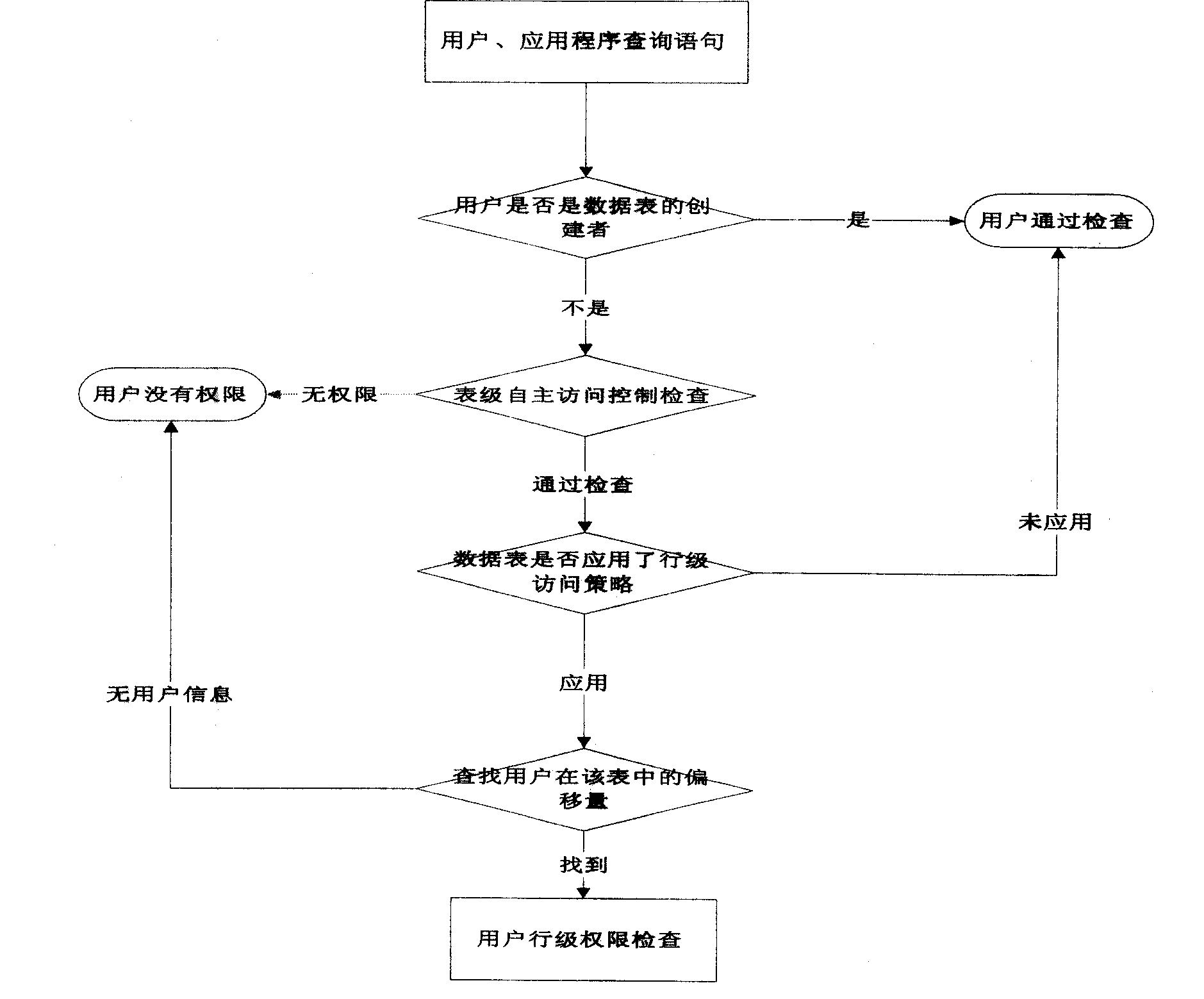
[0022] The invention modifies the database table, and adds a column in the database table to which the row-level autonomous access control policy is applied, which is used to record the row-level authorization situation of each record row, so as to realize the row-level autonomous access control. At the same time, the offset of the database user in the database table is recorded in the row-level autonomous access control system table, and the permission information of the row recorded by the user is found through this offset.
[0023] The structure diagram of the row-level autonomous access control model is as follows: figure 1 shown.
[0024] A database that uses row-level autonomous access contains the following data objects:
[0025] ●One system table: the row-level autonomous access control system table (sys_user_row_privilege), which is mainly used to record the information of the database table using the row-level access control policy, including: the name of the databa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com