Identification based integrated network terminal united access control method
A network terminal and access control technology, applied in data exchange networks, transmission systems, digital transmission systems, etc., can solve the problems of tracking and positioning operation problems, debugging and troubleshooting difficulties, etc., to overcome cloning threats and authentication processes. Simple, easy to achieve effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
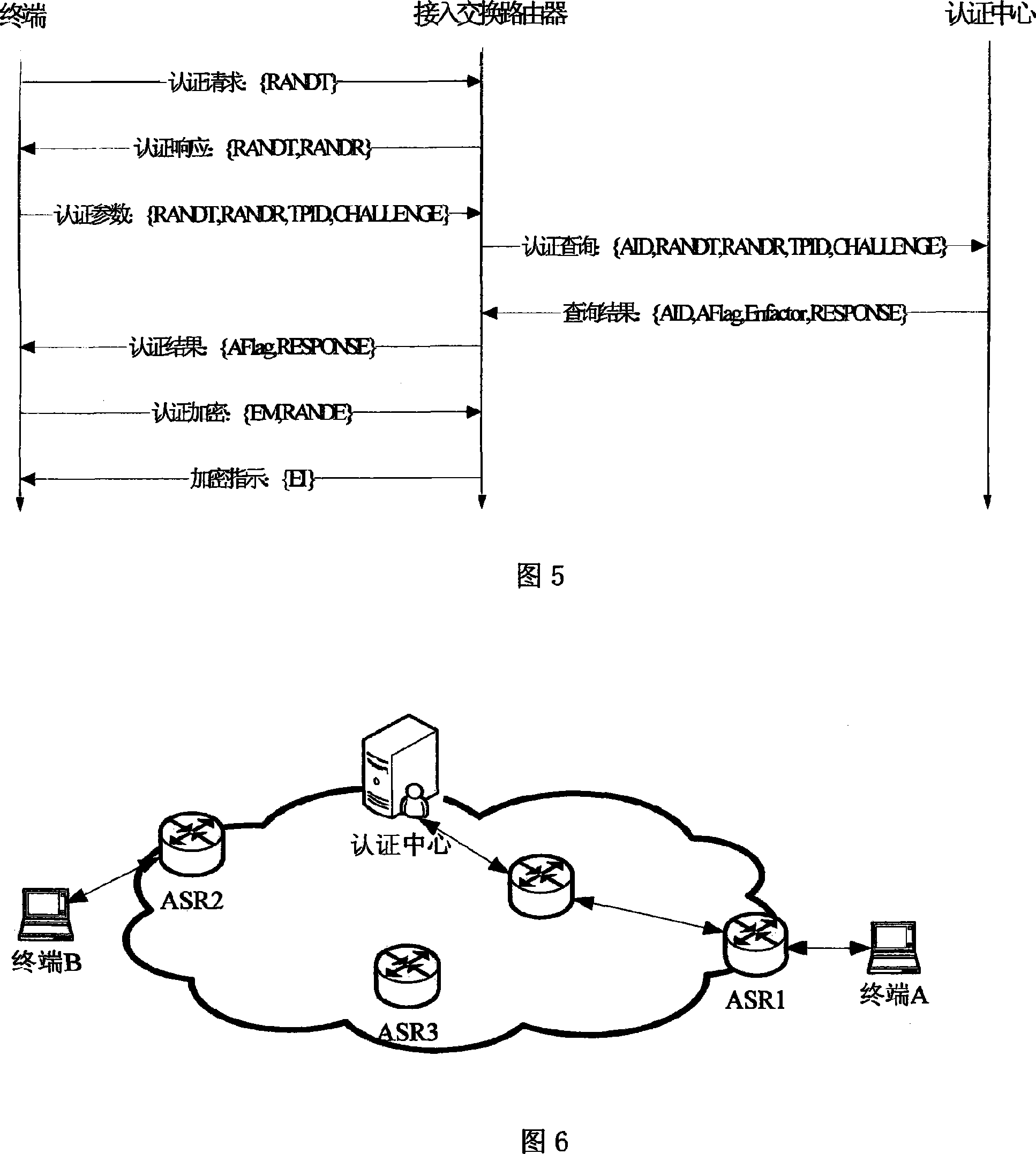
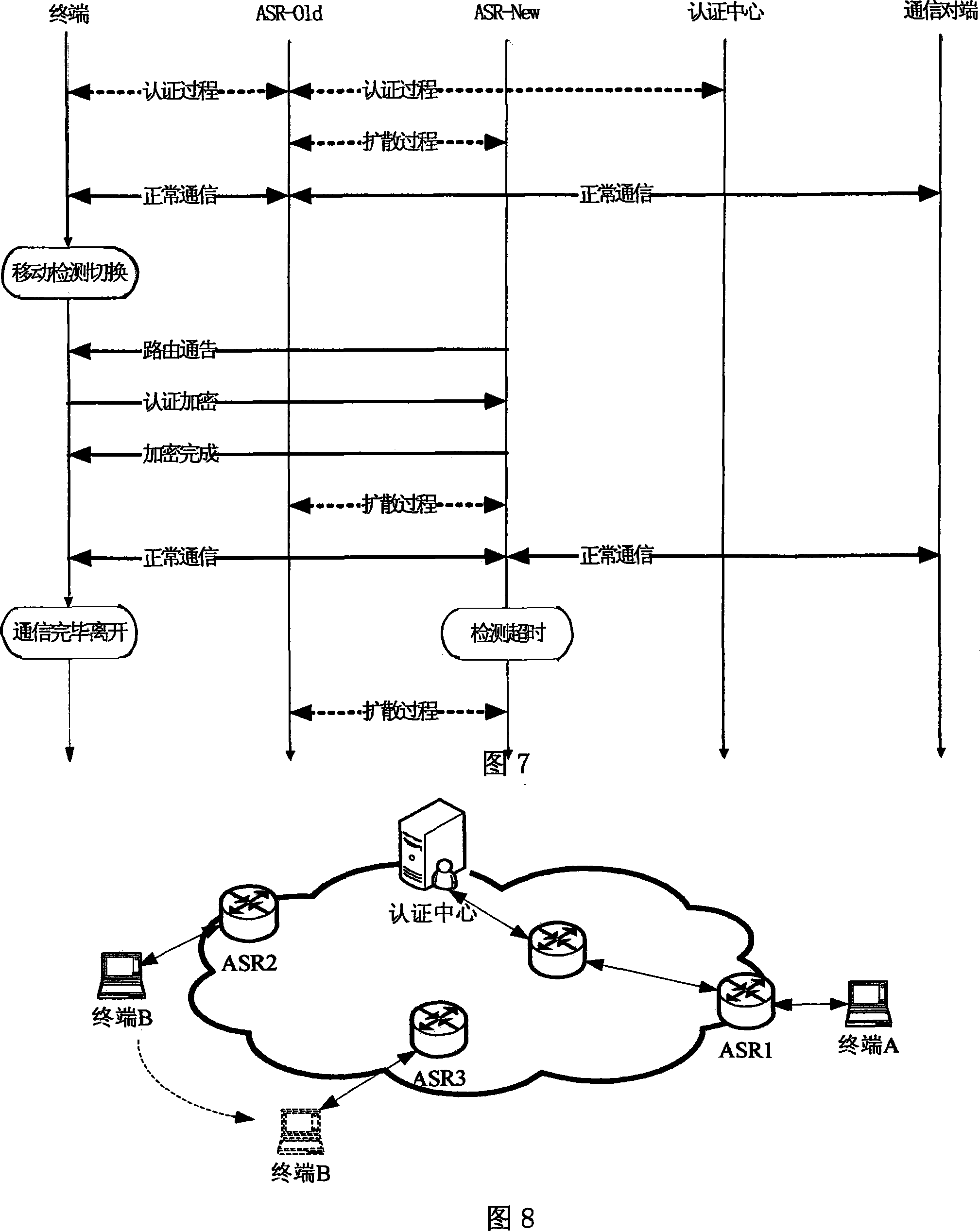
[0028] The complete technical solution proposed in this embodiment consists of five parts: the definition of the unified identity of the terminal, the registration process of the unified identity of the terminal, the unified access control authentication process of the terminal, the fast authentication process of the mobile handover of the terminal, and the encrypted communication process between the terminal and the ASR. .
[0029] The hardware involved in this embodiment includes: three network entities: terminal, access switching router, and authentication center.
[0030] The terminal generally refers to various electronic devices that can be connected to the network, such as computers, telephones, mobile phones, sensor nodes, and the like.
[0031] The access switching router is responsible for the access of various fixed terminals and mobile terminals, fixed networks such as WLAN, and mobile networks such as mobile subnets and ad hoc networks, and is responsible for acce...
Embodiment 2
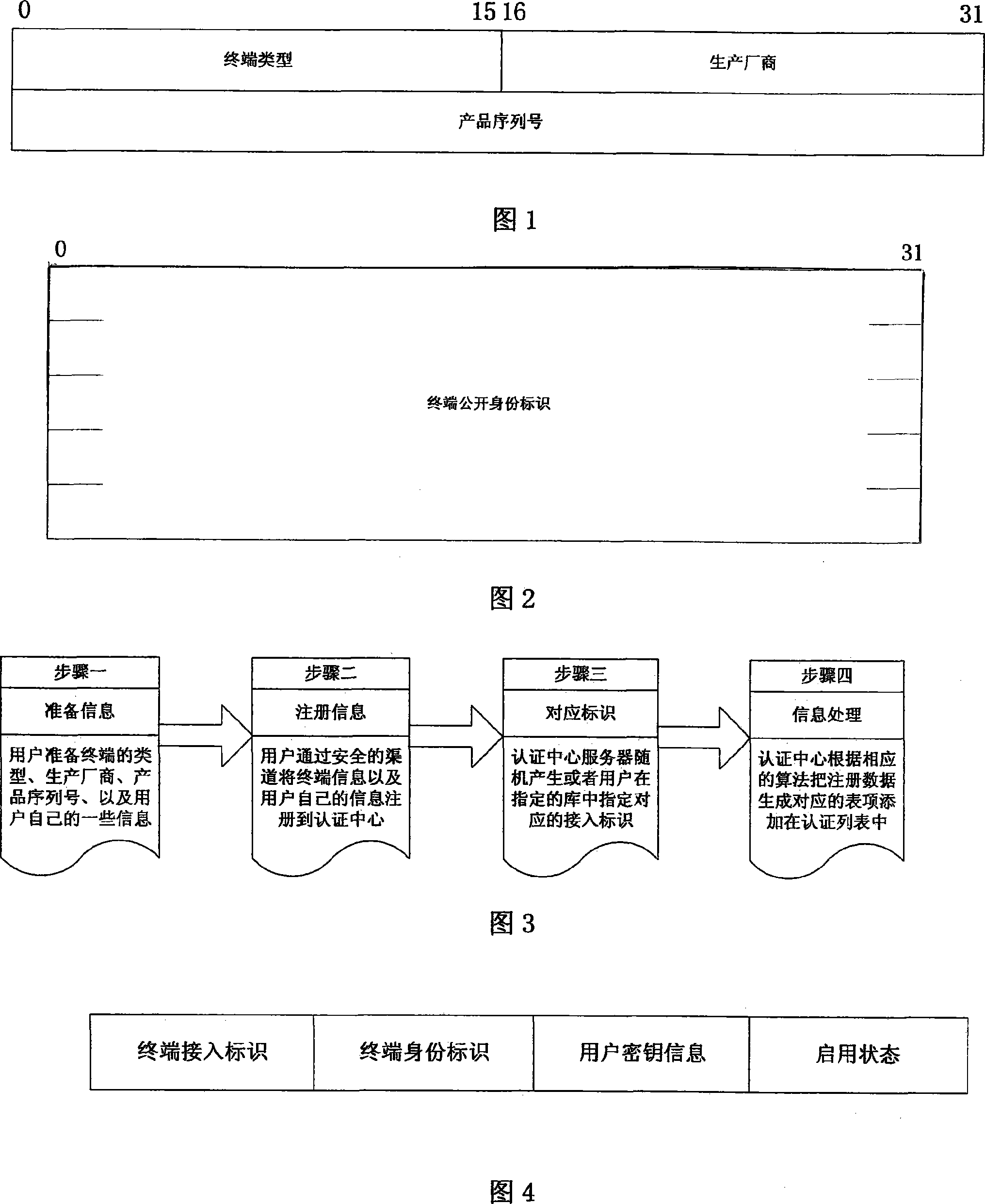
[0042] This embodiment is a refinement of the steps of defining the unified identity of the terminal described in the first embodiment. The definition of terminal unified identity is based on the commonality of heterogeneous network terminals, abstracting the category, manufacturer and terminal serial number of heterogeneous network terminals to form a user-readable terminal privacy identity, and the unreadable identity after encryption transformation is used as The public identity of the terminal is used for authentication transmission between network nodes.
[0043] The above narrative can be described as the following steps:
[0044] Find the commonality of heterogeneous network terminals, and abstract the category, manufacturer, and terminal serial number of heterogeneous network terminals to form a user-readable terminal privacy identity.
[0045] The user-readable terminal privacy identity is encrypted and transformed into an unreadable identity, which is used as the te...
Embodiment 3
[0047] This embodiment is a refinement of the steps of the registration process of the terminal unified identity described in the first embodiment. Before connecting to the network, the terminal must register its type, manufacturer and product serial number in the certification center, and obtain the legal access identifier for accessing the network, otherwise the terminal will never be able to pass the network-to-terminal unified access control certification process without being able to enjoy network services.
[0048] The registration process of the unified identity information of the terminal refers to the process that the user registers with the authentication center server in the network after purchasing the terminal, and the process is shown in FIG. 3 . The authentication center server saves the identity information entry for each terminal, as shown in Figure 4, for authentication query when the terminal accesses the network. The specific registration process is as fol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com