A method for realizing network access control
A network access control and network access technology, applied in the field of network access control, can solve the problems of unsuitable hotel environment, difficult for network operators to know when network end users start to surf the Internet, weak monitoring of network end users, etc. The process is convenient and fast, clear network access control, and the effect of network access control is realized
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
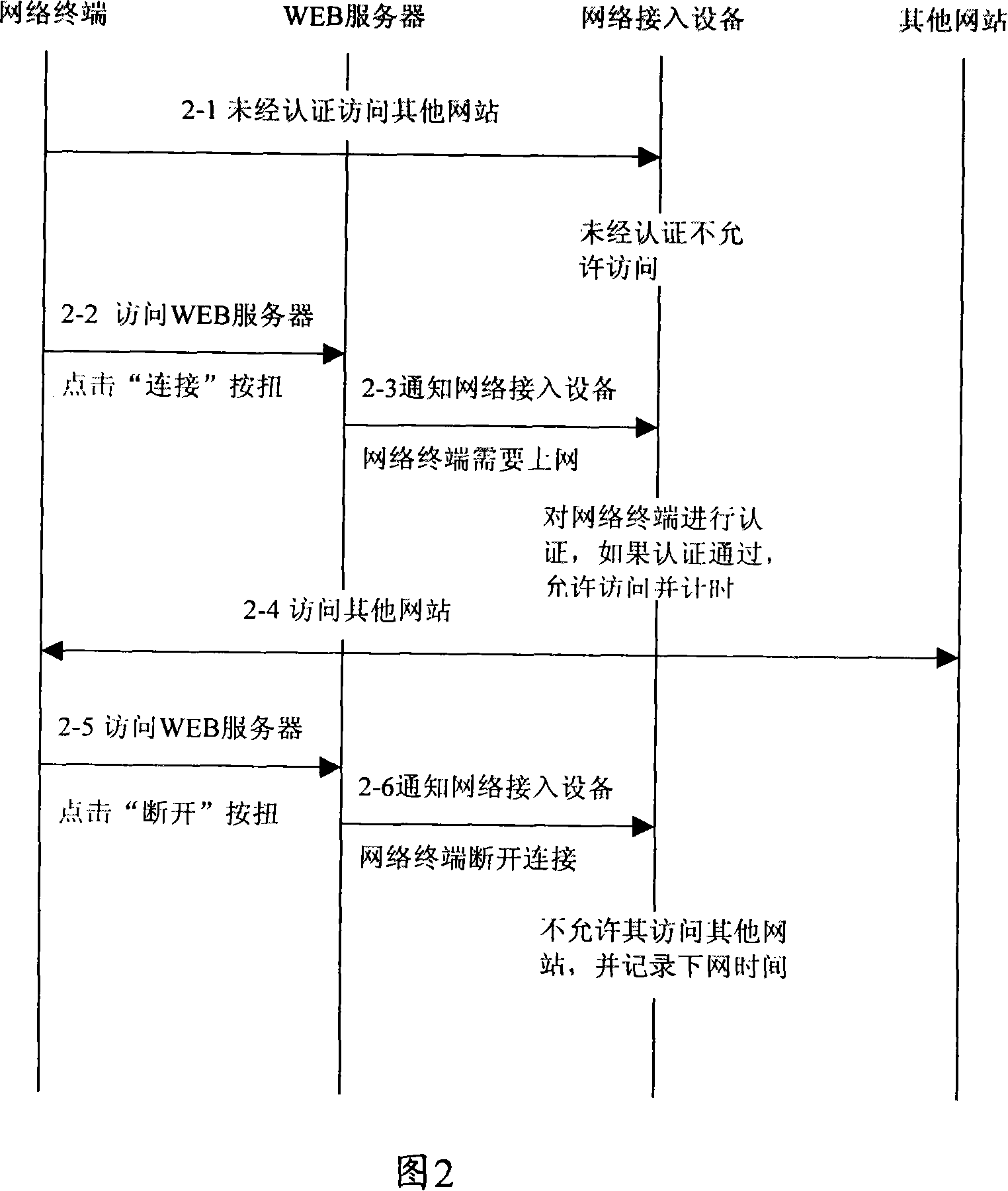
[0042] The core idea of the present invention is: we can simplify the authentication process and adopt an Information such as user name information and passwords of network terminal users can also realize a convenient and fast authentication method for authentication to manage the Internet access rights and information of network terminal users, so as to realize network access control for network terminal users.
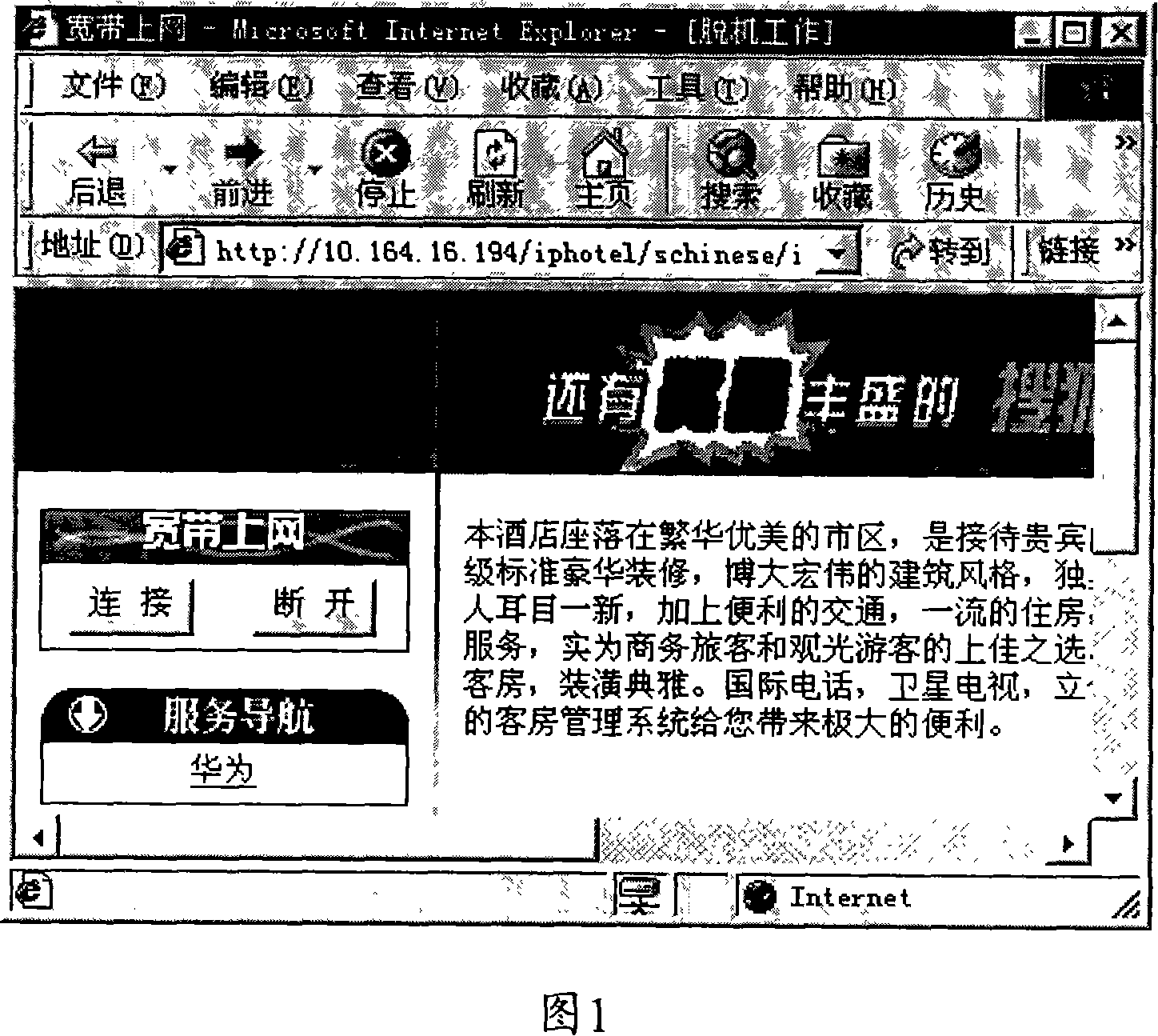
[0043] The specific implementation method of the present invention is: the network terminal user transmits the request message to the network access device, the network access device can be a switch, etc., and the request message can be an HTTP (Hypertext Transfer Protocol) request message, such as a network terminal The user clicks on the IE browser to apply to open a certain web page. After receiving the request message, the network access device determines the access location information of the network terminal user according to the information carried in the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com