USB status restriction equipment and method of use thereof
A device and state technology, applied in the field of information security, can solve problems such as leakage and loss, virus infection, flooding of sensitive information, etc., to enhance security and reduce abuse.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
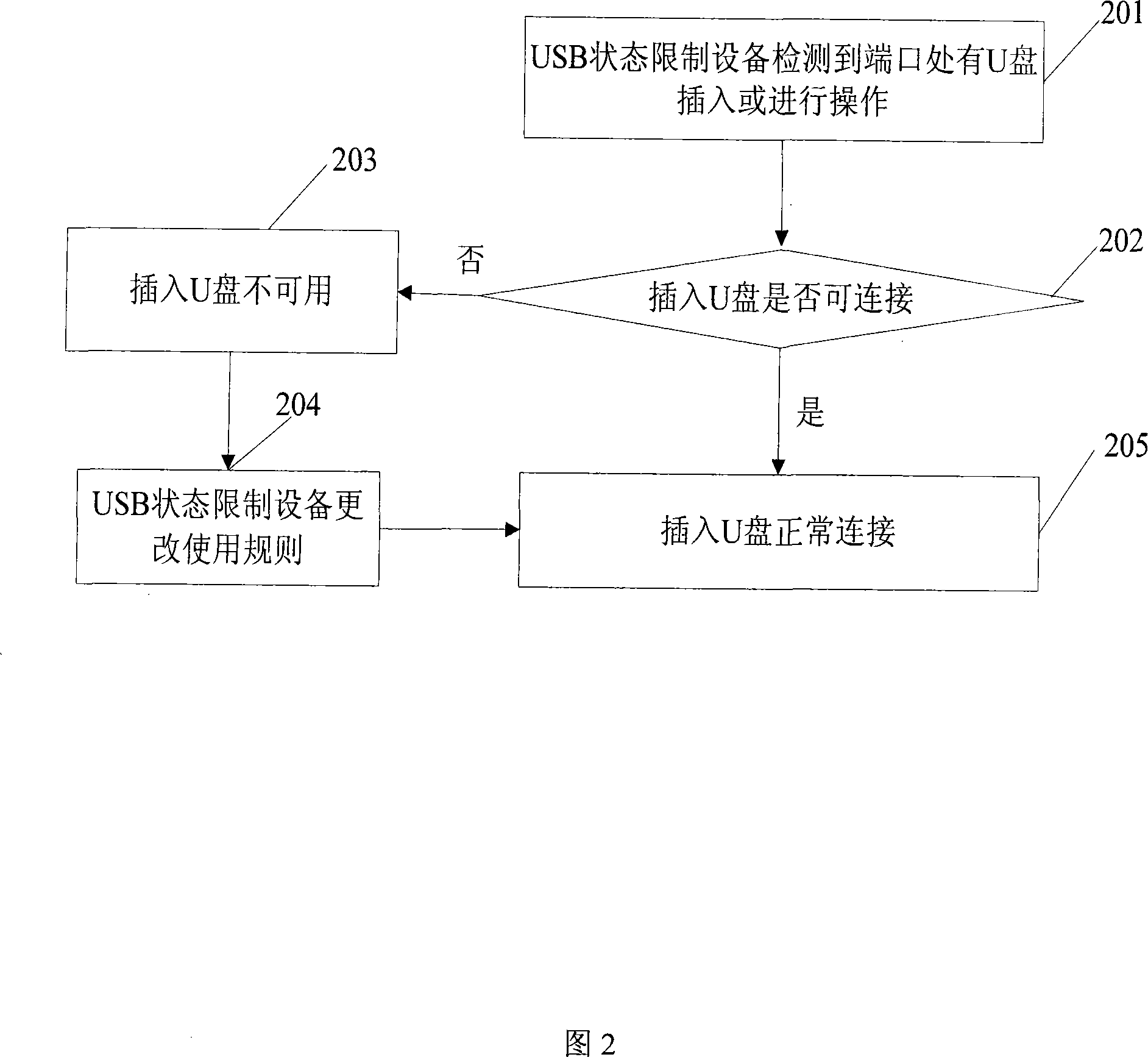
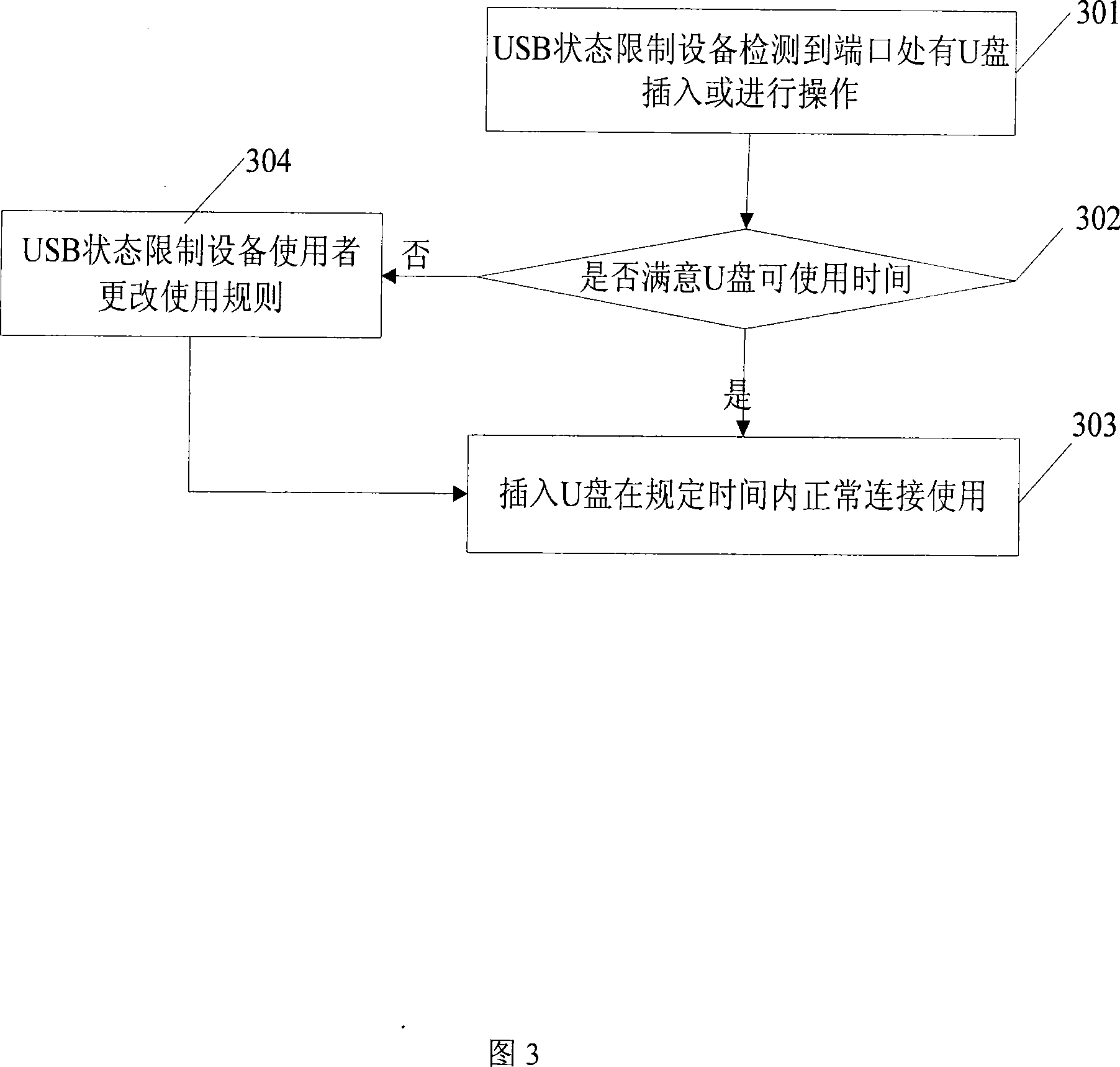
[0035] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
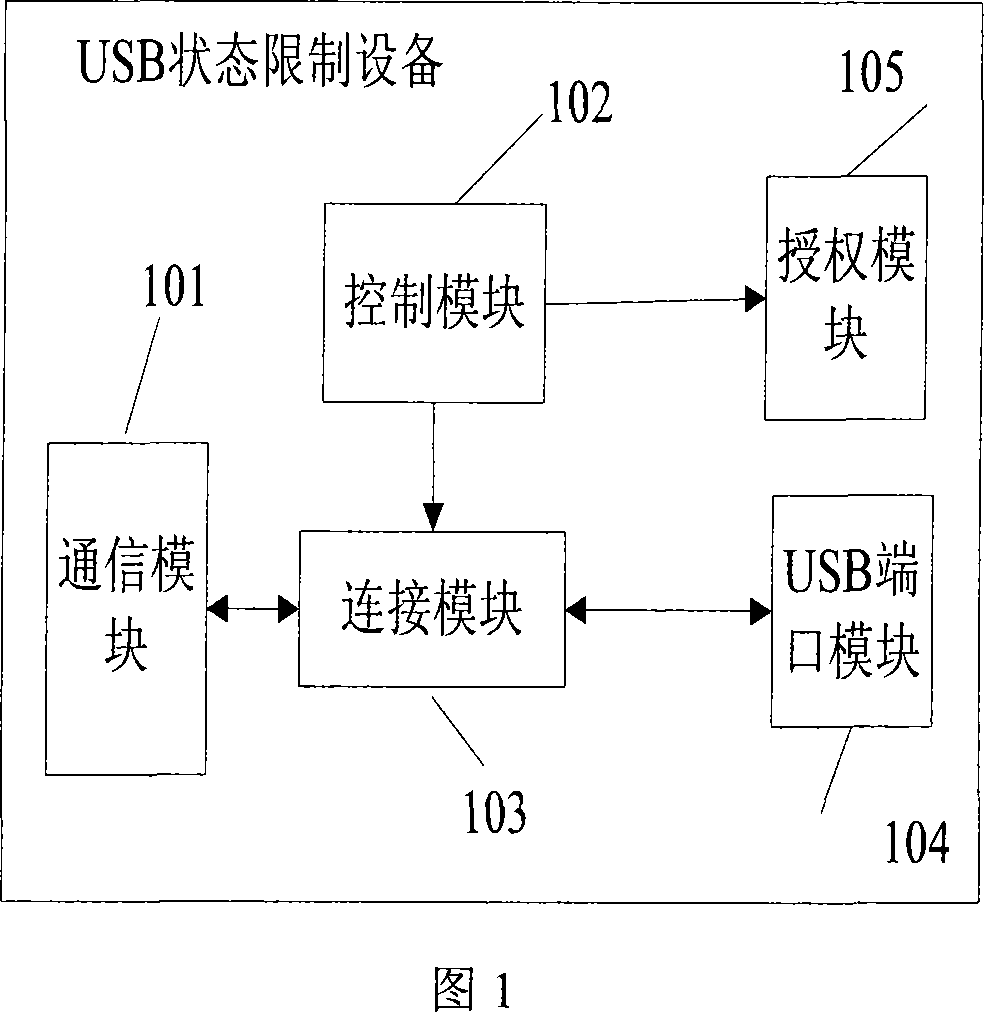
[0036] In the technical solution provided by the embodiment of the present invention, the USB state limiting device adopts the S3C4510B chip developed by Samsung for ARM7. The S3C4510B chip is a chip commonly used in the industry at present and has a USB-Host function. Thus, the USB state-limited device has a USB port, a signal line, a pull-up resistor and a pull-down resistor.
[0037] Two of the signal lines (D+ and D-) of the USB state limit device, and each signal line has a pull-down resistor of 15kΩ. USB devices such as U disks are on D+ (full-speed devices) or D- (low-speed devices). There is a 1.5kΩ pull-up resistor. When a USB device such as a U disk is inserted into a port of the USB state limiting device, the upper resistan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com