Intersect looped network, node and protecting method of random topology intersect looped network
A technology of intersecting rings and ring networks, applied in the field of Ethernet ring networks, to achieve the effect of smooth data links
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] In this embodiment, the implementation process of the present invention is described by using the first detection method.
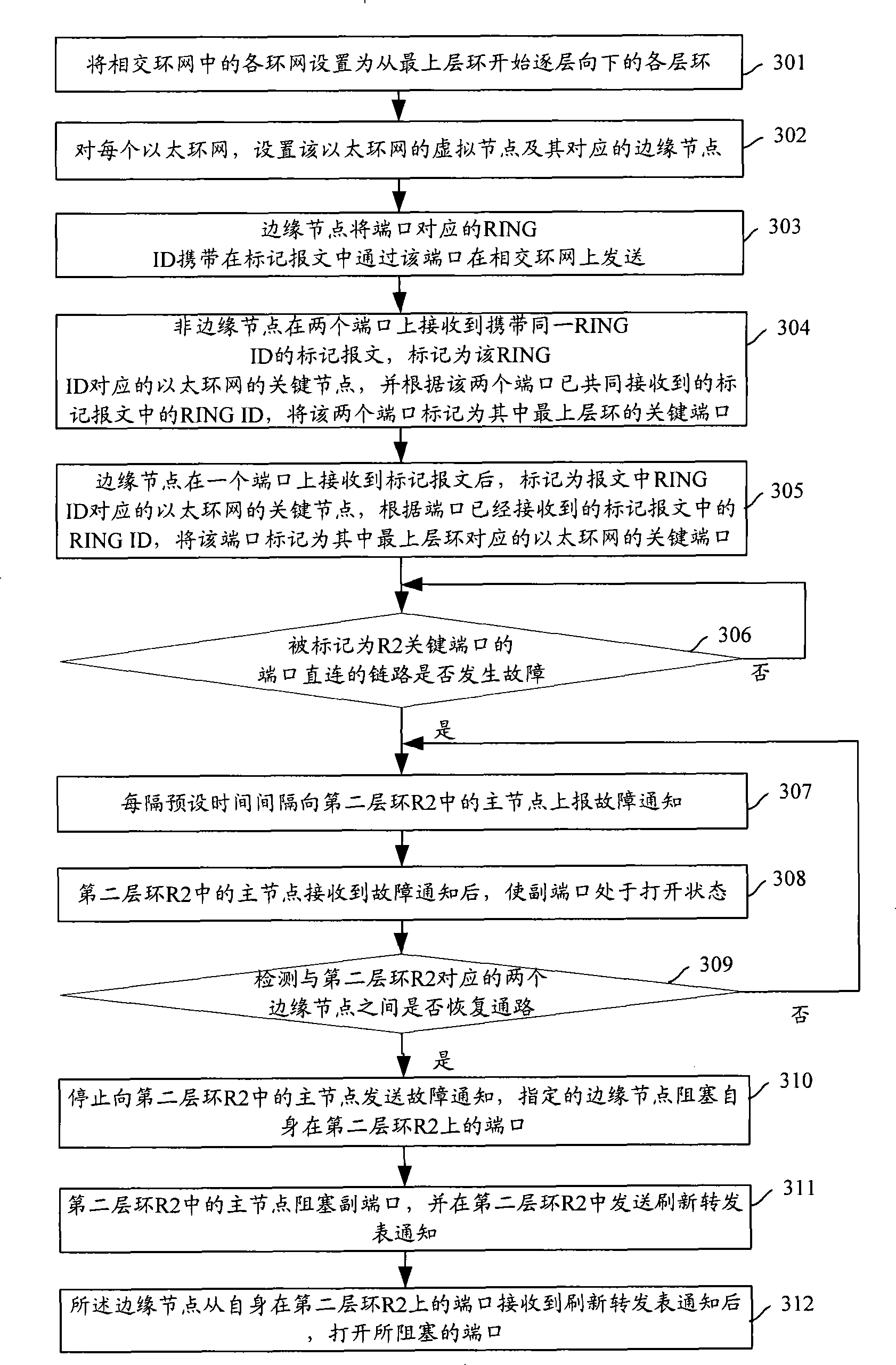
[0034] image 3 It is a flow chart of protecting an intersecting ring network of any topology in Embodiment 1 of the present invention. see image 3 , the process includes:
[0035] Step 301: For all the intersecting Ethernet ring networks, set each ring network in advance as each layer ring starting from the uppermost layer ring and descending layer by layer.
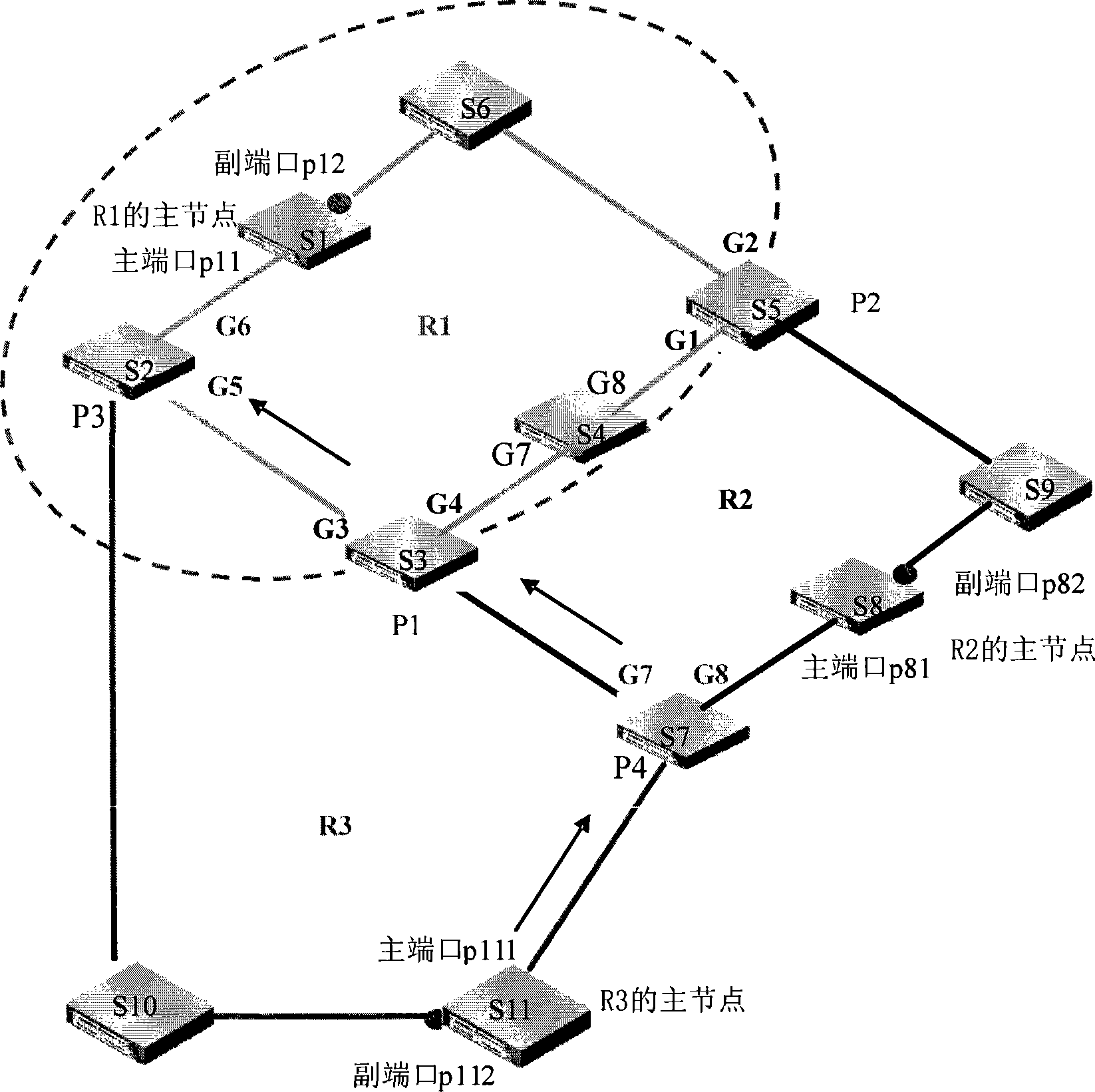
[0036] still with figure 2 The intersecting structure of three Ethernet ring networks is shown as an example. In this step 301, the Ethernet ring network R1 can be set as the first layer ring, and the Ethernet ring networks R2 and R3 can be respectively set as the second layer ring and the third layer ring. layer ring. Wherein, the first ring is the uppermost ring, and the third ring is the lowermost ring.
[0037] In specific service implementation, the upper and lower layer relatio...
Embodiment 2
[0086] In this embodiment, the implementation process of the present invention is described by using the second detection method.
[0087] Figure 7 It is a flow chart of protecting an Ethernet ring network of any topology in Embodiment 2 of the present invention. see Figure 7 , the process includes:
[0088] All descriptions of steps 701 to 702 are the same as those of steps 301 to 302.
[0089] Step 703: For two edge nodes corresponding to one Ethernet ring network, set a master edge node and an assistant edge node.
[0090] For ease of description, in the following steps, the upper layer ring R1 and the lower layer ring R2 are taken as examples to illustrate the subsequent implementation process of the present invention. For the two edge nodes corresponding to the second layer ring R2, for example, S5 may be set as the primary edge node, and S3 may be set as the auxiliary edge node.
[0091] Step 704: The main edge node S5 corresponding to the second-level ring R2 con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com