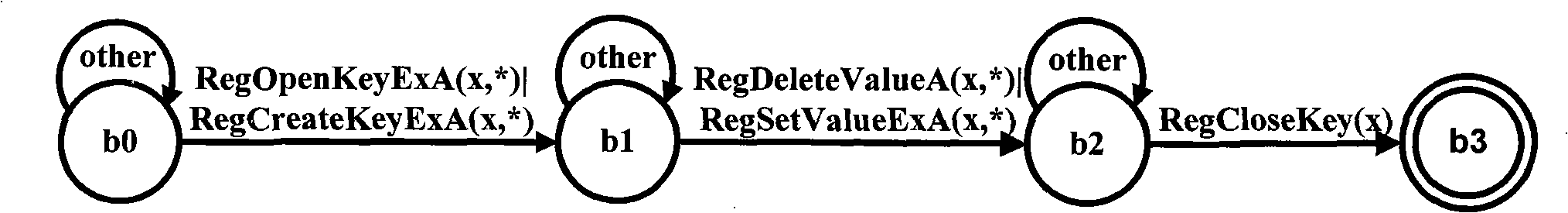Malicious code detection method
A malicious code detection and malicious code technology, applied in the fields of instrumentation, computing, electrical digital data processing, etc., can solve the problems of backwardness, easy to be bypassed, and inability to identify polymorphism or deformation of malicious code.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
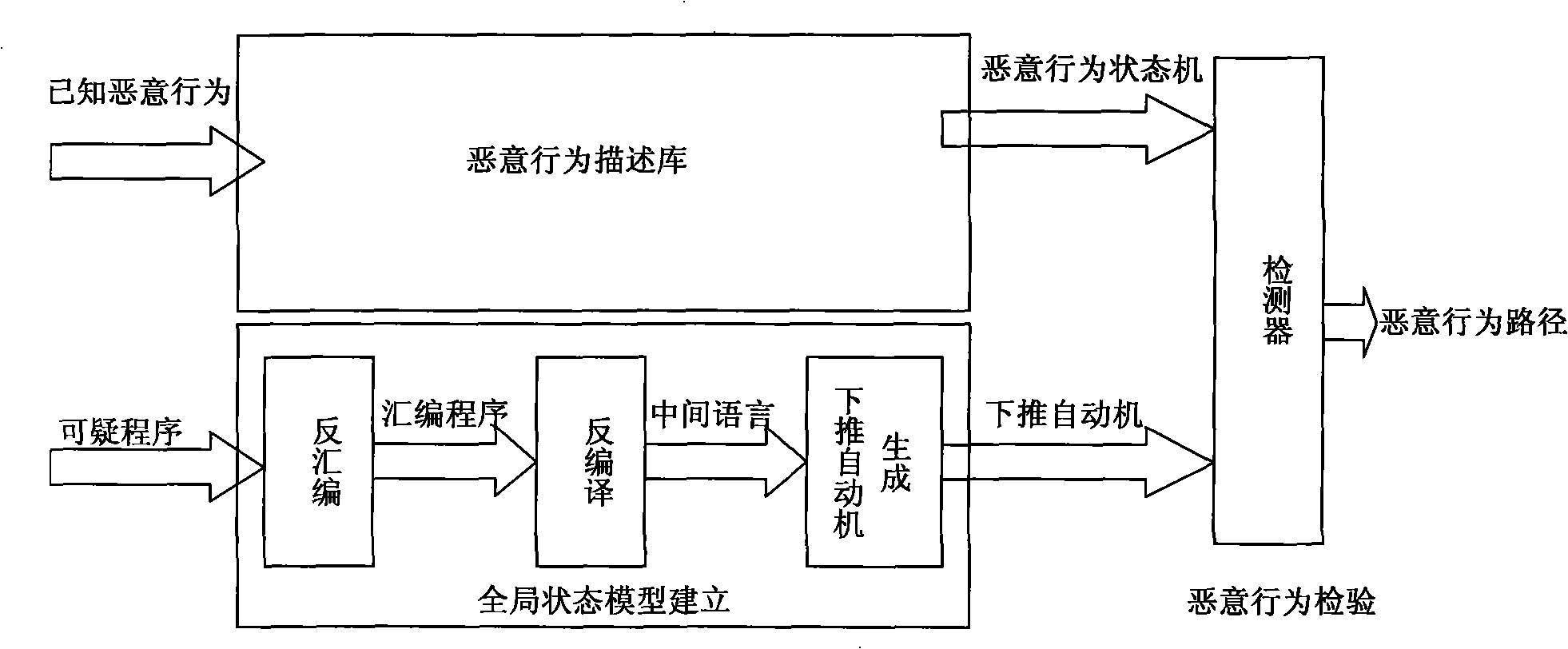
[0040] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
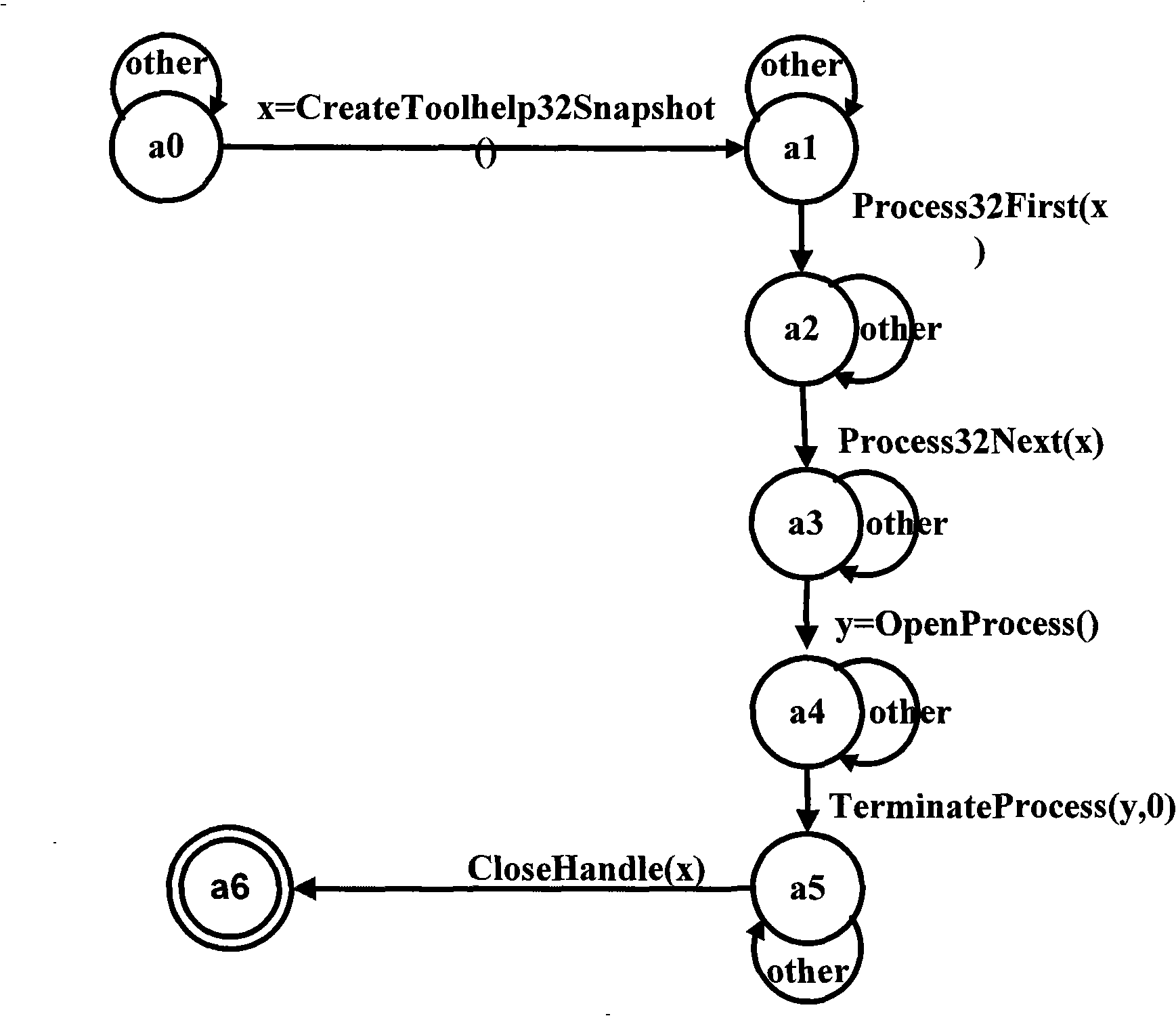
[0041] 1. Finite State Automata for Obtaining Known Malicious Behaviors
[0042] In this embodiment, by analyzing the key steps of known malicious behaviors (such as some API calls) and the timing relationship between them, judging the changes between program states, and using finite state automata to describe these malicious behaviors.
[0043] The construction process of the finite state automaton is as follows: the state of the known malicious behavior before or after each key step is taken as the state set Q, and the actions of the key steps such as API calls are used as the input alphabet A, according to the known malicious behavior The specific execution of the malicious code establishes the state transition function δ, and the state after the malicious behavior is triggered is taken as the receiving state set F, and the initial...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com