Method and devices for user authentication
A user and authentication code technology, which is applied in the direction of code identification card or credit card start-up, equipment, calculation, etc., can solve problems such as inability to establish
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
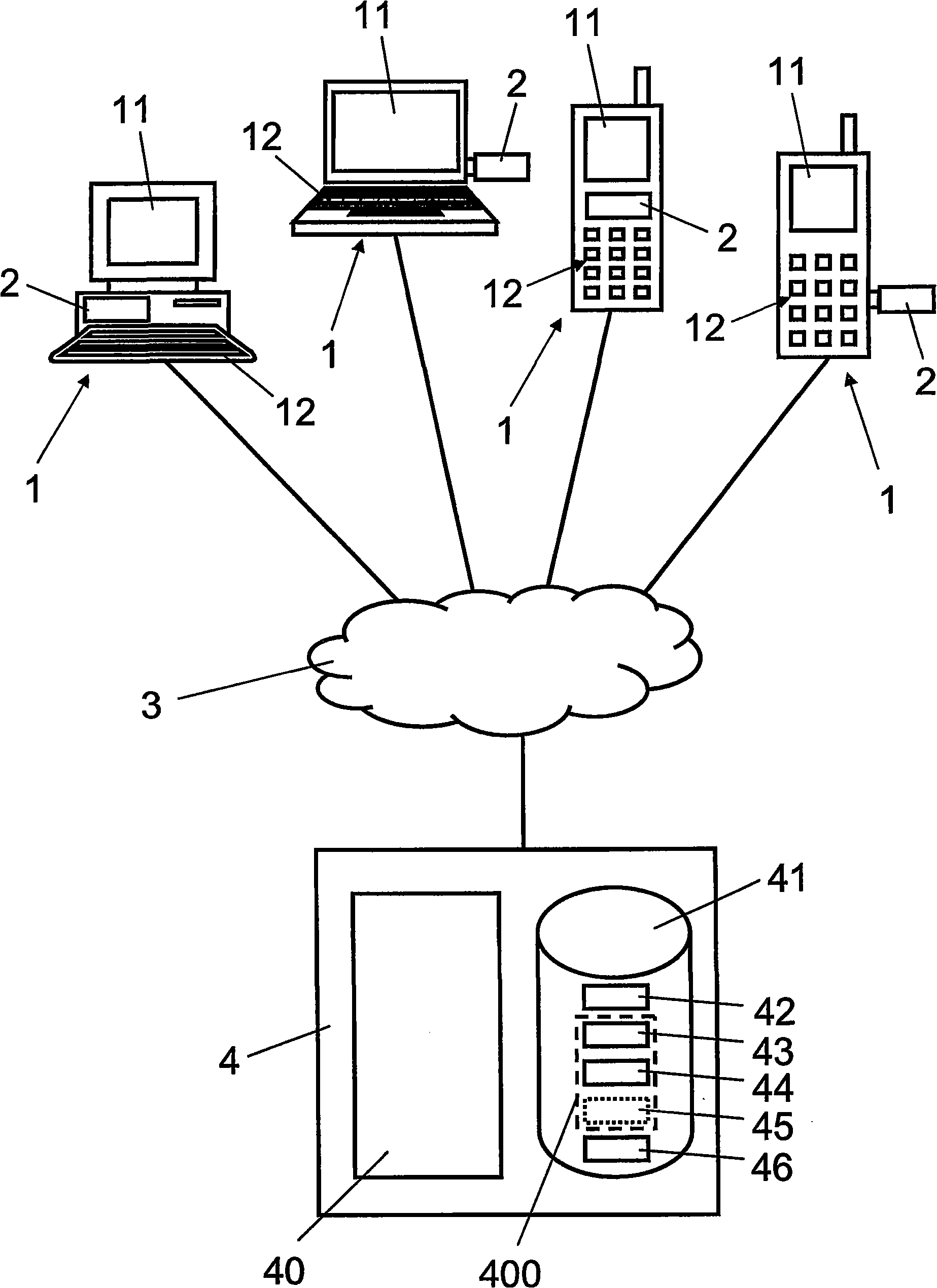
[0044] exist figure 1 Here, reference numeral 1 designates a communication terminal configured to exchange data with a computerized server 4 via a telecommunications network 3 . Communication terminals 1 include, but are not limited to, stationary personal computers (PCs), mobile laptop computers, mobile wireless telephones and / or mobile personal digital assistants (PDAs). Each communication terminal 1 has a display 11 and data input means 12, such as a keyboard and a pointing device (eg computer mouse, trackball, etc.). The communication terminal 1 comprises a client application, preferably a browser (such as Microsoft Internet Explorer or Mozilla Firefox), in order to access a server 4 residing on a server 4 via a telecommunications network 3 through a secure session established with a secure session establishment protocol such as SSL / TLS. online application. In addition, the communication terminal 1 includes an authentication module 2, which will be referred to later fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com