Method for implementing subscriber authority management based on role function mapping table
A technology of user authority and mapping table, applied in the direction of user identity/authority verification, etc., can solve the problems of prolonging the engineering cycle, complicating the system development work, and unfavorable maintenance work.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] A preferred embodiment of the present invention is as follows:
[0019] 1. Permission definition method:
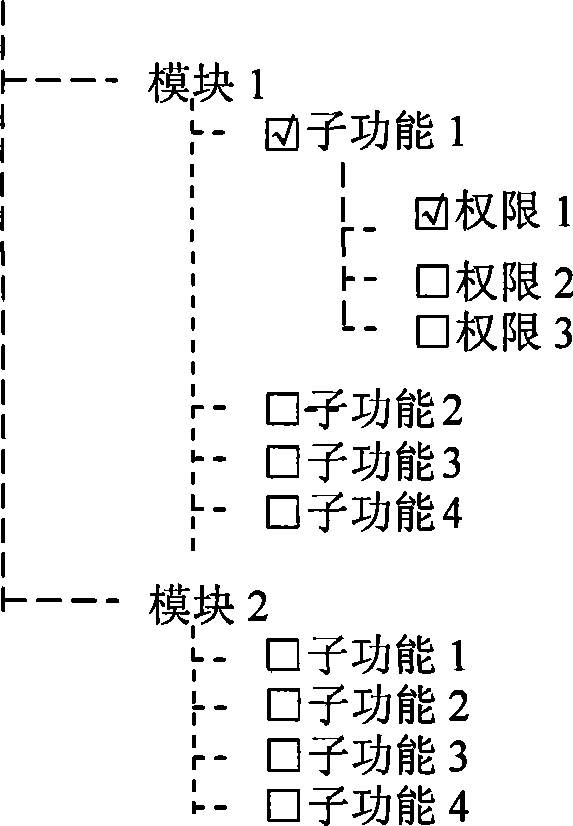
[0020] (1) Roughly divide the system functions into modules, and then subdivide various sub-functions in each module. The modules and the sub-functions in the modules define an extensible expression "module + sub-function", which is an authorized Functional objects, for the functional objects allowed to be defined by the system, form a set of functional objects of the system. When specifically applied in a computer system, assign a unique identifier to the module: a double-byte unsigned integer module_id, assign a unique identifier to the sub-function of the module: a double-byte unsigned integer subfunc_id , then the function identifier of the module sub-function in the global sense can be represented by a 4-byte unsigned integer func_id=(module_id<<16)|subfunc_id, since the double-byte unsigned integer can represent up to 65535, so the available The number of m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com