Network worm detection method and detection system
A detection method and worm technology, applied in the field of network security, can solve the problems that it is difficult to meet the requirements of large-scale high-speed network real-time detection, and the false positive rate of the worm detection method is high, so as to achieve good real-time performance and practicality, simple method, and improved accuracy sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
[0113] K 1 :E 1 → H CF 1 (H,E)
[0114] K 2 :E 2 → H CF 2 (H,E)
[0115] K 3 :E 3 ∨E 4 → H CF 3 (H,E)
[0116] K 4 :E 5 ∨E 6 → H CF 4 (H,E)
[0117] K 5 :E 7 → H CF 5 (H,E)
[0118] K 6 :E 8 → H CF 6 (H,E)
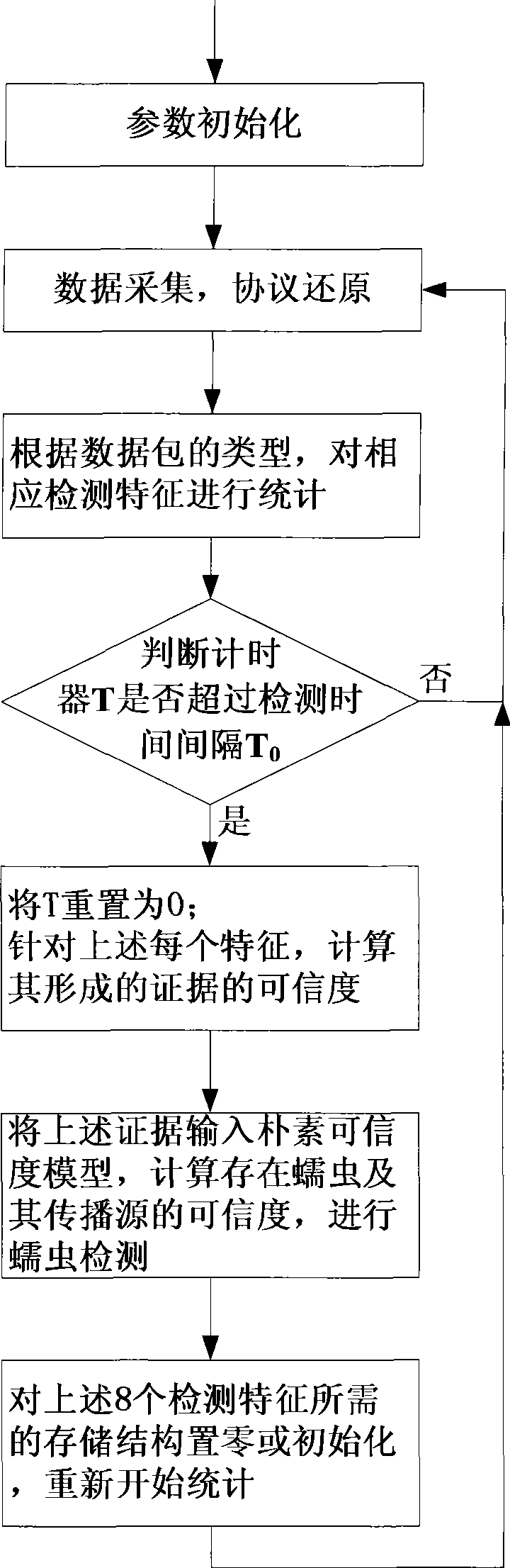
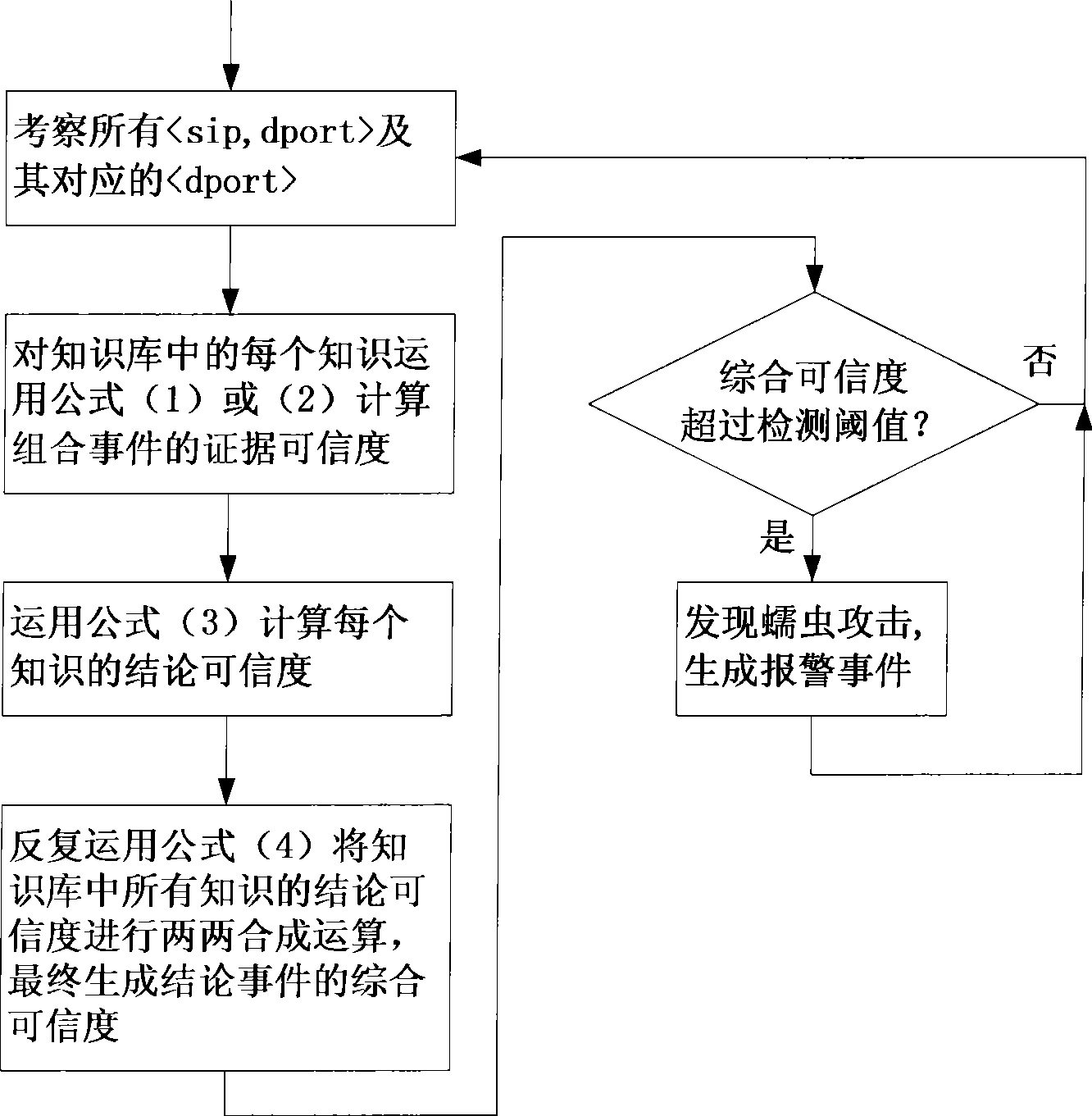
[0119] Among them, E i (i=1~8) means 8 pieces of evidence obtained from the aforementioned 8 detection features, H means the conclusion event "there is a worm attack", CF i (H, E) (i=1~6) represents the credibility of knowledge, the credibility of each knowledge is directly given by domain experts, or calculated from objective historical data through learning or training methods, its measurement principle It should be ensured that the higher the degree of support for the conclusion being true by the appearance of evidence, the greater the value of knowledge credibility. In the knowledge base, the CF i (H, E) (i=1 to 6) are known values.
[0120] The calculation formula of the credibility will not change wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com